Cybersecurity researchers have made available a nearer search at the RokRAT remote entry trojan which is utilized by the North Korean point out-sponsored actor acknowledged as ScarCruft.
“RokRAT is a advanced remote entry trojan (RAT) that has been observed as a critical ingredient in the attack chain, enabling the danger actors to achieve unauthorized entry, exfiltrate delicate facts, and probably keep persistent manage over compromised programs,” ThreatMon mentioned.
ScarCruft, lively because at minimum 2012, is a cyber espionage group that operates on behalf of the North Korean federal government, completely concentrating on targets in its southern counterpart.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The team is believed to be a subordinate aspect inside of North Korea’s Ministry of Condition Security (MSS). Attack chains mounted by the group have leaned intensely on social engineering to spear-phish victims and provide payloads onto goal networks.
This features exploiting vulnerabilities in Hancom’s Hangul Word Processor (HWP), a efficiency application broadly applied by community and non-public organizations in South Korea, to produce its signature malware dubbed RokRAT.
The Windows backdoor, also called DOGCALL, is actively made and taken care of, and has due to the fact been ported to other running systems this kind of as macOS and Android.
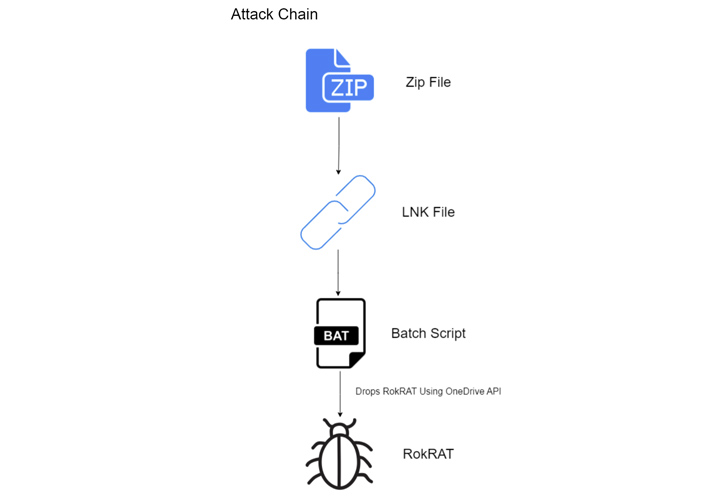
The latest spear-phishing attacks, as evidenced by the AhnLab Security Unexpected emergency response Middle (ASEC) and Verify Place, have made use of LNK data files to set off multi-stage an infection sequences that eventually result in the deployment of the RokRAT malware.
Impending WEBINAR Zero Believe in + Deception: Find out How to Outsmart Attackers!
Uncover how Deception can detect superior threats, halt lateral movement, and enrich your Zero Rely on system. Be part of our insightful webinar!
Preserve My Seat!.advert-button,.advert-label,.advertisement-label:right afterdisplay:inline-block.advertisement_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px sound #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-suitable-radius:25px-moz-border-radius-bottomright:25px.ad-labelfont-size:13pxmargin:20px 0font-excess weight:600letter-spacing:.6pxcolor:#596cec.advertisement-label:immediately afterwidth:50pxheight:6pxcontent:”border-top:2px sound #d9deffmargin: 8px.advert-titlefont-size:21pxpadding:10px 0font-fat:900textual content-align:leftline-top:33px.advert-descriptiontextual content-align:leftfont-sizing:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.advertisement-buttonpadding:6px 12pxborder-radius:5pxbackground-color:#4469f5font-size:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-excess weight:500letter-spacing:.2px
RokRAT permits the adversary to harvest procedure metadata, get screenshots, execute arbitrary commands received from a distant server, enumerate directories, and exfiltrate data files of desire.
The development will come as ASEC disclosed a ScarCruft attack that leverages a Windows executable masquerading as a Hangul doc to fall malware that is configured to get hold of an external URL every single 60 minutes.
“The URL registered in the job scheduler appears to be a ordinary homepage, but it incorporates a web shell,” ASEC pointed out.
Observed this article attention-grabbing? Comply with us on Twitter and LinkedIn to go through extra distinctive content material we publish.
Some parts of this posting are sourced from:
thehackernews.com


 Active Mirai Botnet Variant Exploiting Zyxel Devices for DDoS Attacks
Active Mirai Botnet Variant Exploiting Zyxel Devices for DDoS Attacks