A new Go-primarily based malware loader identified as JinxLoader is being made use of by menace actors to provide subsequent-stage payloads this sort of as Formbook and its successor XLoader.
The disclosure arrives from cybersecurity firms Palo Alto Networks Device 42 and Symantec, the two of which highlighted multi-phase attack sequences that led to the deployment of JinxLoader by means of phishing attacks.
“The malware pays homage to League of Legends character Jinx, that includes the character on its advert poster and [command-and-control] login panel,” Symantec reported. “JinxLoader’s principal purpose is straightforward – loading malware.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Device 42 discovered in late November 2023 that the malware provider was initial marketed on hackforums[.]net on April 30, 2023, for $60 a thirty day period, $120 a yr, or for a lifetime payment of $200.

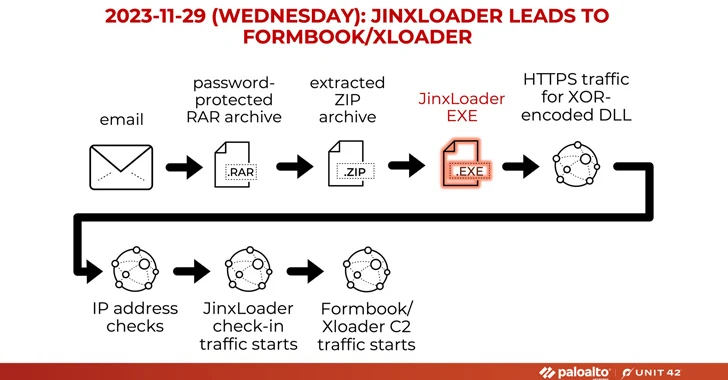
The attacks start off with phishing e-mails impersonating Abu Dhabi Nationwide Oil Enterprise (ADNOC), urging recipients to open up password-shielded RAR archive attachments that, upon opening, drop the JinxLoader executable, which subsequently functions as a gateway for Formbook or XLoader.
The enhancement comes as ESET exposed a spike in infections, delivering yet another beginner loader malware household dubbed Rugmi to propagate a broad selection of information stealers.
It also arrives amid a surge in strategies distributing DarkGate and PikaBot, with a risk actor acknowledged as TA544 (aka Narwal Spider) leveraging new variants of loader malware called IDAT Loader to deploy Remcos RAT or SystemBC malware.
What is much more, the menace actors at the rear of the Meduza Stealer have introduced an up to date model of the malware (model 2.2) on the dark web with expanded guidance for browser-primarily based cryptocurrency wallets and an improved credit history card (CC) grabber.

In a indicator that stealer malware proceeds to be a lucrative market place for cybercriminals, scientists have learned a new stealer household acknowledged as Vortex Stealer that is able of exfiltrating browser details, Discord tokens, Telegram classes, procedure details, and information that are a lot less than 2 MB in size.
“Stolen details will be archived and uploaded to Gofile or Anonfiles the malware will also publish it onto the author’s Discord working with webhooks,” Symantec mentioned. “It truly is also able of publishing to Telegram through a Telegram bot.”
Uncovered this report intriguing? Comply with us on Twitter and LinkedIn to browse additional special information we write-up.
Some areas of this post are sourced from:
thehackernews.com

 Beware: Scam-as-a-Service Aiding Cybercriminals in Crypto Wallet-Draining Attacks
Beware: Scam-as-a-Service Aiding Cybercriminals in Crypto Wallet-Draining Attacks