A new variant of the infamous Mirai botnet has been found leveraging numerous security vulnerabilities to propagate by itself to Linux and IoT products.
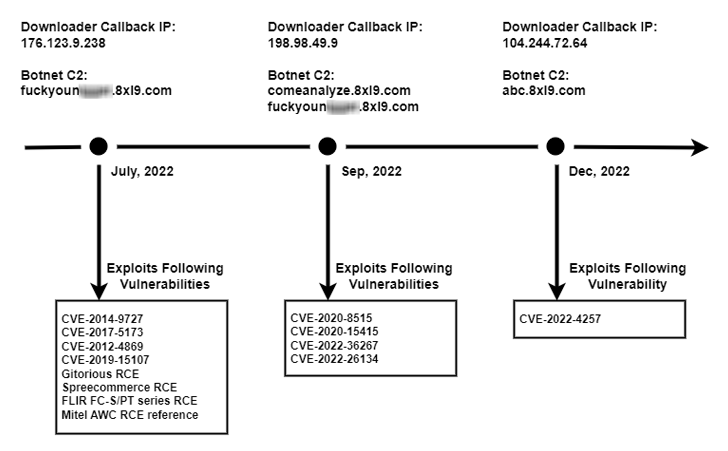
Observed in the course of the next 50 % of 2022, the new version has been dubbed V3G4 by Palo Alto Networks Device 42, which determined 3 distinct campaigns possible executed by the very same danger actor.
“As soon as the vulnerable units are compromised, they will be entirely controlled by attackers and develop into a part of the botnet,” Unit 42 scientists mentioned. “The risk actor has the functionality to use those gadgets to perform even more attacks, these as distributed denial-of-services (DDoS) attacks.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The attacks mainly solitary out uncovered servers and networking products working Linux, with the adversary weaponizing as quite a few as 13 flaws that could direct to remote code execution (RCE).
Some of the noteworthy flaws relate to critical flaws in Atlassian Confluence Server and Knowledge Center, DrayTek Vigor routers, Airspan AirSpot, and Geutebruck IP cameras, among the others. The oldest flaw in the record is CVE-2012-4869, an RCE bug in FreePBX.
Pursuing a profitable compromise, the botnet payload is retrieved from a remote server using the wget and cURL utilities.
The botnet, in addition to examining if it’s presently functioning on the infected machine, also takes ways to terminate other competing botnets this sort of as Mozi, Okami, and Yakuza.
V3G4 additional packs a established of default or weak login credentials that it makes use of to have out brute-pressure attacks by way of Telnet/SSH and proliferate to other equipment.
It also establishes make contact with with a command-and-regulate server to await commands for launching DDoS attacks towards targets through UDP, TCP, and HTTP protocols.
“The vulnerabilities outlined higher than have less attack complexity than formerly observed variants, but they sustain a critical security effect that can guide to distant code execution,” the scientists mentioned.
To stave off this sort of attacks, it’s proposed that people apply required patches and updates as and when they turn out to be applicable, and secure the equipment with powerful passwords.
Identified this short article fascinating? Observe us on Twitter and LinkedIn to examine extra special information we put up.
Some elements of this write-up are sourced from:
thehackernews.com

 How IT professionals can switch careers into cyber security
How IT professionals can switch careers into cyber security