Vulnerable Redis expert services have been targeted by a “new, improved, hazardous” variant of a malware referred to as SkidMap that’s engineered to concentrate on a wide selection of Linux distributions.
“The malicious mother nature of this malware is to adapt to the technique on which it is executed,” Trustwave security researcher Radoslaw Zdonczyk mentioned in an examination released last 7 days.
Some of the Linux distribution SkidMap sets its eyes on incorporate Alibaba, Anolis, openEuler, EulerOS, Stream, CentOS, RedHat, and Rocky.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
SkidMap was very first disclosed by Development Micro in September 2019 as a cryptocurrency mining botnet with capabilities to load malicious kernel modules that can obfuscate its activities as well as observe the miner process.

The operators of the malware have also been discovered camouflaging their backup command-and-regulate (C2) IP tackle on the Bitcoin blockchain, evocative of a different botnet malware acknowledged as Glupteba.
“The procedure of fetching genuine-time facts from a decentralized and effectively uncensorable knowledge source to produce a C2 IP deal with can make the infection tricky to get down and would make pivoting the C2 IP handle very simple and speedy,” Akamai observed in February 2021.
The latest attack chain documented by Trustwave requires breaching improperly secured Redis server situations to deploy a dropper shell script that is made to distribute an ELF binary that masquerades as a GIF image file.
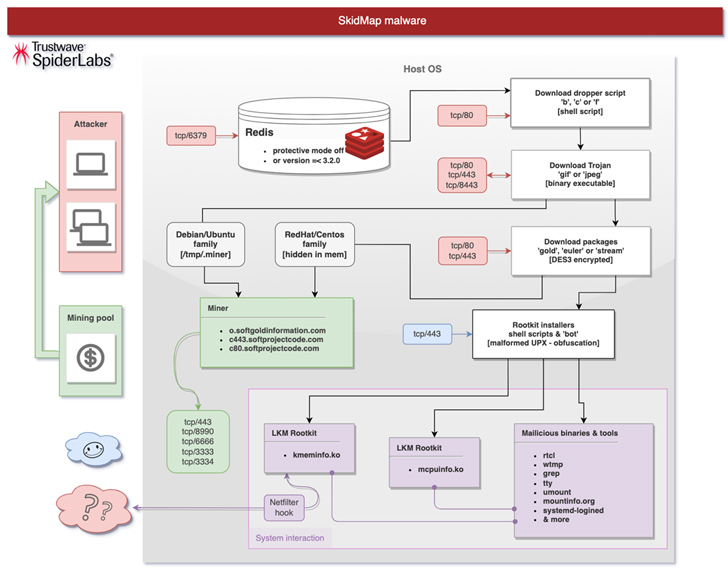
The binary then proceeds to add SSH keys to the “/root/.ssh/authoried_keys” file, disable SELinux, establish a reverse shell that pings an actor-managed server just about every 60 minutes, and finally down load an acceptable package deal (named gold, stream, or euler) dependent on the Linux distribution and the kernel made use of.

The deal, for its part, will come with numerous shell scripts to install the kernel modules and just take ways to cover up the tracks by purging logs, and start a botnet part able of retrieving more rootkit payloads: mcpuinfo.ko, to cover the miner course of action, and kmeminfo.ko, to review, modify, or fall network packets.
Also downloaded is the miner binary by itself, although in some variants, a “built-in miner from an extracted ‘GIF’ binary file” is made use of.
“The amount of progression of this malware is seriously large, and detecting it, particularly in much larger server infrastructures, can be quite tricky,” Zdonczyk reported. “When tests it on home personal computers, the only significant indicator that a little something was improper was the extreme operation of followers, and in the circumstance of laptops, the temperature of the situation.”
Found this posting appealing? Follow us on Twitter and LinkedIn to read through extra exclusive written content we post.
Some sections of this article are sourced from:
thehackernews.com


 FBI Alert: Crypto Scammers are Masquerading as NFT Developers
FBI Alert: Crypto Scammers are Masquerading as NFT Developers