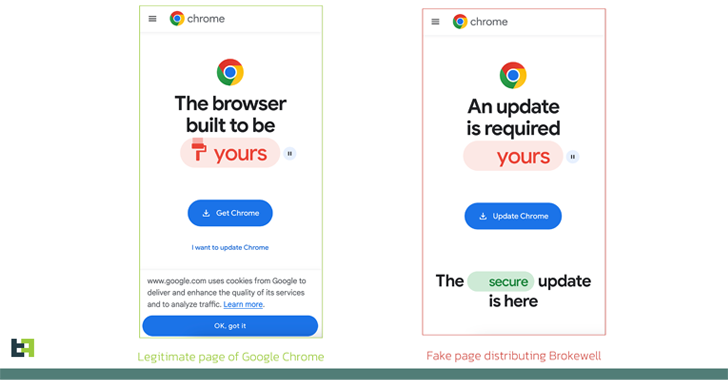
Bogus browser updates are remaining applied to push a previously undocumented Android malware identified as Brokewell.
“Brokewell is a usual contemporary banking malware equipped with both of those data-thieving and remote-command abilities crafted into the malware,” Dutch security firm ThreatFabric reported in an evaluation revealed Thursday.
The malware is mentioned to be in energetic enhancement, incorporating new instructions to capture touch events, textual information shown on monitor, and the apps a sufferer launches.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The record of Brokewell apps that masquerade as Google Chrome, ID Austria, and Klarna is as follows –
- jcwAz.EpLIq.vcAZiUGZpK (Google Chrome)
- zRFxj.ieubP.lWZzwlluca (ID Austria)
- com.brkwl.upstracking (Klarna)
Like other current Android malware households of its kind, Brokewell is able of receiving close to limitations imposed by Google that prevent sideloaded applications from requesting accessibility services permissions.

The banking trojan, when set up and launched for the initially time, prompts the sufferer to grant permissions to the accessibility services, which it subsequently takes advantage of to immediately grant other permissions and have out different malicious things to do.
This includes displaying overlay screens on top rated of targeted apps to pilfer user credentials. It can also steal cookies by launching a WebView and loading the reputable web-site, right after which the session cookies are intercepted and transmitted to an actor-managed server.

Some of the other characteristics of Brokewell contain the capability to record audio, take screenshots, retrieve call logs, access product spot, checklist set up applications, report just about every every event occurring on the gadget, ship SMS messages, do phone phone calls, set up and uninstall apps, and even disable the accessibility service.
The danger actors can also leverage the malware’s remote control performance to see what is shown on display in authentic-time, as very well as interact with the gadget as a result of clicks, swipes, and touches.
Brokewell is explained to be the operate of a developer who goes by the name “Baron Samedit Marais” and manages the “Brokewell Cyber Labs” task, which also consists of an Android Loader publicly hosted on Gitea.

The loader is built to act as a dropper that bypasses accessibility permissions limitations in Android variations 13, 14, and 15 applying a strategy beforehand adopted by dropper-as-a-provider (DaaS) choices like SecuriDropper and deploy the trojan implant.
By default, the loader applications produced as a result of this approach have the package identify “com.brkwl.apkstore,” whilst this can configured by the consumer by possibly offering a unique title or enabling the random package deal identify generator.
The absolutely free availability of the loader means it could be embraced by other threat actors wanting to sidestep Android’s security protections.
“Second, present ‘Dropper-as-a-Service’ offerings that currently provide this capacity as a exclusive aspect will probably possibly shut their providers or attempt to reorganize,” ThreatFabric reported.
“This further more lowers the entry barrier for cybercriminals seeking to distribute cellular malware on fashionable gadgets, generating it a lot easier for a lot more actors to enter the field.”
Observed this short article appealing? Comply with us on Twitter and LinkedIn to go through a lot more exclusive articles we put up.
Some components of this posting are sourced from:
thehackernews.com

 Palo Alto Networks Outlines Remediation for Critical PAN-OS Flaw Under Attack
Palo Alto Networks Outlines Remediation for Critical PAN-OS Flaw Under Attack