A new botnet consisting of firewalls and routers from Cisco, DrayTek, Fortinet, and NETGEAR is currently being made use of as a covert info transfer network for superior persistent risk actors, including the China-linked menace actor termed Volt Typhoon.
Dubbed KV-botnet by the Black Lotus Labs crew at Lumen Systems, the destructive network is an amalgamation of two complementary activity clusters that have been active given that at the very least February 2022.
“The campaign infects devices at the edge of networks, a segment that has emerged as a smooth location in the defensive array of a lot of enterprises, compounded by the change to distant operate in recent years,” the organization claimed.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Impending WEBINAR Conquer AI-Run Threats with Zero Belief – Webinar for Security Industry experts
Conventional security measures is not going to slash it in present-day planet. It really is time for Zero Have faith in Security. Protected your details like under no circumstances in advance of.
Be part of Now
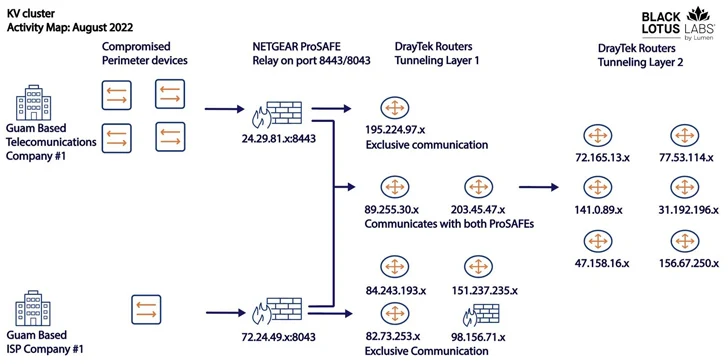
The two clusters – codenamed KY and JDY – are stated to be distinctive but operating in tandem to aid accessibility to large-profile victims as nicely as set up covert infrastructure. Telemetry knowledge suggests that the botnet is commandeered from IP addresses primarily based in China.
When the bots section of JDY engages in broader scanning working with considerably less subtle strategies, the KY component, showcasing mostly outdated and close-of-life items, is assessed to be reserved for handbook operations in opposition to large-profile targets picked by the previous.
It is suspected that Volt Hurricane is at least 1 person of the KV-botnet and it encompasses a subset of their operational infrastructure, which is evidenced by the obvious drop in operations in June and early July 2023, coinciding with the public disclosure of the adversarial collective’s concentrating on of critical infrastructure in the U.S.
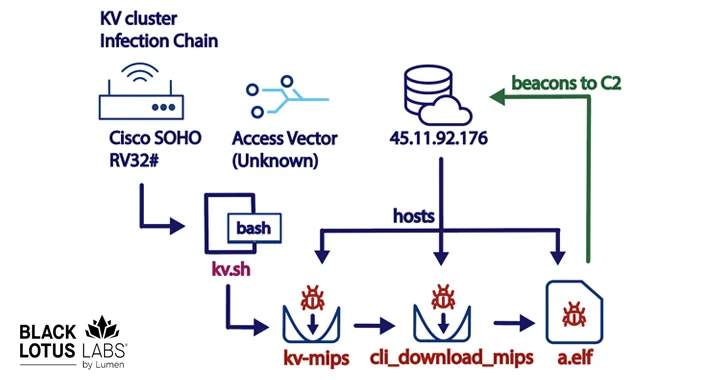
Microsoft, which first uncovered the risk actor’s tactics, stated it “tries to mix into normal network activity by routing targeted traffic through compromised modest office and home workplace (SOHO) network gear, such as routers, firewalls, and VPN components.”
The actual initial an infection system process utilized to breach the gadgets is now not known. It truly is adopted by the initially-stage malware getting steps to clear away security plans and other malware strains so as to guarantee that it is the “only existence” on these machines.

It is also created to retrieve the main payload from a distant server, which, in addition to beaconing back again to the identical server, is also capable of uploading and downloading files, functioning instructions, and executing more modules.
In excess of the earlier thirty day period, the botnet’s infrastructure has acquired a facelift, targeting Axis IP cameras, indicating that the operators could be gearing up for a new wave of attacks.
“A single of the somewhat exciting factors of this marketing campaign is that all the tooling seems to reside completely in-memory,” the scientists reported. “This makes detection very difficult, at the price tag of extensive-expression persistence.”
“As the malware resides fully in-memory, by only energy-cycling the device the close user can cease the an infection. Although that gets rid of the imminent threat, re-infection is transpiring regularly.”
Located this short article fascinating? Adhere to us on Twitter and LinkedIn to browse far more special information we post.
Some parts of this article are sourced from:
thehackernews.com

 Crypto Hardware Wallet Ledger’s Supply Chain Breach Results in $600,000 Theft
Crypto Hardware Wallet Ledger’s Supply Chain Breach Results in $600,000 Theft