A critical flaw in Development Software’s in MOVEit Transfer managed file transfer software has appear under prevalent exploitation in the wild to choose above vulnerable programs.
The shortcoming, which is still to be assigned a CVE identifier, relates to a serious SQL injection vulnerability that could lead to escalated privileges and possible unauthorized access to the atmosphere.
“An SQL injection vulnerability has been uncovered in the MOVEit Transfer web software that could allow an unauthenticated attacker to attain unauthorized obtain to MOVEit Transfer’s databases,” the enterprise mentioned.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Depending on the databases engine being utilized (MySQL, Microsoft SQL Server, or Azure SQL), an attacker may be equipped to infer details about the construction and contents of the database in addition to executing SQL statements that change or delete databases things.”
Patches for the bug have been produced offered by the Massachusetts-based mostly business, which also owns Telerik, in the next versions: 2021..6 (13..6), 2021.1.4 (13.1.4), 2022..4 (14..4), 2022.1.5 (14.1.5), and 2023..1 (15..1).
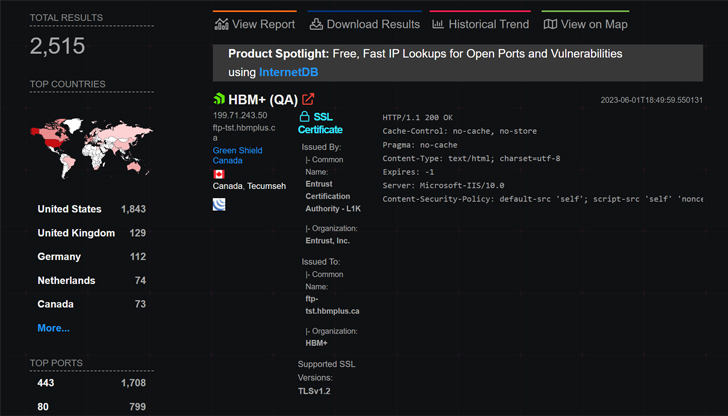
The advancement was to start with claimed by Bleeping Pc. In accordance to Huntress and Quick7, roughly 2,500 circumstances of MOVEit Transfer were exposed to the community internet as of Could 31, 2023, a vast majority of them found in the U.S.
Effective exploitation tries culminate in the deployment of a web shell, a file named “human2.aspx” in the “wwwroot” listing that is designed by means of script with a randomized filename, to “exfiltrate different info saved by the neighborhood MOVEit support.”
The web shell is also engineered to add new admin person account sessions with the name “Wellness Examine Support” in a probably effort and hard work to sidestep detection, an examination of the attack chain has discovered.
Threat intelligence business GreyNoise mentioned it “noticed scanning action for the login site of MOVEit Transfer located at /human.aspx as early as March 3, 2023,” introducing five different IP addresses have been detected “attempting to explore the area of MOVEit installations.”
Future WEBINAR 🔐 Mastering API Security: Knowledge Your Legitimate Attack Surface
Find out the untapped vulnerabilities in your API ecosystem and get proactive steps in the direction of ironclad security. Be part of our insightful webinar!
Sign up for the Session.advertisement-button,.advert-label,.advert-label:just aftershow:inline-block.ad_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px reliable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-suitable-radius:25px-moz-border-radius-bottomright:25px.advertisement-labelfont-size:13pxmargin:20px 0font-weight:600letter-spacing:.6pxcolor:#596cec.advert-label:right afterwidth:50pxheight:6pxcontent:”border-top:2px good #d9deffmargin: 8px.advert-titlefont-dimensions:21pxpadding:10px 0font-weight:900text-align:leftline-top:33px.advert-descriptiontextual content-align:leftfont-dimensions:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.advertisement-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-measurement:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-bodyweight:500letter-spacing:.2px
“When we you should not know the specifics close to the group guiding the zero working day attacks involving MOVEit, it underscores a worrisome development of risk actors targeting file transfer options,” Satnam Narang, senior staff analysis engineer at Tenable, claimed.
The development has prompted the U.S. Cybersecurity and Infrastructure Security Company (CISA) to issue an alert, urging customers and corporations to observe the mitigation techniques to secure against any malicious exercise.
It can be also recommended to isolate the servers by blocking inbound and outbound traffic and examine the environments for feasible indicators of compromise (IoCs), and if so, delete them just before making use of the fixes.
“If it turns out to be a ransomware team again this will be the second company MFT zero working day in a calendar year, cl0p went wild with GoAnywhere not long ago,” security researcher Kevin Beaumont said.
Identified this report attention-grabbing? Follow us on Twitter and LinkedIn to examine extra exceptional material we post.
Some sections of this article are sourced from:
thehackernews.com


 Horabot Campaign Targets Spanish-Speaking Users in the Americas
Horabot Campaign Targets Spanish-Speaking Users in the Americas