North Korean point out-sponsored risk actors have been attributed to a cyber espionage marketing campaign focusing on the defense sector throughout the planet.
In a joint advisory revealed by Germany’s Federal Business office for the Protection of the Constitution (BfV) and South Korea’s Countrywide Intelligence Company (NIS), the businesses stated the intention of the attacks is to plunder highly developed protection technologies in a “value-productive” manner.
“The regime is working with the armed forces systems to modernize and strengthen the functionality of typical weapons and to establish new strategic weapon units such as ballistic missiles, reconnaissance satellites and submarines,” they pointed out.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The notorious Lazarus Team has been blamed for one of the two hacking incidents, which involved the use of social engineering to infiltrate the defense sector as part of a extensive-standing operation identified as Aspiration Position. The marketing campaign has been ongoing considering that August 2020 about several waves.
In these attacks, the menace actors possibly produce a fake profile or leverage authentic-but-compromised profiles on platforms like LinkedIn to strategy possible targets and establish believe in with them, right before supplying valuable position possibilities and shifting the discussion to a diverse messaging provider like WhatsApp to initiate the recruitment approach.

Victims are then sent coding assignments and position give documents laden with malware that, when released, activate the infection treatment to compromise their computer systems.
“Universally, the circumstance that staff members ordinarily do not chat to their colleagues or employer about position features performs into the arms of the attacker,” the companies claimed.
“The Lazarus Team changed its resources all over the campaign and demonstrated a lot more than at the time that it is capable of developing whatever is vital to fit the scenario.”
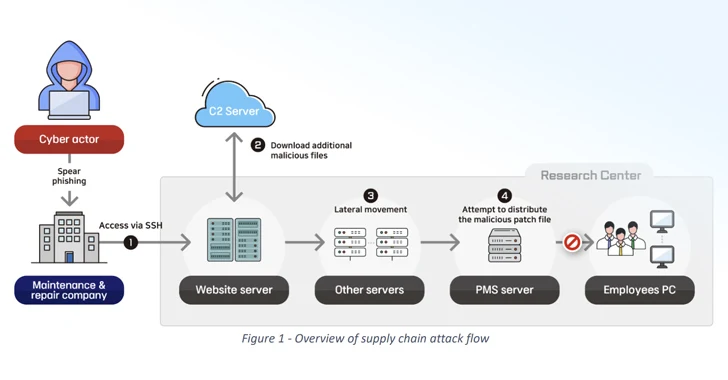
The next scenario considerations an intrusion into a defense study centre toward the end of 2022 by executing a software package supply chain attack versus an unnamed enterprise liable for maintaining one of the exploration center’s web servers.
“The cyber actor even more infiltrated the investigate facility by deploying remote-regulate malware by means of a patch management system (PMS) of the study centre, and stole many account data of enterprise portals and email contents,” the BfV and NIS stated.

The breach, which was carried by one more North Korea-primarily based danger actor, unfolded above 5 stages –
- Hack into the web server servicing company, steal SSH qualifications, and attain remote obtain to the study center’s server
- Download additional malicious tooling using curl instructions, together with a tunneling software package and a Python-centered downloader
- Perform lateral movement and plunder employee account qualifications
- Leverage the stolen security manager’s account information and facts to unsuccessfully distribute a trojanized update that comes with capabilities to upload and down load information, execute code, and to gather technique information and facts
- Persist in focus on surroundings by weaponizing a file add vulnerability in the internet site to deploy a web shell for distant accessibility and send spear-phishing email messages
“The actor prevented carrying out a direct attack against its concentrate on, which maintained a superior stage of security, but rather designed an initial attack versus its seller, the servicing and repair business,” the businesses explained. “This suggests that the actor took advantage of the trustful marriage involving the two entities.”

The security bulletin is the 2nd to be printed by BfV and NIS in as many years. In March 2023, the agencies warned of Kimsuky actors using rogue browser extensions to steal users’ Gmail inboxes. Kimsuky was sanctioned by the U.S. govt in November 2023.
The improvement arrives as blockchain analytics business Chainalysis discovered that the Lazarus Group has switched to utilizing YoMix bitcoin mixer to launder stolen proceeds pursuing the shutdown of Sinbad late past 12 months, indicating their means to adapt their modus operandi in reaction to regulation enforcement steps.
“Sinbad turned a desired mixer for North Korea-affiliated hackers in 2022, before long following the sanctioning of Tornado Cash, which had previously been the go-to for these subtle cybercriminals,” the company stated. “With Sinbad out of the image, Bitcoin-centered mixer YoMix has acted as a alternative.”
The destructive pursuits are the get the job done of a myriad of North Korean hacking units running below the broad Lazarus umbrella, which are known to have interaction in an array of hacking operations ranging from cyber espionage to cryptocurrency thefts, ransomware, and supply chain attacks to achieve their strategic targets.
Found this report appealing? Comply with us on Twitter and LinkedIn to read more distinctive material we article.
Some pieces of this article are sourced from:
thehackernews.com

 Critical Flaws Found in ConnectWise ScreenConnect Software – Patch Now
Critical Flaws Found in ConnectWise ScreenConnect Software – Patch Now