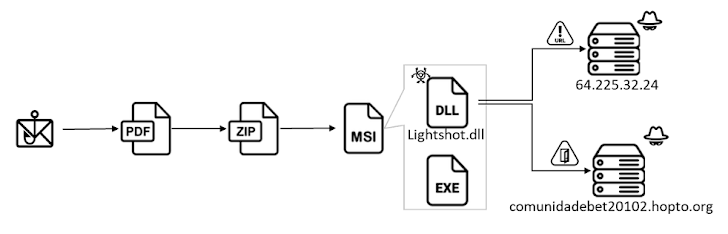
End users in Brazil are the target of a new banking trojan acknowledged as CHAVECLOAK which is propagated by using phishing e-mail bearing PDF attachments.
“This intricate attack will involve the PDF downloading a ZIP file and subsequently making use of DLL side-loading procedures to execute the closing malware,” Fortinet FortiGuard Labs researcher Cara Lin claimed.
The attack chain requires the use of agreement-themed DocuSign lures to trick consumers into opening PDF data files made up of a button to read through and indicator the paperwork.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
In fact, clicking the button leads to the retrieval of an installer file from a remote hyperlink which is shortened applying the Goo.su URL shortening support.
Current inside the installer is an executable named “Lightshot.exe” that leverages DLL aspect-loading to load “Lightshot.dll,” which is the CHAVECLOAK malware that facilitates the theft of sensitive data.
This contains accumulating technique metadata and functioning checks to decide no matter whether the compromised machine is situated in Brazil and, if so, periodically monitoring the foreground window to compare it in opposition to a predefined listing of bank-related strings.

If it matches, a relationship is founded with a command-and-handle (C2) server and proceeds to harvest a variety of forms of information and facts and exfiltrate them to unique endpoints on the server based on the economical institution.
“The malware facilitates many steps to steal a victim’s qualifications, these types of as making it possible for the operator to block the victim’s display screen, log keystrokes, and screen misleading pop-up windows,” Lin reported.
“The malware actively screens the victim’s obtain to specific economic portals, like numerous financial institutions and Mercado Bitcoin, which encompasses equally common banking and cryptocurrency platforms.”
Fortinet mentioned it also uncovered a Delphi variant of CHAVECLOAK, the moment once more highlighting the prevalence of Delphi-based mostly malware targeting Latin The usa.
“The emergence of the CHAVECLOAK banking Trojan underscores the evolving landscape of cyberthreats concentrating on the monetary sector, specifically concentrating on consumers in Brazil,” Lin concluded.
The findings occur amid an ongoing cell banking fraud marketing campaign from the U.K., Spain, and Italy that entails employing smishing and vishing (i.e., SMS and voice phishing) strategies to deploy an Android malware termed Copybara with the goal of carrying out unauthorized banking transfers to a network of bank accounts operated by dollars mules.
“TAs [Threat actors] have been caught employing a structured way of controlling all the ongoing phishing campaigns by way of a centralized web panel recognised as ‘Mr. Robot,'” Cleafy mentioned in a report published very last 7 days.
“With this panel, TAs can empower and handle numerous phishing campaigns (in opposition to distinctive money establishments) based mostly on their demands.”
The C2 framework also permits attackers to orchestrate tailored attacks on distinct monetary establishments using phishing kits that are engineered to mimic the consumer interface of the qualified entity, when also adopting anti-detection techniques by using geofencing and product fingerprinting to limit connections only from cellular products.
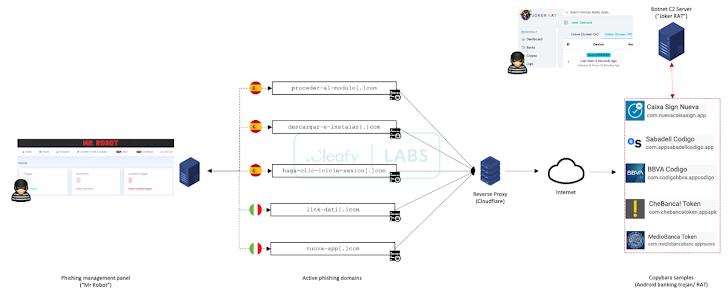
The phishing package – which serves as a faux login webpage – is liable for capturing retail banking customer credentials and phone quantities and sending the aspects to a Telegram team.
Some of the malicious infrastructure utilized for the campaign is made to supply Copybara, which is managed making use of a C2 panel named JOKER RAT that displays all the infected devices and their geographical distribution about a reside map.
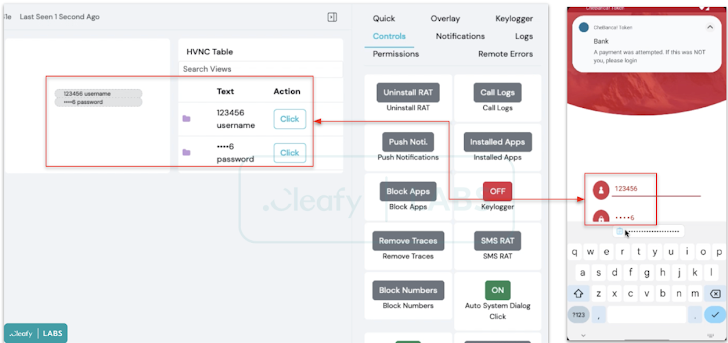
It also makes it possible for the danger actors to remotely interact in real-time with an infected system employing a VNC module, in addition to injecting phony overlays on leading of banking applications to siphon credentials, logging keystrokes by abusing Android’s accessibility providers, and intercepting SMS messages.

On prime of that, JOKER RAT comes with an APK builder that tends to make it attainable to customize the rogue app’s identify, offer title, and icons.
“Yet another characteristic obtainable inside the panel is the ‘Push Notification,’ most likely utilized to send out to the contaminated products bogus drive notifications that search like a financial institution notification to entice the person to open up the bank’s application in this kind of a way that the malware can steal credentials,” Cleafy scientists Francesco Iubatti and Federico Valentini claimed.
The increasing sophistication of on-unit fraud (ODF) strategies is even further evidenced by a lately disclosed TeaBot (aka Anatsa) campaign that managed to infiltrate the Google Engage in Retailer under the guise of PDF reader apps.
“This application serves as a dropper, facilitating the download of a banking trojan of the TeaBot family by a number of stages,” Iubatti said. “Right before downloading the banking trojan, the dropper performs state-of-the-art evasion approaches, together with obfuscation and file deletion, along with numerous checks about the victim international locations.”
Located this post exciting? Adhere to us on Twitter and LinkedIn to read far more unique written content we article.
Some areas of this article are sourced from:
thehackernews.com

 Data Leakage Prevention in the Age of Cloud Computing: A New Approach
Data Leakage Prevention in the Age of Cloud Computing: A New Approach