A new security vulnerability has been disclosed in RARlab’s UnRAR utility that, if correctly exploited, could permit a remote attacker to execute arbitrary code on a method that depends on the binary.
The flaw, assigned the identifier CVE-2022-30333, relates to a path traversal vulnerability in the Unix variations of UnRAR that can be induced on extracting a maliciously crafted RAR archive.
Following accountable disclosure on Could 4, 2022, the shortcoming was dealt with by RarLab as aspect of edition 6.12 unveiled on May 6. Other versions of the computer software, which includes all those for Windows and Android operating methods, are not impacted.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“An attacker is capable to make information outdoors of the concentrate on extraction directory when an software or sufferer consumer extracts an untrusted archive,” SonarSource researcher Simon Scannell mentioned in a Tuesday report. “If they can produce to a regarded spot, they are probable to be capable to leverage it in a way primary to the execution of arbitrary commands on the procedure.”
It is really really worth pointing out that any software package that utilizes an unpatched model of UnRAR to extract untrusted archives is afflicted by the flaw.
This also consists of Zimbra collaboration suite, whereby the vulnerability could guide to pre-authenticated distant code execution on a susceptible instance, supplying the attacker full access to an email server and even abuse it to accessibility or overwrite other interior sources in the organization’s network.
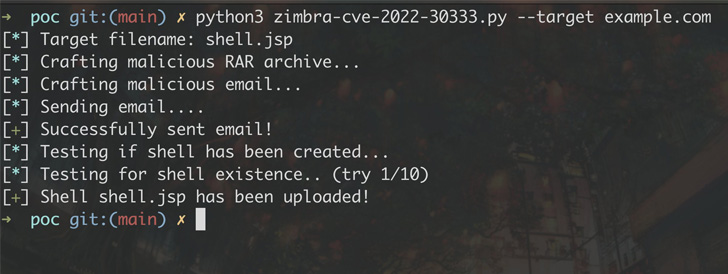 Image Supply: Simon Scannell
Image Supply: Simon Scannell
The vulnerability, at its coronary heart, relates to a symbolic hyperlink attack in which a RAR archive is crafted these that it contains a symlink that is a mix of the two forward slashes and backslashes (e.g., “……tmp/shell”) so as to bypass latest checks and extract it outside of the envisioned directory.

Additional specifically, the weak spot has to do with a purpose that is intended to change backslashes (”) to forward slashes (“https://thehackernews.com/”) so that a RAR archive made on Windows can be extracted on a Unix process, successfully altering the aforementioned symlink to “../../../tmp/shell.”
By having advantage of this conduct, an attacker can publish arbitrary data files any where on the goal filesystem, such as producing a JSP shell in Zimbra’s web directory and execute destructive instructions.
“The only necessity for this attack is that UnRAR is set up on the server, which is envisioned as it is necessary for RAR archive virus-scanning and spam-examining,” Scannell noted.
Located this post fascinating? Adhere to THN on Fb, Twitter and LinkedIn to examine additional distinctive content we submit.
Some components of this report are sourced from:
thehackernews.com


 Ransomware Suspected in Wiltshire Farm Foods Attack
Ransomware Suspected in Wiltshire Farm Foods Attack