Ukrainian entities based mostly in Finland have been focused as section of a malicious marketing campaign distributing a business distant access trojan recognised as Remcos RAT making use of a malware loader called IDAT Loader.
The attack has been attributed to a threat actor tracked by the Laptop Emergency Response Staff of Ukraine (CERT-UA) beneath the moniker UAC-0184.
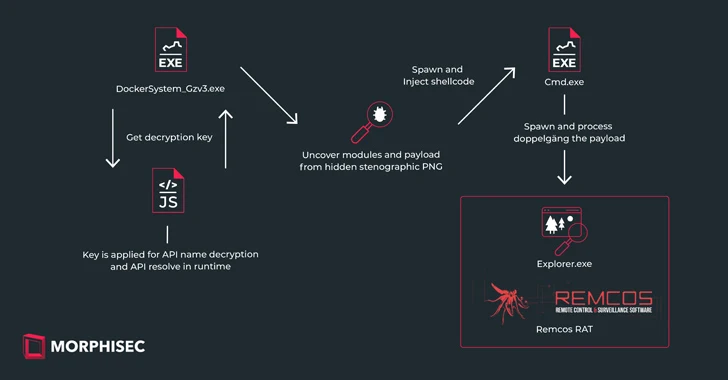
“The attack, as section of the IDAT Loader, employed steganography as a method,” Morphisec researcher Michael Dereviashkin claimed in a report shared with The Hacker Information. “Whilst steganographic, or ‘Stego’ tactics are perfectly-recognized, it is important to recognize their roles in defense evasion, to superior comprehend how to protect in opposition to such techniques.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

IDAT Loader, which overlaps with yet another loader spouse and children termed Hijack Loader, has been used to serve supplemental payloads like DanaBot, SystemBC, and RedLine Stealer in modern months. It has also been applied by a risk actor tracked as TA544 to distribute Remcos RAT and SystemBC via phishing attacks.
The phishing campaign – 1st disclosed by CERT-UA in early January 2024 – entail applying war-themed lures as a beginning point to kick-start out an infection chain that sales opportunities to the deployment of IDAT Loader, which, in flip, takes advantage of an embedded steganographic PNG to track down and extract Remcos RAT.
The progress comes as CERT-UA disclosed that protection forces in the place have been specific by way of the Sign prompt messaging application to distribute a booby-trapped Microsoft Excel document that executes COOKBOX, a PowerShell-primarily based malware that is capable of loading and executing cmdlets. CERT-UA has attributed the activity to a cluster dubbed UAC-0149.

It also follows the resurgence of malware campaigns propagating PikaBot malware given that February 8, 2024, using an up-to-date variant that seems to be currently less than lively improvement.
“This version of the PIKABOT loader employs a new unpacking strategy and significant obfuscation,” Elastic Security Labs reported. “The core module has added a new string decryption implementation, changes to obfuscation functionality, and several other modifications.”
Found this article attention-grabbing? This post is a contributed piece from a person of our valued partners. Stick to us on Twitter and LinkedIn to study more unique content we post.
Some areas of this report are sourced from:
thehackernews.com

 8,000+ Subdomains of Trusted Brands Hijacked for Massive Spam Operation
8,000+ Subdomains of Trusted Brands Hijacked for Massive Spam Operation