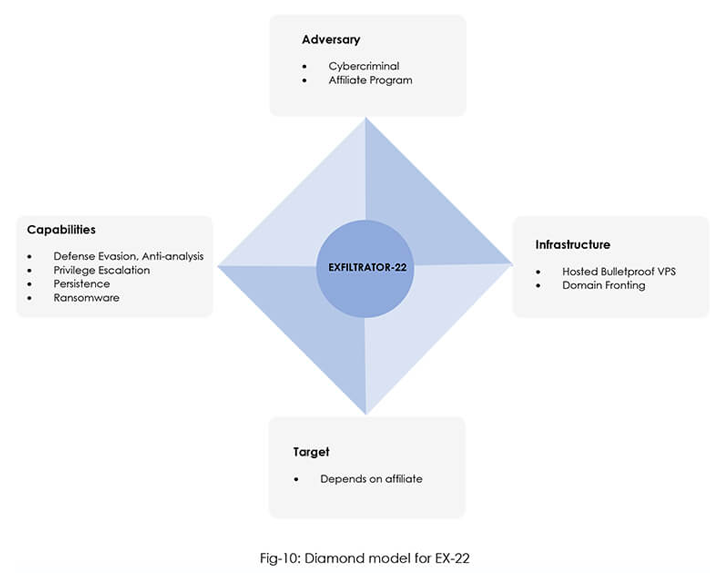
A new submit-exploitation framework identified as EXFILTRATOR-22 (aka EX-22) has emerged in the wild with the aim of deploying ransomware inside enterprise networks though traveling below the radar.
“It comes with a wide vary of capabilities, building post-exploitation a cakewalk for everyone obtaining the device,” CYFIRMA mentioned in a new report.
Some of the notable capabilities incorporate developing a reverse shell with elevated privileges, uploading and downloading data files, logging keystrokes, launching ransomware to encrypt files, and starting off a dwell VNC (Digital Network Computing) session for real-time accessibility.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
It’s also equipped to persist soon after technique reboots, perform lateral movement by means of a worm, view operating processes, create cryptographic hashes of data files, and extract authentication tokens.
The cybersecurity firm assessed with moderate self-confidence that threat actors accountable for making the malware are working from North, East, or Southeast Asia and are most likely previous affiliate marketers of the LockBit ransomware.
Advertised as a entirely undetectable malware on Telegram and YouTube, EX-22 is available for $1,000 a thirty day period or $5,000 for life span access. Felony actors purchasing the toolkit are supplied a login panel to access the EX-22 server and remotely manage the malware.
Due to the fact its initially appearance on November 27, 2022, the malware authors have constantly iterated the toolkit with new options, indicating energetic growth work.
The connections to LockBit 3. come up from technological and infrastructure overlaps, with the two malware people using the very same domain fronting system for hiding command-and-command (C2) site visitors.
The put up-exploitation-framework-as-a-provider (PEFaaS) design is the most recent device available for adversaries searching to sustain covert accessibility to compromised gadgets over an extended period of time of time.
It also joins other frameworks like Manjusaka and Alchimist as very well as authentic and open up resource solutions these types of as Cobalt Strike, Metasploit, Sliver, Empire, Brute Ratel, and Havoc that have been co-opted for destructive ends.
Discovered this write-up exciting? Follow us on Twitter and LinkedIn to examine a lot more distinctive material we publish.
Some areas of this article are sourced from:
thehackernews.com

 How to build a cyber-resilient business read to innovate and thrive
How to build a cyber-resilient business read to innovate and thrive