Cybersecurity scientists have claimed an increase in TrueBot bacterial infections, generally concentrating on Mexico, Brazil, Pakistan, and the U.S.
Cisco Talos claimed the attackers driving the operation have moved from applying destructive e-mails to alternate supply approaches these kinds of as the exploitation of a now-patched distant code execution (RCE) flaw in Netwrix auditor as well as the Raspberry Robin worm.
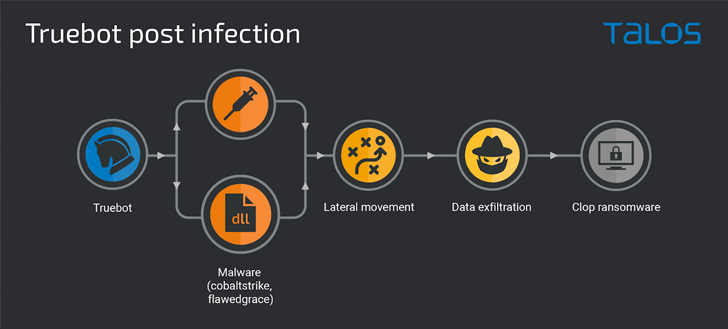
“Article-compromise exercise involved facts theft and the execution of Clop ransomware,” security researcher Tiago Pereira explained in a Thursday report.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
TrueBot is a Windows malware downloader that’s attributed to a danger actor tracked by Group-IB as Silence, a Russian-talking crew thought to share associations with Evil Corp (aka DEV-0243) and TA505.

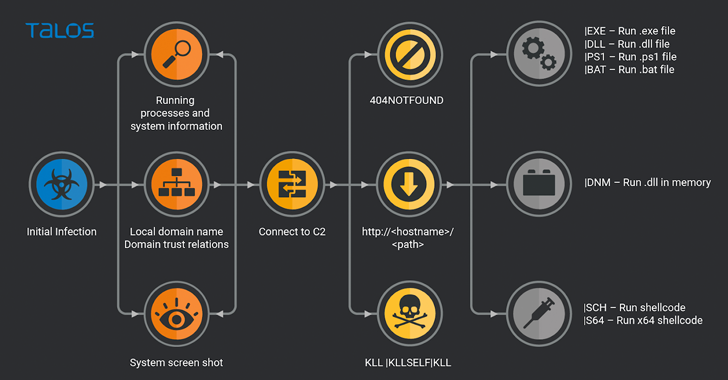
The initially-phase module capabilities as an entry issue for subsequent post-exploitation actions, which include info theft using a hitherto not known customized details exfiltration utility dubbed Teleport, the cybersecurity business said.
The use of Raspberry Robin – a worm generally unfold by way of contaminated USB drives – as a shipping and delivery vector for TrueBot was highlighted lately by Microsoft, which it mentioned is part of a “elaborate and interconnected malware ecosystem.”
In what is a more indicator of enmeshed collaboration with other malware families, Raspberry Robin has also been observed deploying FakeUpdates (aka SocGholish) on compromised systems, in the end top to ransomware-like habits connected to Evil Corp.
Microsoft is monitoring the operators of the USB-primarily based malware as DEV-0856 and the Clop ransomware attacks that come about by using Raspberry Robin and TrueBot less than the emerging danger cluster DEV-0950.
“DEV-0950 traditionally utilizes phishing to get the the greater part of their victims, so this notable shift to employing Raspberry Robin enables them to produce payloads to present bacterial infections and transfer their campaigns much more speedily to ransomware levels,” the Windows maker noted in Oct 2022.
The hottest results from Cisco Talos show that the Silence APT carried out a modest established of attacks amongst mid-August and September 2022 by abusing a critical RCE vulnerability in Netwrix auditor (CVE-2022-31199, CVSS rating: 9.8) to down load and operate TrueBot.
The truth that the bug was weaponized simply a thirty day period just after its general public disclosure by Bishop Fox in mid-July 2022 indicates that “attackers are not only on the lookout for new infection vectors, but are also in a position to promptly test them and include them into their workflow,” Pereira mentioned.
TrueBot infections in Oct, having said that, entailed the use of a diverse attack vector – i.e., Raspberry Robin – underscoring Microsoft’s assessment about the USB worm’s central purpose as a malware distribution system.
The principal functionality of TrueBot is to acquire facts from the host and deploy up coming-stage payloads these as Cobalt Strike, FlawedGrace, and Teleport. This is followed by the execution of the ransomware binary following harvesting related facts.
The Teleport details exfiltration tool is also noteworthy for its capability to limit add speeds and file sizes, thereby leading to the transmissions to go undetected by checking computer software. On top rated of that, it can erase its have presence from the device.
A closer glance at the commands issued via Teleport reveals that the plan is remaining solely made use of to collect files from OneDrive and Downloads folders as perfectly as the victim’s Outlook email messages.
“The Raspberry Robin shipping and delivery led to the creation of a botnet of in excess of 1,000 methods that is dispersed throughout the world, but with unique concentration on Mexico, Brazil, and Pakistan,” Pereira reported.
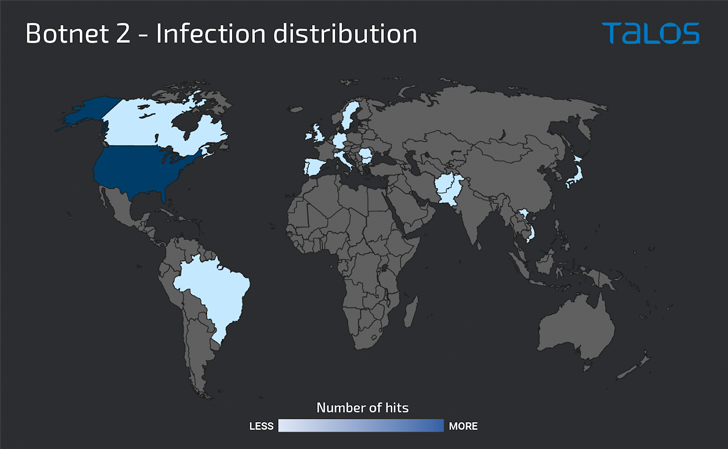
The attackers, having said that, surface to have switched to an unknown TrueBot distribution system starting in November, with the vector succeeding in co-opting about 500 internet-facing Windows servers located in the U.S., Canada, and Brazil into a botnet.
Uncovered this short article attention-grabbing? Follow us on Twitter and LinkedIn to browse much more special written content we publish.
Some elements of this post are sourced from:
thehackernews.com

 BEC Attacks Expand Beyond Email and Toward Mobile Devices
BEC Attacks Expand Beyond Email and Toward Mobile Devices