VMware ESXi hypervisors are the target of a new wave of attacks designed to deploy ransomware on compromised systems.
“These attack campaigns appear to exploit CVE-2021-21974, for which a patch has been available since February 23, 2021,” the Computer Emergency Response Team (CERT) of France said in an advisory on Friday.
VMware, in its own alert released at the time, described the issue as an OpenSLP heap-overflow vulnerability that could lead to the execution of arbitrary code.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“A malicious actor residing within the same network segment as ESXi who has access to port 427 may be able to trigger the heap-overflow issue in OpenSLP service resulting in remote code execution,” the virtualization services provider noted.
French cloud services provider OVHcloud said the attacks are being detected globally with a specific focus on Europe. It’s being suspected that the attacks are related to a new Rust-based ransomware strain called Nevada that emerged on the scene in December 2022.
Other ransomware families that are known to have embraced Rust in recent months include BlackCat, Hive, Luna, Nokoyawa, RansomExx, and Agenda.
“The actors are inviting both Russian- and English-speaking affiliates to collaborate with a big number of Initial Access Brokers (IABs) in [the] dark web,” Resecurity said last month.
“Notably, the group behind the Nevada Ransomware is also buying compromised access by themselves, the group has a dedicated team for post-exploitation, and for conducting network intrusions into the targets of interest.”
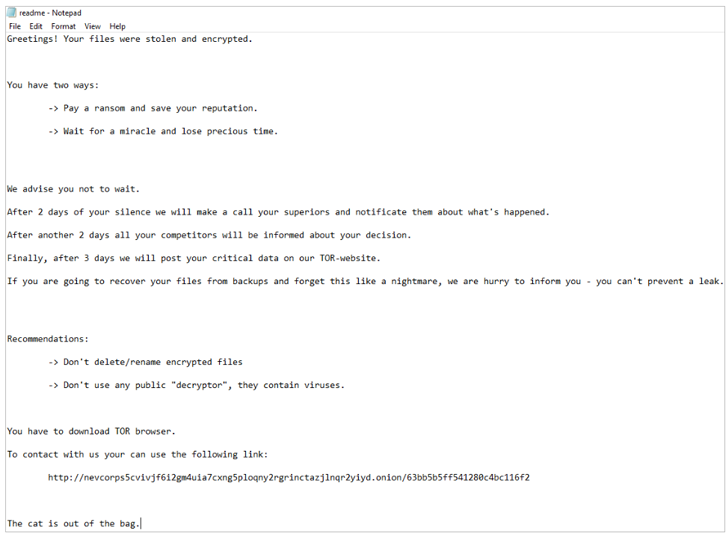
However, Bleeping Computer reports that the ransom notes seen in the attacks bear no similarities to Nevada ransomware, adding the strain is being tracked under the name ESXiArgs.
Users are recommended to upgrade to the latest version of ESXi to mitigate potential threats as well as restrict access to the OpenSLP service to trusted IP addresses.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
Some parts of this article are sourced from:
thehackernews.com


 Warning: Hackers Actively Exploiting Zero-Day in Fortra’s GoAnywhere MFT
Warning: Hackers Actively Exploiting Zero-Day in Fortra’s GoAnywhere MFT