Cybersecurity researchers have uncovered the 1st-ever illicit cryptocurrency mining marketing campaign used to mint Dero considering that the get started of February 2023.
“The novel Dero cryptojacking procedure concentrates on locating Kubernetes clusters with nameless obtain enabled on a Kubernetes API and listening on non-normal ports accessible from the internet,” CrowdStrike mentioned in a new report shared with The Hacker News.
The development marks a notable change from Monero, which is a commonplace cryptocurrency employed in these campaigns. It really is suspected it could have to do with the point that Dero “offers bigger benefits and presents the similar or superior anonymizing functions.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The attacks, attributed to an mysterious fiscally enthusiastic actor, commence with scanning for Kubernetes clusters with authentication set as –nameless-auth=legitimate, which permits anonymous requests to the server, to fall first payloads from a few various U.S.-centered IP addresses.
This consists of deploying a Kubernetes DaemonSet named “proxy-api,” which, in convert, is utilized to drop a malicious pod on every single node of the Kubernetes cluster to kick-commence the mining exercise.
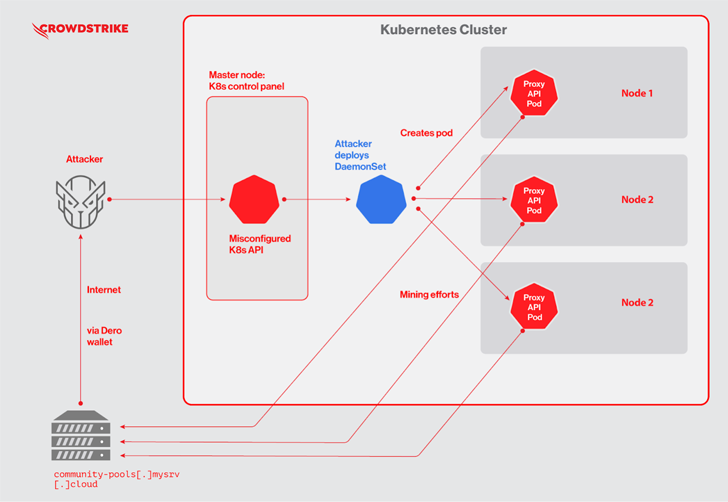
To that stop, the DaemonSet’s YAML file is orchestrated to run a Docker impression that contains a “pause” binary, which is really the Dero coin miner.
“In a legitimate Kubernetes deployment, ‘pause’ containers are utilised by Kubernetes to bootstrap a pod,” the enterprise observed. “Attackers may perhaps have employed this identify to blend in to prevent evident detection.”
WEBINARDiscover the Concealed Risks of 3rd-Party SaaS Apps
Are you conscious of the pitfalls connected with 3rd-party application entry to your company’s SaaS apps? Be part of our webinar to master about the varieties of permissions becoming granted and how to decrease risk.
RESERVE YOUR SEAT
The cybersecurity enterprise claimed it determined a parallel Monero-mining marketing campaign also concentrating on uncovered Kubernetes clusters by attempting to delete the existing “proxy-api” DaemonSet associated with the Dero campaign.
This is an sign of the ongoing tussle concerning cryptojacking teams that are vying for cloud assets to just take and keep management of the equipment and consume all of its resources.
“The two strategies are hoping to locate undiscovered Kubernetes attack surfaces and are battling it out,” CrowdStrike danger scientists Benjamin Grap and Manoj Ahuje reported.
Discovered this article interesting? Abide by us on Twitter and LinkedIn to read a lot more distinctive content we publish.
Some areas of this post are sourced from:
thehackernews.com


 Microsoft Patches Two Zero Days This Month
Microsoft Patches Two Zero Days This Month