Researchers have exposed a new qualified email campaign aimed at French entities in the building, genuine estate, and governing administration sectors that leverages the Chocolatey Windows package deal manager to deliver a backdoor termed Serpent on compromised programs.
Enterprise security agency Proofpoint attributed the attacks to a probable innovative menace actor centered on the methods and the victimology designs observed. The final aim of the campaign stays presently mysterious.
“The threat actor attempted to set up a backdoor on a likely victim’s device, which could enable remote administration, command and control (C2), knowledge theft, or supply other supplemental payloads,” Proofpoint scientists explained in a report shared with The Hacker News.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

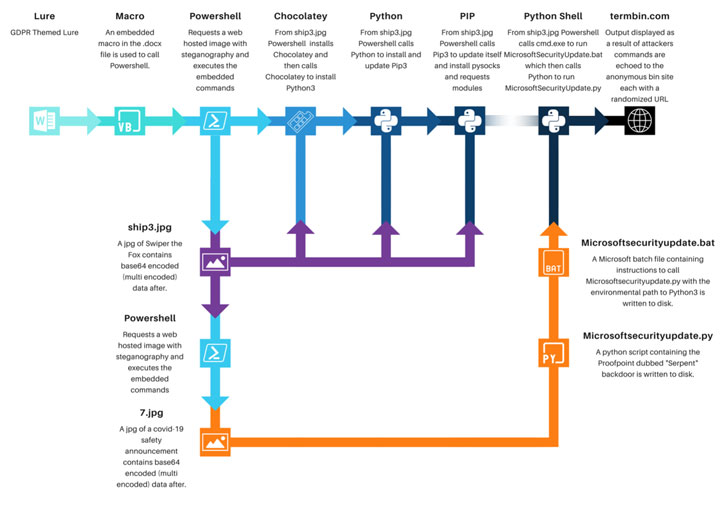
The phishing lure that triggers the an infection sequence helps make use of a resume-themed subject line, with the attached macro-embedded Microsoft Phrase document masquerading as facts similar to the European Union’s Common Facts Protection Regulation (GDPR).
Enabling the macros results in its execution, which retrieves a seemingly harmless picture file hosted on a distant server but really consists of a Base64-encoded PowerShell script which is obscured applying steganography, a minor-applied approach of concealing malicious code inside an graphic or audio in get to circumvent detection.
The PowerShell script, in switch, is engineered to set up the Chocolatey utility on the Windows device, which is then utilized to put in the Python deal installer pip, the latter of which acts as conduit to set up the PySocks proxy library.
Also retrieved by the exact same PowerShell script is a different graphic file from the identical remote server that consists of the camouflaged Python backdoor dubbed Serpent, which comes with capabilities to execute instructions transmitted from the C2 server.
In addition to steganography, the use of broadly identified equipment these types of as Chocolatey as an original payload for comply with-on deployment of real Python offers is an attempt to stay underneath the radar and not be flagged as a danger, Proofpoint said.
The attacks have not unearthed associations with a formerly identified actor or group, but are suspected to be the do the job of a innovative hacking crew.
“This is a novel application of a selection of technologies that are typically legitimately employed within companies,” Sherrod DeGrippo, vice president of risk research and detection at Proofpoint, mentioned in a statement.
“It capitalizes on lots of organizations’, especially technical teams, need to allow their end users to be ‘self-sufficient’ in regards to self-tooling and package deal professionals. Also, the use of steganography is unconventional and a thing we you should not see consistently.”
Uncovered this post attention-grabbing? Follow THN on Fb, Twitter and LinkedIn to examine far more exceptional information we publish.
Some areas of this post are sourced from:
thehackernews.com


 ‘CryptoRom’ Crypto Scam Abusing iPhone Features to Target Mobile Users
‘CryptoRom’ Crypto Scam Abusing iPhone Features to Target Mobile Users