A new elaborate attack campaign has been observed employing PowerShell and VBScript malware to infect Windows units and harvest delicate facts.
Cybersecurity firm Securonix, which dubbed the campaign DEEP#GOSU, mentioned it’s most likely linked with the North Korean state-sponsored team tracked as Kimsuky.
“The malware payloads used in the DEEP#GOSU signify a sophisticated, multi-stage threat designed to operate stealthily on Windows programs especially from a network-checking standpoint,” security researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov stated in a specialized analysis shared with The Hacker News.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Its capabilities integrated keylogging, clipboard checking, dynamic payload execution, and details exfiltration, and persistence making use of both equally RAT software program for complete distant accessibility, scheduled responsibilities as well as self-executing PowerShell scripts using work.”
A notable facet of the infection treatment is that it leverages authentic services these kinds of as Dropbox or Google Docs for command-and-control (C2), therefore enabling the danger actor to mix undetected into typical network visitors.
On best of that, the use of this sort of cloud services to phase the payloads lets for updating the features of the malware or providing more modules.
The commencing position is stated to be a malicious email attachment made up of a ZIP archive with a rogue shortcut file (.LNK) that masquerades as a PDF file (“IMG_20240214_0001.pdf.lnk”).
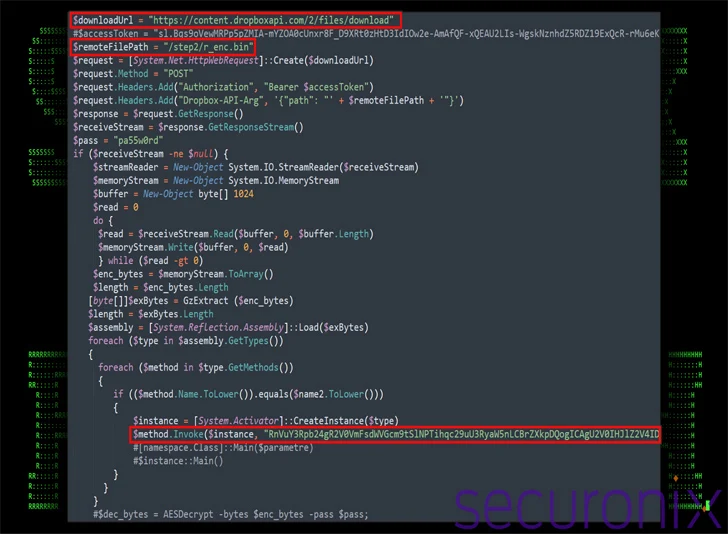
The .LNK file comes embedded with a PowerShell script as very well as a decoy PDF doc, with the former also achieving out to an actor-managed Dropbox infrastructure to retrieve and execute yet another PowerShell script (“ps.bin”).

