A new collection of 8 method injection strategies, collectively dubbed PoolParty, could be exploited to realize code execution in Windows methods when evading endpoint detection and reaction (EDR) devices.
SafeBreach researcher Alon Leviev claimed the strategies are “capable of performing across all processes without any limitations, earning them additional adaptable than existing approach injection strategies.”
The conclusions ended up 1st offered at the Black Hat Europe 2023 conference last 7 days.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Impending WEBINAR Cracking the Code: Study How Cyber Attackers Exploit Human Psychology
Ever questioned why social engineering is so successful? Dive deep into the psychology of cyber attackers in our upcoming webinar.
Be a part of Now
System injection refers to an evasion approach used to operate arbitrary code in a target method. A huge array of approach injection procedures exists, such as dynamic url library (DLL) injection, moveable executable injection, thread execution hijacking, system hollowing, and method doppelgänging.
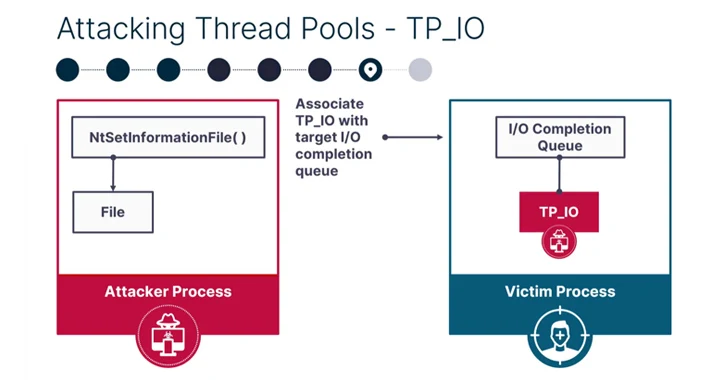
PoolParty is so named for the reason that it can be rooted in a part referred to as Windows consumer-method thread pool, leveraging it to insert any form of do the job product into a goal system on the system.
It functions by concentrating on employee factories – which refer to Windows objects that are liable for handling thread pool employee threads – and overwriting the start out regime with malicious shellcode for subsequent execution by the employee threads.

“Other than the queues, the worker manufacturing facility that serves as the employee threads manager may well be applied to consider over the employee threads,” Leviev mentioned.
SafeBreach explained it was in a position to devise seven other method injection strategies applying the endeavor queue (normal function objects), I/O completion queue (asynchronous do the job things), and the timer queue (timer work products) centered on the supported get the job done products.
PoolParty has been identified to reach 100% results rate towards popular EDR remedies, like people from CrowdStrike, Cybereason, Microsoft, Palo Alto Networks, and SentinelOne.

The disclosure comes just about six months just after Security Joes disclosed yet another procedure injection method dubbed Mockingjay could be exploited by danger actors to bypass security alternatives to execute malicious code on compromised methods.
“Nevertheless modern day EDRs have evolved to detect recognized procedure injection procedures, our study has demonstrated that it is however doable to develop novel tactics that are undetectable and have the potential to make a devastating effects,” Leviev concluded.
“Complex menace actors will proceed to explore new and revolutionary approaches for procedure injection, and security resource distributors and practitioners need to be proactive in their protection towards them.”
Found this short article intriguing? Comply with us on Twitter and LinkedIn to go through extra unique content we publish.
Some components of this report are sourced from:
thehackernews.com

 SLAM Attack: New Spectre-based Vulnerability Impacts Intel, AMD, and Arm CPUs
SLAM Attack: New Spectre-based Vulnerability Impacts Intel, AMD, and Arm CPUs