An updated model of a malware loader codenamed IceXLoader is suspected of possessing compromised thousands of personal and company Windows equipment across the earth.
IceXLoader is a commodity malware which is sold for $118 on underground forums for a life span license. It is really mainly employed to down load and execute further malware on breached hosts.
This past June, Fortinet FortiGuard Labs reported it uncovered a model of the trojan created in the Nim programming language with the objective of evading evaluation and detection.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Whilst the version learned in June (v3.) appeared like a perform-in-development, we recently observed a newer v3.3.3 loader which appears to be absolutely functionable and incorporates a multi-stage shipping chain,” Natalie Zargarov, cybersecurity researcher at Minerva Labs, explained in a report posted Tuesday.
IceXLoader is traditionally dispersed through phishing campaigns, with email messages containing ZIP archives functioning as a bring about to deploy the malware. Infection chains have leveraged IceXLoader to produce DarkCrystal RAT and cryptocurrency miners.
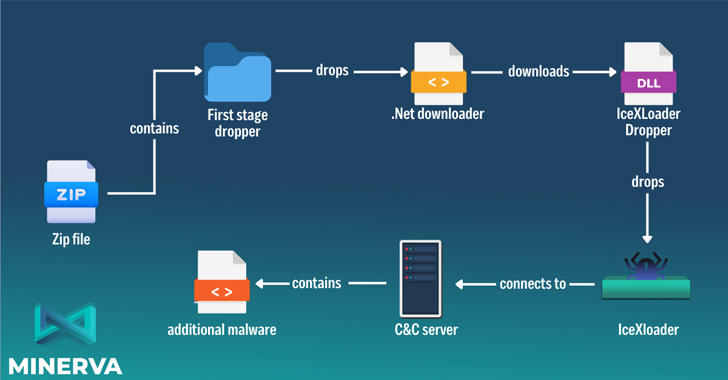
In the attack sequence detailed by Minerva Labs, the ZIP file has been uncovered to harbor a dropper, which drops a .NET-dependent downloader that, as the identify implies, download a PNG image (“Ejvffhop.png”) from a challenging-coded URL.
This graphic file, yet another dropper, is subsequently converted into an array of bytes, efficiently allowing for it to decrypt and inject IceXLoader into a new method making use of a technique termed process hollowing.

Edition 3.3.3 of IceXLoader, like its predecessor, is written in Nim and is outfitted to obtain process metadata, all of which is exfiltrated to a remote attacker-controlled domain, although awaiting further instructions issued by the server.
The commands incorporate the means to restart and uninstall the malware loader and halt its execution. But its principal feature is to download and execute subsequent-stage malware on disk or filelessly in memory.
Minerva Labs reported a SQLite database file hosted in the command-and-regulate (C2) server is becoming continually current with data about 1000’s of victims, incorporating it really is in the process of notifying impacted organizations.
Observed this article interesting? Adhere to THN on Fb, Twitter and LinkedIn to browse extra unique content material we put up.
Some sections of this post are sourced from:
thehackernews.com

 Instagram Influencer Gets 11 Years for Money Laundering
Instagram Influencer Gets 11 Years for Money Laundering