A new pressure of destructive application that’s engineered to penetrate and disrupt critical programs in industrial environments has been unearthed.
Google-owned risk intelligence agency Mandiant dubbed the malware COSMICENERGY, adding it was uploaded to a community malware scanning utility in December 2021 by a submitter in Russia. There is no proof that it has been place to use in the wild.
“The malware is designed to bring about electric powered electricity disruption by interacting with IEC 60870-5-104 (IEC-104) products, such as remote terminal models (RTUs), that are typically leveraged in electric powered transmission and distribution operations in Europe, the Middle East, and Asia,” the business mentioned.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
COSMICENERGY is the most recent addition to specialised malware like Stuxnet, Havex, Triton, IRONGATE, BlackEnergy2, Industroyer, and PIPEDREAM, which are capable of sabotaging critical methods and wreaking havoc.
Mandiant mentioned that there are circumstantial back links that it might have been created as a crimson teaming software by Russian telecom firm Rostelecom-Photo voltaic to simulate energy disruption and crisis response workouts that had been held in October 2021.
This raises the likelihood that the malware was possibly designed to recreate sensible attack scenarios in opposition to vitality grid assets to exam defenses or a further party reused code related with the cyber selection.
The next substitute is not unheard of, especially in light of the simple fact that threat actors are known to adapt and repurpose legit crimson crew and post-exploitation instruments for malicious ends.
COSMICENERGY’s attributes are comparable to that of Industroyer – which has been attributed to the Kremlin-backed Sandworm team – owing to its capability to exploit an industrial communication protocol referred to as IEC-104 to issue commands to RTUs.
“Leveraging this accessibility, an attacker can mail distant commands to have an impact on the actuation of power line switches and circuit breakers to bring about electrical power disruption,” Mandiant claimed.
Impending WEBINARZero Believe in + Deception: Learn How to Outsmart Attackers!
Uncover how Deception can detect highly developed threats, cease lateral motion, and improve your Zero Have confidence in approach. Be part of our insightful webinar!
Conserve My Seat!
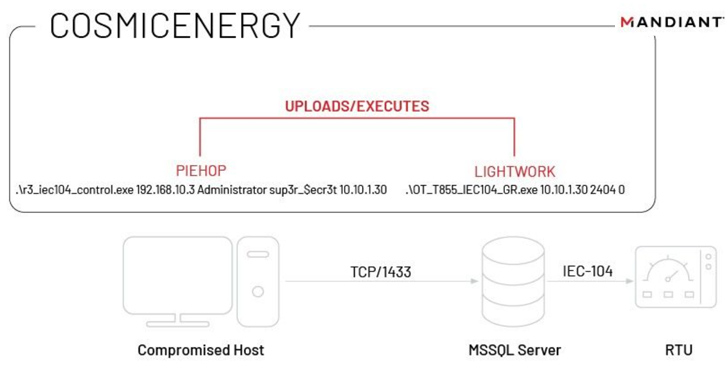
This is completed by signifies of two parts named PIEHOP and LIGHTWORK, which are two disruption equipment penned in Python and C++, respectively, to transmit the IEC-104 commands to the connected industrial products.
A different noteworthy facet of the industrial command system (ICS) malware is the lack of intrusion and discovery abilities, which means it calls for the operator to accomplish an inner reconnaissance of the network to decide the IEC-104 unit IP addresses to be targeted.
To pull off an attack, a risk actor would thus have to infect a computer within just the network, uncover a Microsoft SQL Server that has obtain to the RTUs, and receive its credentials.
PIEHOP is then operate on the equipment to add LIGHTWORK to the server, which sends disruptive remote instructions to modify the condition of the units (ON or OFF) around TCP. It also quickly deletes the executable following issuing the guidance.
“Even though COSMICENERGY’s abilities are not significantly distinctive from prior OT malware families’, its discovery highlights many notable developments in the OT danger landscape,” Mandiant mentioned.
“The discovery of new OT malware offers an rapid menace to influenced organizations, due to the fact these discoveries are scarce and because the malware principally takes benefit of insecure by design and style capabilities of OT environments that are unlikely to be remedied any time shortly.”
Found this short article fascinating? Stick to us on Twitter and LinkedIn to read through much more distinctive content material we submit.
Some elements of this write-up are sourced from:
thehackernews.com


 Barracuda Warns of Zero-Day Exploited to Breach Email Security Gateway Appliances
Barracuda Warns of Zero-Day Exploited to Breach Email Security Gateway Appliances