Cybersecurity scientists now uncovered a new pressure of banking malware that targets not only banking apps but also steals details and qualifications from social networking, relationship, and cryptocurrency apps—in full 337 non-monetary Android purposes on it is really concentrate on listing.
Dubbed “BlackRock” by ThreatFabric scientists, which uncovered the trojan in May perhaps, its source code is derived from a leaked model of Xerxes banking malware, which alone is a strain of the LokiBot Android banking trojan that was first noticed throughout 2016-2017.
Chief between its capabilities are thieving consumer qualifications, intercepting SMS messages, hijacking notifications, and even recording keystrokes from the qualified apps, in addition to being capable of hiding from antivirus software package.
“Not only did the [BlackRock] Trojan go through adjustments in its code, but also will come with an improved focus on record and has been ongoing for a extended period,” ThreatFabric explained.
“It consists of an critical amount of social, networking, interaction and courting applications [that] have not been observed in target lists for other present banking Trojans.”
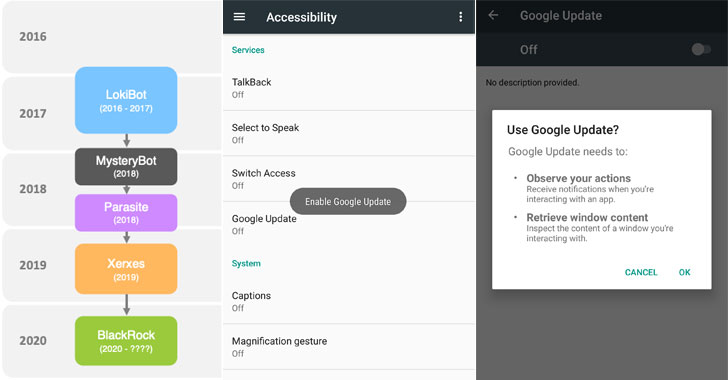
BlackRock does the information assortment by abusing Android’s Accessibility Provider privileges, for which it seeks users’ permissions below the guise of bogus Google updates when it can be introduced for the initially time on the gadget, as proven in the shared screenshots.
Subsequently, it goes on to grant itself extra permissions and create a link with a distant command-and-handle (C2) server to carry out its malicious activities by injecting overlays atop the login and payment screens of the focused apps.
These credential-thieving overlays have been uncovered on banking apps running in Europe, Australia, the US, and Canada, as perfectly as procuring, communication, and business enterprise apps.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
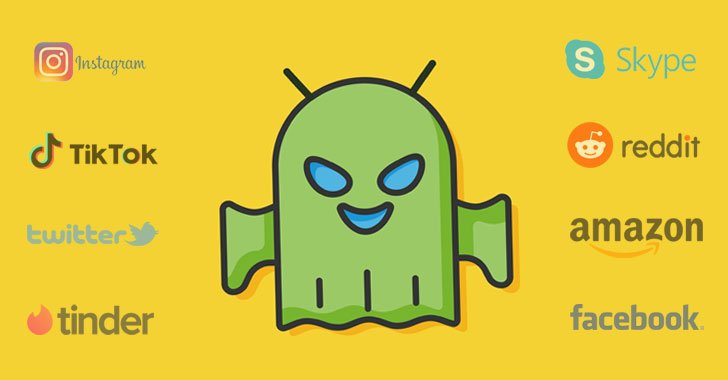
“The target list of non-economical applications is made up of famous applications these kinds of as but not minimal to Tinder, TikTok, PlayStation, Facebook, Instagram, Skype, Snapchat, Twitter, Grinder, VK, Netflix, Uber, eBay, Amazon, Reddit and Tumblr,” the scientists told The Hacker Information.
This is not the initial time mobile malware has abused Android’s accessibility functions.
Earlier this calendar year, IBM X-Power scientists specific a new TrickBot marketing campaign, known as TrickMo, that was observed exclusively targeting German buyers with malware that misused accessibility characteristics to intercept one particular-time passwords (OTP), cellular TAN (mTAN), and pushTAN authentication codes.
Then in April, Cybereason uncovered a diverse class of banking malware identified as EventBot that leveraged the same characteristic to exfiltrate delicate knowledge from fiscal programs, go through person SMS messages, and hijack SMS-centered two-aspect authentication codes.
What can make BlackRock’s campaign distinctive is the sheer breadth of the applications specific, which go beyond the cell banking apps that are ordinarily targeted.
“Just after Alien, Eventbot, and BlackRock we can expect that economically motivated risk actors will construct new banking Trojans and go on improving upon the present kinds,” ThreatFabric scientists concluded.
“With the modifications that we hope to be designed to cellular banking Trojans, the line between banking malware and adware results in being thinner, [and] banking malware will pose a menace for more corporations.”
Located this write-up attention-grabbing? Observe THN on Facebook, Twitter and LinkedIn to read more exceptional content material we article.

 A New Flaw In Zoom Could Have Let Fraudsters Mimic Organisations
A New Flaw In Zoom Could Have Let Fraudsters Mimic Organisations