Entities situated in East and Southeast Asia as properly as Ukraine have been qualified at minimum considering that 2020 by a beforehand undocumented subgroup of APT41, a prolific Chinese superior persistent danger (APT).
Cybersecurity agency Development Micro, which christened the espionage crew Earth Longzhi, stated the actor’s long-jogging marketing campaign can be split into two primarily based on the toolset deployed to attack its victims.
The initially wave from Could 2020 to February 2021 is reported to have targeted government, infrastructure, and health care industries in Taiwan and the banking sector in China, while the succeeding established of intrusions from August 2021 to June 2022 infiltrated significant-profile victims in Ukraine and several international locations in Asia.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This involved defense, aviation, insurance plan, and urban progress industries in Taiwan, China, Thailand, Malaysia, Indonesia, Pakistan, and Ukraine.
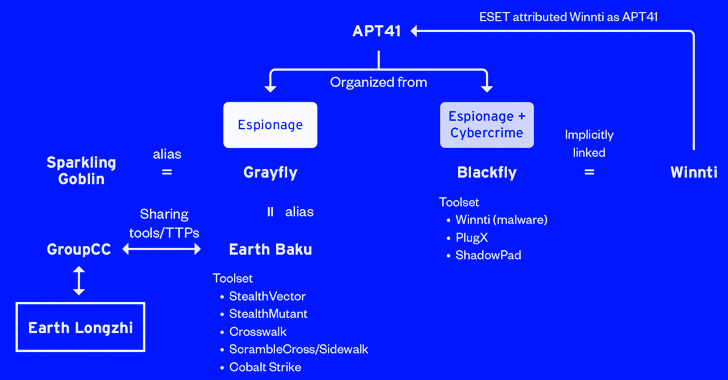
The victimology designs and the qualified sectors overlap with attacks mounted by a distinct sister group of APT41 (aka Winnti) known as Earth Baku, the Japanese cybersecurity organization additional.
Some of Earth Baku’s destructive cyber actions have been tied to groups known as by other cybersecurity corporations ESET and Symantec below the names SparklingGoblin and Grayfly, respectively.
“SparklingGoblin’s Practices, Techniques and Procedures (TTPs) partially overlap with APT41 TTPs,” ESET researcher Mathieu Tartare beforehand told The Hacker Information. “Grayfly’s definition provided by Symantec would seem to (at least partly) overlap with SparklingGoblin.”
Now Earth Longzhi provides to yet another piece in the APT41 attack puzzle, what with the actor also sharing backlinks to a 3rd subgroup dubbed GroupCC (aka APT17, Aurora Panda, or Bronze Keystone).
Attacks orchestrated by the hacker group leverage spear-phishing emails as the first entry vector. These messages are regarded to embed password-secured archives or backlinks to data files hosted on Google Generate that, when opened, launches a Cobalt Strike loader dubbed CroxLoader.
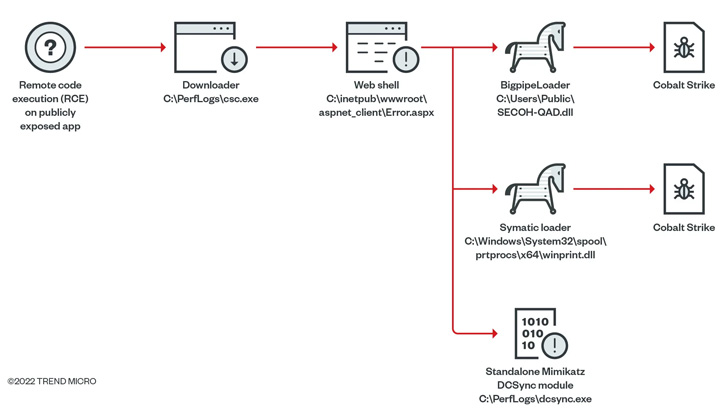
In some conditions, the group has been noticed weaponizing remote code execution flaws in publicly uncovered purposes to provide a web shell able of dropping a following-phase loader referred to as Symatic which is engineered to deploy Cobalt Strike.
Also set to use as aspect of its put up-exploitation pursuits is an “all in a single instrument,” which combines various publicly obtainable and custom made capabilities in a single offer and is thought to have been obtainable considering that September 2014.
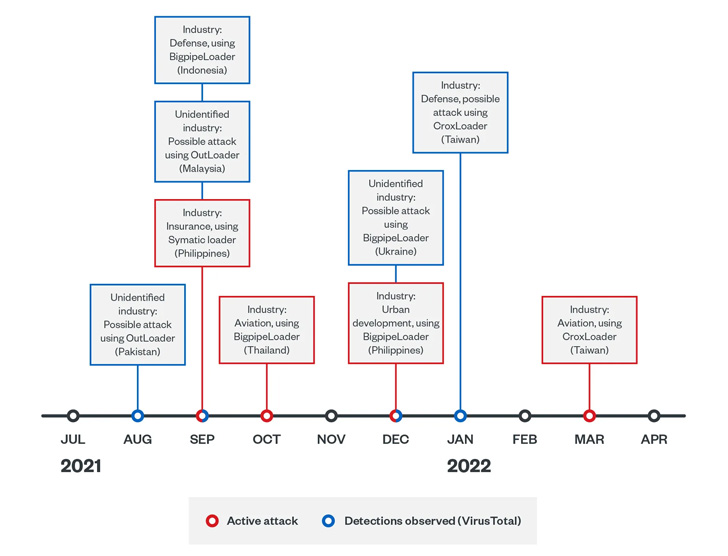
The next sequence of attacks initiated by Earth Longzhi stick to a very similar pattern, the most important variation currently being the use of unique Cobalt Strike loaders named CroxLoader, BigpipeLoader, and OutLoader to fall the crimson workforce framework on infected hosts.
The recent attacks even more stand out for the use of bespoke equipment that can disable security software, dump qualifications working with a modified edition of Mimikatz, and leverage flaws in the Windows Print Spooler part (i.e., PrintNightmare) to escalate privileges.

What is actually additional, incapacitating the mounted security solutions is pulled off by a method termed deliver your possess vulnerable driver (BYOVD), which involves the exploitation of a recognised flaw in the RTCore64.sys driver (CVE-2019-16098).
This is carried out working with ProcBurner, a tool for killing unique working processes, although an additional custom made malware identified as AVBurner is used to unregister the endpoint detection and response (EDR) procedure by eliminating procedure creation callbacks – a system that was in-depth by a security researcher who goes by the alias brsn in August 2020.
It truly is well worth noting the out-of-date edition of the RTCore64.sys driver, which still has a valid electronic signature, has been place to use by several risk actors like BlackByte and OldGremlin around the past several months.
“[Earth Longzhi’s] goal sectors are in industries pertinent to Asia-Pacific countries’ nationwide security and economies,” the researchers reported. “The actions in these strategies demonstrate that the team is well-informed on purple crew operations.”
“The team employs social engineering tactics to unfold its malware and deploy customized hack resources to bypass the safety of security goods and steal sensitive facts from compromised devices.”
Located this report interesting? Abide by THN on Facebook, Twitter and LinkedIn to read far more exceptional content material we submit.
Some sections of this short article are sourced from:
thehackernews.com

 Mass Email Extortion Campaign Claims Server Hack
Mass Email Extortion Campaign Claims Server Hack