A new campaign leveraging an exploit package has been observed abusing an Internet Explorer flaw patched by Microsoft previous calendar year to deliver the RedLine Stealer trojan.
“When executed, RedLine Stealer performs recon from the target program (including username, hardware, browsers put in, anti-virus computer software) and then exfiltrates facts (together with passwords, saved credit rating cards, crypto wallets, VPN logins) to a distant command and regulate server,” Bitdefender reported in a new report shared with The Hacker Information.
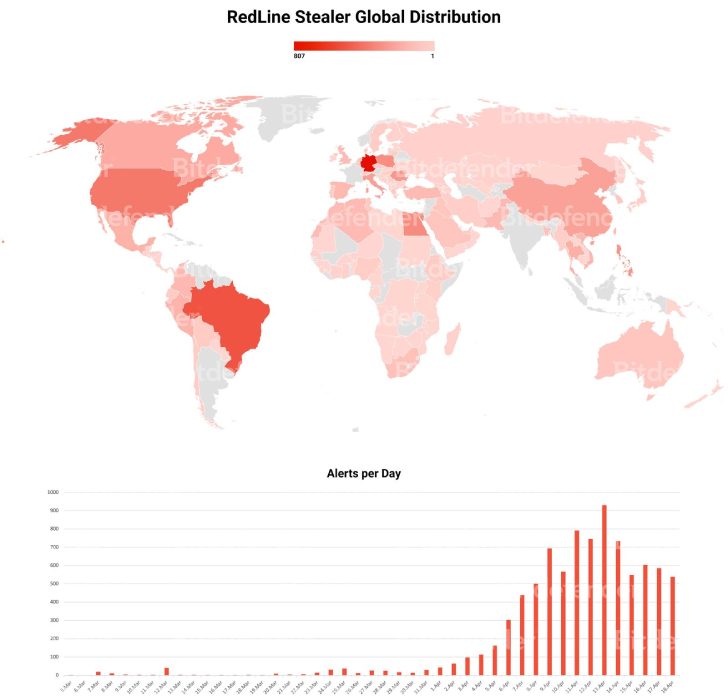
Most of the bacterial infections are located in Brazil and Germany, followed by the U.S., Egypt, Canada, China, and Poland, amongst some others.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Exploit kits or exploit packs are comprehensive applications that include a assortment of exploits created to just take advantage of vulnerabilities in commonly-made use of software program by scanning contaminated programs for distinct types of flaws and deploying extra malware.
The major infection process made use of by attackers to distribute exploit kits, in this circumstance the Rig Exploit Kit, is by way of compromised internet sites that, when visited, drops the exploit code to in the end send out the RedLine Stealer payload to carry out adhere to-on attacks.
The flaw in query is CVE-2021-26411 (CVSS score: 8.8), a memory corruption vulnerability impacting Internet Explorer that has been previously weaponized by North Korea-joined risk actors. It was resolved by Microsoft as section of its Patch Tuesday updates for March 2021.
“The RedLine Stealer sample shipped by RIG EK comes packed in a number of encryption levels […] to stay away from detection,” the Romanian cybersecurity agency famous, with the unpacking of the malware progressing as a result of as lots of as 6 phases.

RedLine Stealer, an info-stealing malware offered on underground community forums, arrives with features to exfiltrate passwords, cookies and credit card data saved in browsers, as effectively as crypto wallets, chat logs, VPN login credentials and text from information as for each commands acquired from a distant server.
This is considerably from the only campaign that involves the distribution of RedLine Stealer. In February 2022, HP in-depth a social engineering attack making use of pretend Windows 11 improve installers to trick Windows 10 users into downloading and executing the malware.
Discovered this report appealing? Stick to THN on Facebook, Twitter and LinkedIn to study much more unique material we post.
Some pieces of this article are sourced from:
thehackernews.com



 U.S Cybersecurity Agency Lists 2021’s Top 15 Most Exploited Software Vulnerabilities
U.S Cybersecurity Agency Lists 2021’s Top 15 Most Exploited Software Vulnerabilities