An examination of more than 70 billion DNS information has led to the discovery of a new sophisticated malware toolkit dubbed Decoy Dog targeting business networks.
Decoy Puppy, as the identify implies, is evasive and employs approaches like strategic domain ageing and DNS question dribbling, whereby a series of queries are transmitted to the command-and-command (C2) domains so as to not arouse any suspicion.
“Decoy Canine is a cohesive toolkit with a amount of highly unusual properties that make it uniquely identifiable, especially when analyzing its domains on a DNS amount,” Infoblox mentioned in an advisory revealed late last thirty day period.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The cybersecurity firm, which discovered the malware in early April 2023 pursuing anomalous DNS beaconing action, mentioned its atypical traits permitted it to map extra domains that are aspect of the attack infrastructure.

That reported, the utilization of Decoy Dog in the wild is “really exceptional,” with the DNS signature matching significantly less than .0000027% of the 370 million active domains on the internet, according to the California-based mostly enterprise.
One of the chief components of the toolkit is Pupy RAT, an open up supply trojan which is delivered by indicates of a strategy named DNS tunneling, in which DNS queries and responses are utilized as a C2 for stealthily dropping payloads.
It truly is value noting that the use of the cross-platform Pupy RAT has been linked to nation-point out actors from China this sort of as Earth Berberoka (aka GamblingPuppet) in the past, despite the fact that there is no evidence to recommend the actor’s involvement in this marketing campaign.
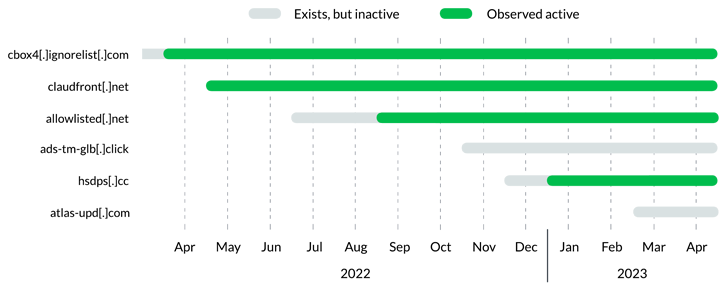
Further more investigation into Decoy Pet indicates that the procedure had been established up at the very least a year prior to its discovery, with 3 distinct infrastructure configurations detected to date.
Forthcoming WEBINARLearn to Prevent Ransomware with Real-Time Protection
Join our webinar and understand how to prevent ransomware attacks in their tracks with genuine-time MFA and assistance account protection.
Preserve My Seat!
Yet another very important component is the uncommon DNS beaconing actions connected with Decoy Pet domains, these kinds of that they adhere to a sample of periodic, but rare, DNS requests so as to fly under the radar.
“Decoy Dog domains can be grouped jointly based mostly on their shared registrars, title servers, IPs, and dynamic DNS providers,” Infoblox reported.
“Given the other commonalities between Decoy Dog domains, this is indicative of either one particular danger actor gradually evolving their methods, or several threat actors deploying the similar toolkit on diverse infrastructure.”
Identified this posting attention-grabbing? Adhere to us on Twitter and LinkedIn to go through more special content material we article.
Some pieces of this posting are sourced from:
thehackernews.com

 Wanted Dead or Alive: Real-Time Protection Against Lateral Movement
Wanted Dead or Alive: Real-Time Protection Against Lateral Movement