A new malvertising marketing campaign has been noticed leveraging advertisements on Google Look for and Bing to target end users trying to find IT equipment like AnyDesk, Cisco AnyConnect VPN, and WinSCP, and trick them into downloading trojanized installers with an goal to breach company networks and possible carry out future ransomware attacks.
Dubbed Nitrogen, the “opportunistic” activity is intended to deploy next-phase attack applications this kind of as Cobalt Strike, Sophos explained in a Wednesday evaluation.
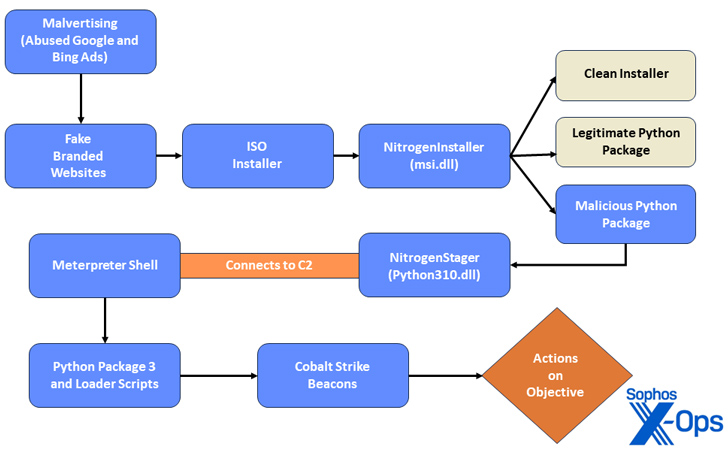
Nitrogen was 1st documented by eSentire in June 2023, detailing an an infection chain that redirects consumers to compromised WordPress internet sites hosting destructive ISO image data files that ultimately culminate in the shipping of Python scripts and Cobalt Strike Beacons onto the targeted process.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Then before this thirty day period, Pattern Micro uncovered a equivalent attack sequence in which a fraudulent WinSCP software functioned as a stepping stone for a BlackCat ransomware attack.
“All through the infection chain, the danger actors use unusual export forwarding and DLL preloading strategies to mask their malicious activity and hinder analysis,” Sophos researchers Gabor Szappanos, Morgan Demboski, and Benjamin Sollman mentioned.
Approaching WEBINARShield Versus Insider Threats: Learn SaaS Security Posture Management
Anxious about insider threats? We’ve bought you included! Sign up for this webinar to investigate sensible tactics and the secrets of proactive security with SaaS Security Posture Administration.
Sign up for These days
The Python scripts, once released, create a Meterpreter reverse TCP shell, thus making it possible for menace actors to remotely execute code on the contaminated host, as very well as download a Cobalt Strike Beacon to facilitate submit-exploitation.
“Abuse of pay back-for each-click commercials displayed in research engine outcomes has develop into a preferred tactic among danger actors,” the scientists reported. “The menace actors are hoping to forged a huge net to entice unsuspecting consumers trying to find specific IT utilities.”
The results also occur in opposition to the backdrop of a spike in cybercriminals employing paid adverts to lure end users to destructive web pages and trick them into downloading a range of malware these kinds of as BATLOADER, EugenLoader (aka FakeBat), and IcedID, which are then used to distribute details stealers and other payloads.
To make matters worse, Sophos stated it located on outstanding criminal marketplaces a “substantial quantity of ads for, and discussion about, Search engine marketing poisoning, malvertising, and connected providers” as very well as sellers giving compromised Google Advertisements accounts.
This illustrates that “marketplaces buyers have a eager curiosity in Search engine optimization poisoning and malvertising” and that “it also negates the trouble of making an attempt to bypass email filters and convincing consumers to click a hyperlink or download and open an attachment.”
Discovered this article attention-grabbing? Abide by us on Twitter and LinkedIn to go through a lot more exceptional articles we publish.
Some elements of this posting are sourced from:
thehackernews.com


 The 4 Keys to Building Cloud Security Programs That Can Actually Shift Left
The 4 Keys to Building Cloud Security Programs That Can Actually Shift Left