The next-phase PowerShell script, for its aspect, fetches a new file from Dropbox (“r_enc.bin”), a .NET assembly file in binary kind that’s really an open up-source remote accessibility trojan regarded as TruRat (aka TutRat or C# RAT) with capabilities to history keystrokes, control files, and aid remote command.
It is really well worth noting that Kimsuky has utilized TruRat in at minimum two campaigns uncovered by the AhnLab Security Intelligence Heart (ASEC) last calendar year.
Also retrieved by the PowerShell script from Dropbox is a VBScript (“information_sc.txt”), which, in transform, is built to run arbitrary VBScript code retrieved from the cloud storage assistance, like a PowerShell script (“w568232.ps12x”).
The VBScript is also designed to use Windows Management Instrumentation (WMI) to execute commands on the technique, and established up scheduled tasks on the method for persistence.
A different noteworthy aspect of the VBScript is the use of Google Docs to dynamically retrieve configuration info for the Dropbox link, allowing for the risk actor to change the account data with no obtaining to alter the script itself.
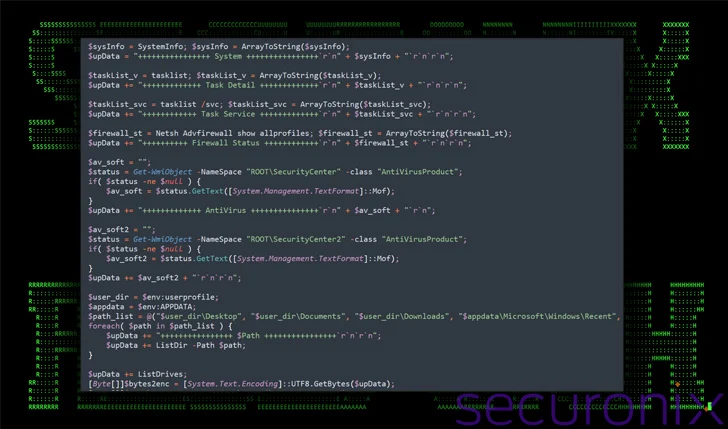
The PowerShell script downloaded as a outcome is outfitted to acquire in depth data about the program and exfiltrate the specifics through a Submit ask for to Dropbox.
“The intent of this script seems to be created to provide as a resource for periodic interaction with a command-and-manage (C2) server by means of Dropbox,” the researchers reported. “Its major uses incorporate encrypting and exfiltrating or downloading data.”
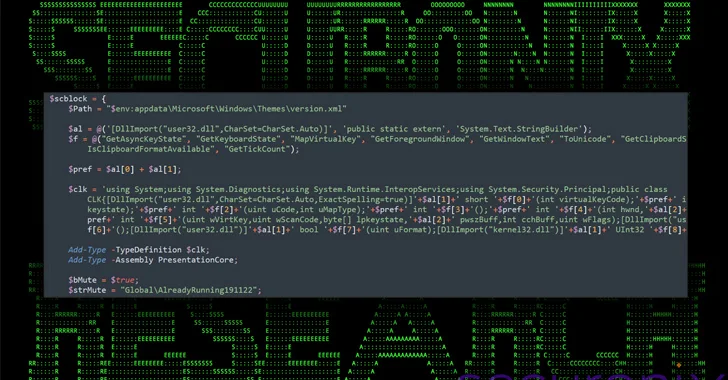
In other text, it acts as a backdoor to handle the compromised hosts and continually hold a log of consumer action, which includes keystrokes, clipboard content material, and the foreground window.
The improvement comes as security researcher Ovi Liber thorough North Korea-joined ScarCruft’s embedding of malicious code inside of Hangul Term Processor (HWP) lure documents existing in phishing email messages to distribute malware like RokRAT.
“The email has a HWP Doc which has an embedded OLE object in the kind of a BAT script,” Liber said. “As soon as the consumer clicks on the OLE item, the BAT script executes which in convert produces a PowerShell-dependent reflective DLL injection attack on the victims machine.”
It also follows Andariel’s exploitation of a reputable distant desktop alternative identified as MeshAgent to set up malware like AndarLoader and ModeLoader, a JavaScript malware intended for command execution.
“This is the very first verified use of a MeshAgent by the Andariel group,” ASEC stated. “The Andariel Group has been repeatedly abusing the asset administration solutions of domestic providers to distribute malware in the method of lateral motion, setting up with Innorix Agent in the earlier.”

Andariel, also identified by the names Nicket Hyatt or Silent Chollima, is a sub-cluster of the notorious Lazarus Team, actively orchestrating attacks for the two cyber espionage and financial gain.
The prolific point out-sponsored menace actor has due to the fact been noticed laundering a chunk of the crypto assets stolen from the hack of crypto trade HTX and its cross-chain bridge (aka HECO Bridge) by way of Twister Dollars. The breach led to the theft of $112.5 million in cryptocurrency in November 2023.
“Pursuing typical crypto-laundering designs, the stolen tokens ended up quickly swapped for ETH, making use of decentralized exchanges,” Elliptic stated. “The stolen funds then lay dormant until finally March 13, 2024, when the stolen crypto belongings commenced to be despatched by way of Twister Hard cash.”
The blockchain analytics firm reported that Tornado Cash’s continuation of its operations irrespective of sanctions have probable created it an desirable proposition for the Lazarus Team to conceal its transaction trail next the shutdown of Sinbad in November 2023.
“The mixer operates as a result of wise contracts functioning on decentralized blockchains, so it can’t be seized and shut down in the exact same way that centralized mixers these as Sinbad.io have been,” it observed.
Found this post attention-grabbing? Abide by us on Twitter and LinkedIn to browse far more exceptional written content we post.
Some pieces of this posting are sourced from:
thehackernews.com

 Fortra Patches Critical RCE Vulnerability in FileCatalyst Transfer Tool
Fortra Patches Critical RCE Vulnerability in FileCatalyst Transfer Tool