A new exploit has been devised to “unenroll” enterprise- or school-managed Chromebooks from administrative control.
Enrolling ChromeOS devices tends to make it possible to implement system procedures as set by the business via the Google Admin console, together with the functions that are offered to consumers.
“Every enrolled product complies with the insurance policies you set right up until you wipe or deprovision it,” Google states in its documentation.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
That is wherever the exploit – dubbed Shady Hacking 1nstrument Would make Machine Enrollment Retreat aka SH1MMER – comes in, allowing buyers to bypass these admin constraints.
The approach is also a reference to shim, a Return Products Authorization (RMA) disk image employed by services middle technicians to reinstall the running technique and operate diagnosis and repair service programs.
The Google-signed shim impression is a “combination of current Chrome OS factory bundle parts” – specifically a release graphic, a toolkit, and the firmware, amid other individuals – that can be flashed to a USB travel.
A Chromebook can then be booted in developer mode with the push picture to invoke the restoration alternatives. A shim picture can both be universal or particular to a Chromebook board.
SH1MMER usually takes edge of a modified RMA shim picture to create a restoration media for the Chromebook and writes it to a USB adhere. Accomplishing so calls for an on the web builder to obtain the patched version of the RMA shim with the exploit.
The up coming action involves launching the restoration manner on the Chromebook and plugging the USB adhere containing the graphic into the product to screen an altered restoration menu that enables people to totally unenroll the machine.
“It will now behave completely as if it is a personal laptop and no for a longer time have adware or blocker extensions,” the Mercury Workshop staff, which arrived up with the exploit, explained.
“RMA shims are a manufacturing facility instrument permitting sure authorization features to be signed, but only the KERNEL partitions are checked for signatures by the firmware,” the workforce even further elaborated. “We can edit the other partitions to our will as extensive as we take out the pressured readonly bit on them.”
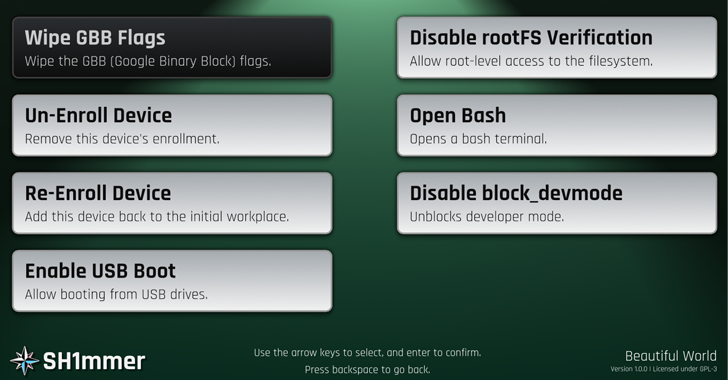
Also, the SH1MMER menu can be employed to re-enroll the machine, permit USB boot, open up a bash shell, and even enable root-stage accessibility to the ChromeOS operating process.
The Hacker Information has arrived at out to Google for remark, and we will update the story if we hear back.
Found this write-up exciting? Adhere to us on Twitter and LinkedIn to study a lot more exceptional content material we put up.
Some pieces of this write-up are sourced from:
thehackernews.com

 Prilex PoS Malware Evolves to Block Contactless Payments to Steal from NFC Cards
Prilex PoS Malware Evolves to Block Contactless Payments to Steal from NFC Cards