A group of teachers from Northeastern University and KU Leuven has disclosed a basic design flaw in the IEEE 802.11 Wi-Fi protocol common, impacting a large array of devices managing Linux, FreeBSD, Android, and iOS.
Effective exploitation of the shortcoming could be abused to hijack TCP connections or intercept shopper and web visitors, researchers Domien Schepers, Aanjhan Ranganathan, and Mathy Vanhoef reported in a paper printed this 7 days.
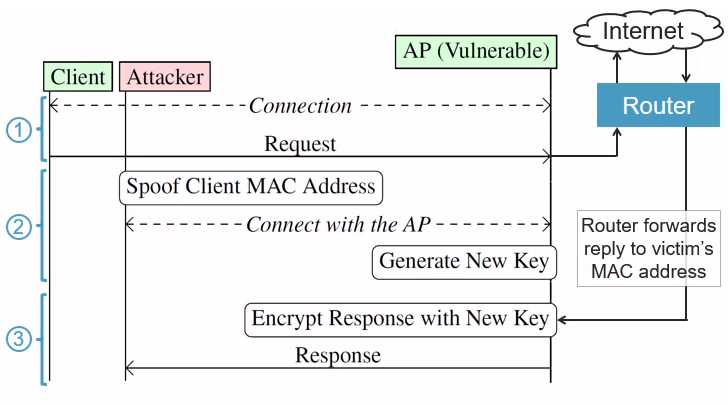
The strategy exploits electric power-help save mechanisms in endpoint equipment to trick accessibility details into leaking knowledge frames in plaintext, or encrypt them using an all-zero important.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“The unprotected character of the energy-save little bit in a frame’s header […] also enables an adversary to pressure queue frames meant for a precise shopper resulting in its disconnection and trivially executing a denial-of-company attack,” the researchers famous.
In other phrases, the intention is to leak frames from the access issue destined to a victim shopper station by having edge of the reality that most Wi-Fi stacks do not adequately dequeue or purge their transmit queues when the security context improvements.
In addition to manipulating the security context to leak frames from the queue, an attacker can override the client’s security context used by an obtain point to acquire packets meant for the victim. This attack pre-supposes that the specific party is connected to a hotspot-like network.
“The core concept at the rear of the attack is that the fashion in which customers are authenticated is unrelated to how packets are routed to the appropriate Wi-Fi customer,” Vanhoef spelled out.
“A destructive insider can abuse this to intercept info to a Wi-Fi customer by disconnecting a sufferer and then connecting underneath the MAC handle of the target (employing the qualifications of the adversary). Any packets that ended up however underway to the sufferer, these kinds of web site info that the sufferer was however loading, will now be gained by the adversary as a substitute.”
Cisco, in an informational advisory, described the vulnerabilities as an “opportunistic attack and the info acquired by the attacker would be of negligible worth in a securely configured network.”
Having said that, the corporation acknowledged that the attacks presented in the analyze may well be productive towards Cisco Wi-fi Access Stage goods and Cisco Meraki products with wireless abilities.
To lower the likelihood of this sort of attacks, it is really advised to implement transport layer security (TLS) to encrypt info in transit and utilize plan enforcement mechanisms to prohibit network obtain.
THN WEBINARBecome an Incident Reaction Pro!
Unlock the secrets to bulletproof incident response – Grasp the 6-Period approach with Asaf Perlman, Cynet’s IR Chief!
Really don’t Miss out on Out – Save Your Seat!
The conclusions arrive months immediately after researchers Ali Abedi and Deepak Vasisht demonstrated a place-revealing privacy attack referred to as Wi-Peep that also exploits the 802.11 protocol’s electrical power-conserving system to localize goal products.
The investigation also follows other modern scientific studies that have leveraged the Google Geolocation API to start locale spoofing attacks in city locations, not to mention use Wi-Fi signals to detect and map human movement in a place.
Discovered this article attention-grabbing? Comply with us on Twitter and LinkedIn to examine much more distinctive content we post.
Some parts of this report are sourced from:
thehackernews.com


 3CX CEO suggests state-sponsored hackers behind supply chain malware attack
3CX CEO suggests state-sponsored hackers behind supply chain malware attack