The U.K. Nationwide Cyber Security Centre (NCSC) is contacting on makers of good units to comply with new legislation that prohibits them from utilizing default passwords, helpful April 29, 2024.
“The law, regarded as the Product or service Security and Telecommunications Infrastructure act (or PSTI act), will aid buyers to pick smart products that have been created to give ongoing security against cyber attacks,” the NCSC stated.
To that conclude, companies are expected to not source units that use guessable default passwords, supply a level of speak to to report security issues, and state the period for which their equipment are predicted to obtain essential security updates.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Default passwords can not only be simply identified on line, they also act as a vector for danger actors to log in to gadgets for stick to-on exploitation. That explained, a distinctive default password is permissible underneath the legislation.

The regulation, which aims to enforce a set of least security requirements throughout the board and reduce susceptible products from getting corralled into a DDoS botnet like Mirai, applies to the subsequent products and solutions that can be linked to the internet –
- Clever speakers, intelligent TVs, and streaming devices
- Clever doorbells, child screens, and security cameras
- Cellular tablets, smartphones, and match consoles
- Wearable exercise trackers (like intelligent watches)
- Clever domestic appliances (these types of as light bulbs, plugs, kettles, thermostats, ovens, fridges, cleaners, and washing machines)
Businesses that fall short to adhere to the provisions of the PSTI act are liable to experience recalls and monetary penalties, attracting fines of up to £10 million ($12.5 million) or 4% of their global annual revenues, depending on whichever is higher.

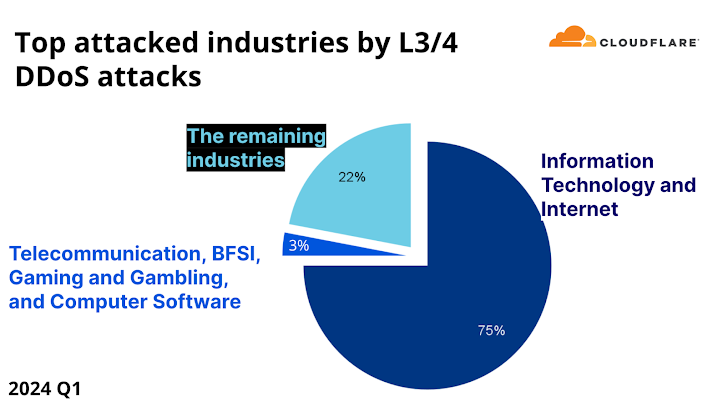
The enhancement makes the U.K. the very first region in the entire world to outlaw default usernames and passwords from IoT products. In accordance to Cloudflare’s DDoS threat report for Q1 2024, Mirai-based attacks carry on to be prevalent despite the primary botnet currently being taken down in 2016.
“4 out of just about every 100 HTTP DDoS attacks, and two out of each 100 L3/4 DDoS attacks are launched by a Mirai-variant botnet,” Omer Yoachimik and Jorge Pacheco said. “The Mirai resource code was created public, and above the yrs there have been many permutations of the original.”

It also follows a $196 million great issued by the U.S. Federal Communications Commission (FCC) in opposition to telecom carriers AT&T ($57 million), Dash ($12 million), T-Mobile ($80 million), and Verizon ($47 million) for illegally sharing customers’ serious-time place information without their consent to aggregators, who then offered the facts to third-party spot-dependent services companies.
“No a single who signed up for a mobile plan thought they have been supplying authorization for their phone corporation to sell a in-depth file of their movements to anybody with a credit history card,” U.S. Senator Ron Wyden, who revealed the apply in 2018, reported in a statement.
Identified this article appealing? Observe us on Twitter and LinkedIn to browse much more distinctive material we submit.
Some parts of this post are sourced from:
thehackernews.com


 Google Prevented 2.28 Million Malicious Apps from Reaching Play Store in 2023
Google Prevented 2.28 Million Malicious Apps from Reaching Play Store in 2023