A in no way-ahead of-viewed botnet named Goldoon has been noticed focusing on D-Backlink routers with a almost decade-old critical security flaw with the aim of utilizing the compromised devices for even further attacks.
The vulnerability in dilemma is CVE-2015-2051 (CVSS score: 9.8), which impacts D-Link DIR-645 routers and makes it possible for remote attackers to execute arbitrary instructions by signifies of specially crafted HTTP requests.
“If a qualified unit is compromised, attackers can get comprehensive management, enabling them to extract technique data, set up interaction with a C2 server, and then use these gadgets to launch more attacks, these kinds of as distributed denial-of-provider (DDoS),” Fortinet FortiGuard Labs researchers Cara Lin and Vincent Li reported.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Telemetry knowledge from the network security corporation points to a spike in the botnet activity all over April 9, 2024.
It all commences with the exploitation of CVE-2015-2051 to retrieve a dropper script from a distant server, which is responsible for liable for downloading the upcoming-stage payload for diverse Linux method architectures, like aarch64, arm, i686, m68k, mips64, mipsel, powerpc, s390x, sparc64, x86-64, sh4, riscv64, DEC Alpha, and PA-RISC.

The payload is subsequently launched on the compromised product and acts as a downloader for the Goldoon malware from a distant endpoint, immediately after which the dropper gets rid of the executed file and then deletes alone in a bid to cover up the trail and fly beneath the radar.
Any endeavor to accessibility the endpoint directly by using a web browser shows the error information: “Sorry, you are an FBI Agent & we are not able to assistance you 🙁 Go away or I will destroy you :)”
Goldoon, apart from location up persistence on the host applying different autorun methods, establishes contact with a command-and-control (C2) server to await commands for stick to-up actions.
This incorporates an “astounding 27 distinct procedures” to pull off DDoS flood attacks working with a variety of protocols like DNS, HTTP, ICMP, TCP, and UDP.
“Though CVE-2015-2051 is not a new vulnerability and provides a low attack complexity, it has a critical security affect that can guide to distant code execution,” the researchers mentioned.
The growth comes as botnets continue to evolve and exploit as a lot of units as probable, even as cybercriminals and advanced persistent threat (APT) actors alike have shown an interest in compromised routers for use as an anonymization layer.
“Cybercriminals rent out compromised routers to other criminals, and most probable also make them readily available to business residential proxy suppliers,” cybersecurity enterprise Pattern Micro explained in a report.
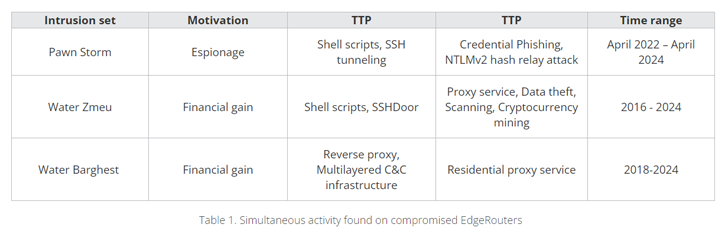
“Nation-state threat actors like Sandworm made use of their own committed proxy botnets, although APT team Pawn Storm had entry to a legal proxy botnet of Ubiquiti EdgeRouters.”
In using the hacked routers as proxies, the goal is to disguise traces of their existence and make detection of malicious activities more tricky by mixing their exercise in with benign ordinary visitors.
Previously this February, the U.S. government took measures to dismantle elements of a botnet called MooBot that, between other internet-struggling with products like Raspberry Pi and VPS servers, mainly leveraged Ubiquiti EdgeRouters.

Craze Micro said it noticed the routers staying utilized for Protected Shell (SSH) brute forcing, pharmaceutical spam, using server information block (SMB) reflectors in NTLMv2 hash relay attacks, proxying stolen qualifications on phishing web pages, multi-goal proxying, cryptocurrency mining, and sending spear phishing emails.
Ubiquiti routers have also arrive under assault from another danger actor that infects these gadgets with a malware dubbed Ngioweb, which are then employed as exit nodes in a commercially out there residential proxy botnet.
The conclusions further more underscore the use of different malware families to wrangle the routers into a network that threat actors could control, efficiently turning them into covert listening posts capable of monitoring all network traffic.
“Internet routers remain a popular asset for danger actors to compromise given that they typically have lessened security checking, have a lot less stringent password procedures, are not updated regularly, and may possibly use strong running units that lets for set up of malware such as cryptocurrency miners, proxies, distributed denial of assistance (DDoS malware), destructive scripts, and web servers,” Development Micro stated.
Found this write-up interesting? Follow us on Twitter and LinkedIn to read through a lot more special information we submit.
Some areas of this post are sourced from:
thehackernews.com


 CISA Warns of Active Exploitation of Severe GitLab Password Reset Vulnerability
CISA Warns of Active Exploitation of Severe GitLab Password Reset Vulnerability