An examination of the Linux variant of a new ransomware pressure termed BlackSuit has covered important similarities with a different ransomware family members referred to as Royal.
Development Micro, which examined an x64 VMware ESXi model focusing on Linux machines, explained it identified an “particularly high diploma of similarity” concerning Royal and BlackSuit.
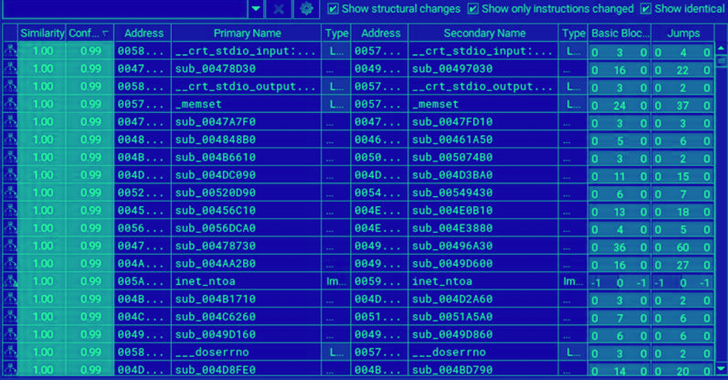
“In truth, they’re nearly similar, with 98% similarities in features, 99.5% similarities in blocks, and 98.9% similarities in jumps centered on BinDiff, a comparison software for binary information,” Pattern Micro researchers famous.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
A comparison of the Windows artifacts has identified 93.2% similarity in functions, 99.3% in simple blocks, and 98.4% in jumps primarily based on BinDiff.
BlackSuit to start with arrived to gentle in early Could 2023 when Palo Alto Networks Device 42 drew interest to its potential to concentrate on equally Windows and Linux hosts.

In line with other ransomware teams, it operates a double extortion plan that steals and encrypts delicate info in a compromised network in return for monetary compensation. Information involved with a one target has been stated on its dark web leak web site.
The most recent conclusions from Pattern Micro demonstrate that, each BlackSuit and Royal use OpenSSL’s AES for encryption and use equivalent intermittent encryption procedures to pace up the encryption approach.
The overlaps aside, BlackSuit incorporates supplemental command-line arguments and avoids a diverse checklist of information with unique extensions in the course of enumeration and encryption.
“The emergence of BlackSuit ransomware (with its similarities to Royal) signifies that it is both a new variant developed by the exact authors, a copycat working with comparable code, or an affiliate of the Royal ransomware gang that has applied modifications to the original spouse and children,” Trend Micro said.
Supplied that Royal is an offshoot of the erstwhile Conti team, it’s also feasible that “BlackSuit emerged from a splinter group in the authentic Royal ransomware gang,” the cybersecurity corporation theorized.
The improvement at the time once again underscores the regular condition of flux in the ransomware ecosystem, even as new danger actors arise to tweak current equipment and make illicit profits.
Forthcoming WEBINAR 🔐 Mastering API Security: Being familiar with Your True Attack Area
Find out the untapped vulnerabilities in your API ecosystem and consider proactive measures towards ironclad security. Be a part of our insightful webinar!
Be part of the Session.advertisement-button,.ad-label,.ad-label:followingdisplay:inline-block.advert_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px strong #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-best-still left-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-ideal-radius:25px-moz-border-radius-bottomright:25px.advertisement-labelfont-size:13pxmargin:20px 0font-excess weight:600letter-spacing:.6pxcolor:#596cec.ad-label:followingwidth:50pxheight:6pxcontent:”border-top rated:2px sound #d9deffmargin: 8px.advert-titlefont-size:21pxpadding:10px 0font-pounds:900textual content-align:leftline-peak:33px.ad-descriptiontextual content-align:leftfont-dimensions:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.advertisement-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-dimension:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-fat:500letter-spacing:.2px
This incorporates a new ransomware-as-a-service (RaaS) initiative codenamed NoEscape that Cyble claimed lets its operators and affiliates to choose gain of triple extortion approaches to optimize the affect of a prosperous attack.
Triple extortion refers to a a few-pronged approach whereby knowledge exfiltration and encryption is coupled with dispersed denial-of-service (DDoS) attacks in opposition to the targets in an try to disrupt their business enterprise and coerce them into paying out the ransom.
The DDoS services, for every Cyble, is out there for an extra $500,000 price, with the operators imposing conditions that forbid affiliate marketers from hanging entities found in the Commonwealth of Impartial States (CIS) nations.
Located this short article fascinating? Observe us on Twitter and LinkedIn to go through extra exceptional content material we post.
Some parts of this report are sourced from:
thehackernews.com

 Cloud Security Tops Concerns for Cybersecurity Leaders: EC-Council’s Certified CISO Hall of Fame Report 2023
Cloud Security Tops Concerns for Cybersecurity Leaders: EC-Council’s Certified CISO Hall of Fame Report 2023