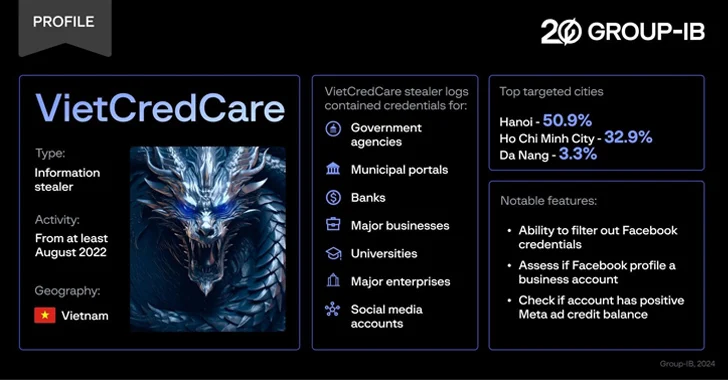
Fb advertisers in Vietnam are the target of a previously unfamiliar information and facts stealer dubbed VietCredCare at minimum due to the fact August 2022.
The malware is “noteworthy for its ability to automatically filter out Facebook session cookies and qualifications stolen from compromised products, and evaluate whether these accounts handle company profiles and if they preserve a optimistic Meta advertisement credit stability,” Singapore-headquartered Team-IB explained in a new report shared with The Hacker Information.
The conclusion purpose of the big-scale malware distribution plan is to facilitate the takeover of corporate Facebook accounts by focusing on Vietnamese people who deal with the Fb profiles of prominent firms and businesses.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Fb accounts that have been productively seized are then employed by the threat actors powering the operation to publish political written content or to propagate phishing and affiliate scams for monetary obtain.

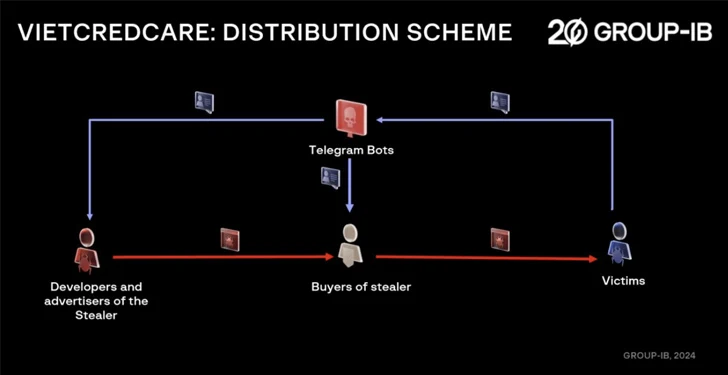
VietCredCare is presented to other aspiring cybercriminals beneath the stealer-as-a-support model and advertised on Facebook, YouTube, and Telegram. It is really assessed to be managed by Vietnamese-speaking men and women.
Customers possibly have the selection of obtaining obtain to a botnet managed by the malware’s builders, or procure entry to the supply code for resale or personal use. They are also presented a bespoke Telegram bot to handle the exfiltration and shipping of qualifications from an infected product.
The .NET-based mostly malware is distributed by way of hyperlinks to bogus websites on social media posts and prompt messaging platforms, masquerading as legitimate software program like Microsoft Business or Acrobat Reader to dupe visitors into installing them.
One particular of its main promoting factors is its ability to extract qualifications, cookies, and session IDs from web browsers like Google Chrome, Microsoft Edge, and Cốc Cốc, indicating its Vietnamese concentrate.
It can also retrieve a victim’s IP handle, test if a Facebook is a company profile, and evaluate no matter whether the account in dilemma is currently taking care of any adverts, even though simultaneously taking actions to evade detection by disabling the Windows Antimalware Scan Interface (AMSI) and introducing alone to the exclusion record of Windows Defender Antivirus.
“VietCredCare’s core functionality to filter out Fb qualifications puts corporations in equally the public and private sectors at risk of reputational and economic damages if their sensitive accounts are compromised,” Vesta Matveeva, head of the Significant-Tech Crime Investigation Office for APAC, stated.

Credentials belonging to various govt agencies, universities, e-commerce platforms, financial institutions, and Vietnamese organizations have been siphoned by using the stealer malware.
VietCredCare is also the latest addition to a prolonged record of stealer malware, such as Ducktail and NodeStealer,that has originated from the Vietnamese cyber felony ecosystem with the intent of concentrating on Facebook accounts.
“The stealer-as-a-company organization model permits threat actors with little to no technological techniques to enter the cybercrime area, which effects in extra harmless victims remaining harmed,” Group-IB mentioned.
Observed this post intriguing? Stick to us on Twitter and LinkedIn to read a lot more special content we put up.
Some sections of this write-up are sourced from:
thehackernews.com

 Signal Introduces Usernames, Allowing Users to Keep Their Phone Numbers Private
Signal Introduces Usernames, Allowing Users to Keep Their Phone Numbers Private