Vietnamese community firms have been qualified as portion of an ongoing marketing campaign that deploys a novel backdoor termed SPECTRALVIPER.
“SPECTRALVIPER is a greatly obfuscated, earlier undisclosed, x64 backdoor that brings PE loading and injection, file upload and obtain, file and listing manipulation, and token impersonation capabilities,” Elastic Security Labs explained in a Friday report.
The attacks have been attributed to an actor it tracks as REF2754, which overlaps with a Vietnamese threat group acknowledged as APT32, Canvas Cyclone (previously Bismuth), Cobalt Kitty, and OceanLotus.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Meta, in December 2020, joined the pursuits of the hacking crew to a cybersecurity business named CyberOne Team.

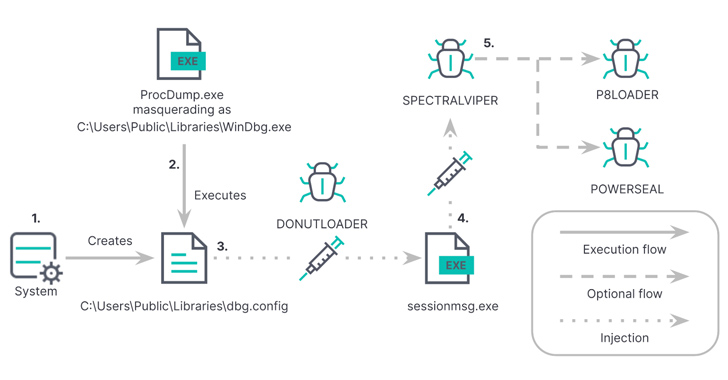
In the hottest infection flow unearthed by Elastic, the SysInternals ProcDump utility is leveraged to load an unsigned DLL file that includes DONUTLOADER, which, in transform, is configured to load SPECTRALVIPER and other malware this sort of as P8LOADER or POWERSEAL.
SPECTRALVIPER is built to make contact with an actor-managed server and awaits further more instructions though also adopting obfuscation techniques like management circulation flattening to resist examination.
P8LOADER, composed in C++, is able of launching arbitrary payloads from a file or from memory. Also made use of is a intent-crafted PowerShell runner named POWERSEAL which is equipped to operate equipped PowerShell scripts or commands.
REF2754 is said to share tactical commonalities with another team dubbed REF4322, which is identified to largely goal Vietnamese entities to deploy a write-up-exploitation implant referred to as PHOREAL (aka Rizzo).
The connections have elevated the probability that “each REF4322 and REF2754 exercise groups symbolize strategies planned and executed by a Vietnamese point out-affiliated menace.”
Approaching WEBINAR🔐 Mastering API Security: Comprehension Your Legitimate Attack Surface area
Discover the untapped vulnerabilities in your API ecosystem and choose proactive steps in the direction of ironclad security. Sign up for our insightful webinar!
Be part of the Session.wn-button,.wn-label,.wn-label:immediately afterdisplay:inline-block.check_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px stable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top rated-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-suitable-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-sizing:13pxmargin:20px 0font-body weight:600letter-spacing:.6pxcolor:#596cec.wn-label:right afterwidth:50pxheight:6pxcontent:”border-best:2px strong #d9deffmargin: 8px.wn-titlefont-sizing:21pxpadding:10px 0font-fat:900textual content-align:leftline-top:33px.wn-descriptiontextual content-align:leftfont-dimensions:15.6pxline-height:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-color:#4469f5font-dimensions:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-bodyweight:500letter-spacing:.2px
The results appear as the intrusion set dubbed REF2924 has been tied to nevertheless an additional piece of malware named SOMNIRECORD that employs DNS queries to connect with a remote server and bypass network security controls.
SOMNIRECORD, like NAPLISTENER, makes use of current open source assignments to hone its abilities, enabling it to retrieve details about the infected equipment, listing all running processes, deploy a web shell, and start any executable now existing in the technique.
“The use of open up source assignments by the attacker indicates that they are using measures to customize current equipment for their particular needs and may well be attempting to counter attribution attempts,” the corporation mentioned.
Located this posting intriguing? Adhere to us on Twitter and LinkedIn to study a lot more exclusive content we publish.
Some elements of this report are sourced from:
thehackernews.com

 New Critical MOVEit Transfer SQL Injection Vulnerabilities Discovered – Patch Now!
New Critical MOVEit Transfer SQL Injection Vulnerabilities Discovered – Patch Now!