Cybersecurity companies ESET and Broadcom’s Symantec mentioned they discovered a new data wiper malware employed in contemporary attacks from hundreds of equipment in Ukraine, as Russian forces formally launched a total-scale military services operation versus the state.
The Slovak business dubbed the wiper “HermeticWiper” (aka KillDisk.NCV), with a person of the malware samples compiled on December 28, 2021, implying that preparations for the attacks may possibly have been underway for nearly two months.
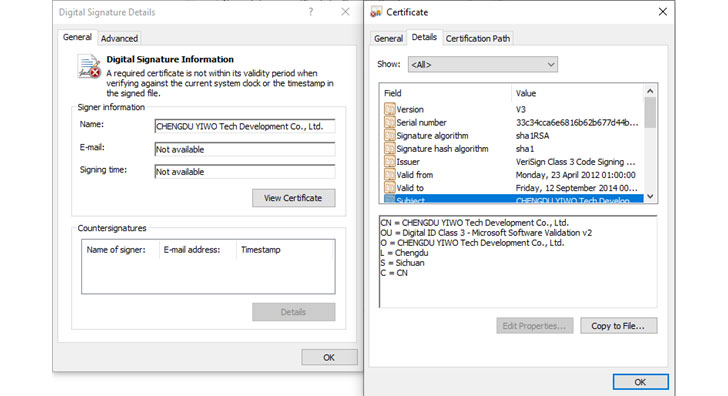
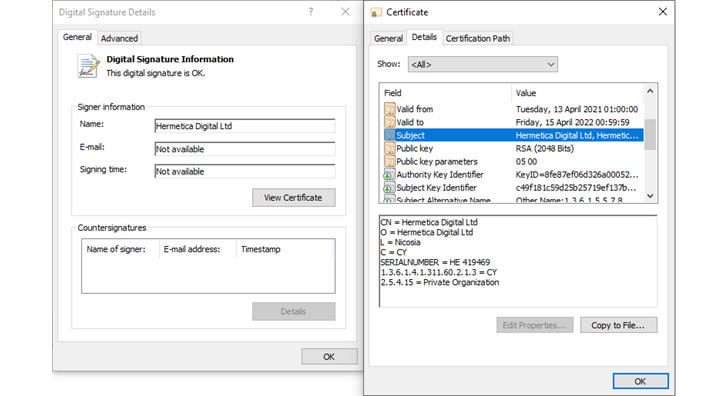
“The wiper binary is signed using a code signing certification issued to Hermetica Digital Ltd,” ESET explained in a sequence of tweets. “The wiper abuses legitimate motorists from the EaseUS Partition Learn software package in buy to corrupt data. As a remaining stage the wiper reboots [the] computer.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
At least one of the intrusions concerned deploying the malware immediately from the Windows domain controller, indicating that the attackers experienced taken control of the goal network.
The scale and the impression of the details-wiping attacks stays unfamiliar as yet, as is the identification of the risk actor powering the bacterial infections. But the progress marks the 2nd time this year that a harmful malware has been deployed on Ukrainian personal computer units following the WhisperGate procedure in mid-January.
The wiper attacks also stick to a 3rd “enormous” wave of dispersed denial-of-service (DDoS) attacks that strike several Ukrainian government and banking institutions on Wednesday, knocking out online portals for the Ministry of Foreign Affairs, Cupboard of Ministers, and Rada, the country’s parliament.
Final 7 days, two of the largest Ukrainian banks, PrivatBank and Oschadbank, as very well as the websites of the Ukrainian Ministry of Defense and the Armed Forces suffered outages as a result of a DDoS attack from unidentified actors, prompting the U.K. and U.S. governments to level the fingers at the Russian Main Intelligence Directorate (GRU), an allegation the Kremlin has denied.
Strategies that use DDoS attacks provide torrents of junk site visitors that are meant to overwhelm targets with the purpose of rendering them inaccessible. A subsequent evaluation of the February 15 incidents by the CERT-UA uncovered that they have been carried out working with botnets these as Mirai and Mēris by leveraging compromised MikroTik routers and other IoT products.
What’s far more, information programs belonging to Ukraine’s state institutions are claimed to have been unsuccessfully specific in as numerous as 121 cyber attacks in January 2022 on your own.
Which is not all. Cybercriminals on the dark web are hunting to capitalize on the ongoing political tensions by advertising databases and network accesses that contains facts on Ukrainian citizens and critical infra entities on RaidForums and Free Civilian marketplaces in “hopes of getting high income,” according to a report printed by Accenture earlier this 7 days.
The continual onslaught of disruptive malicious cyber functions since the start off of the calendar year has also led the Ukrainian law enforcement authority to paint the attacks as an hard work to unfold stress, undermine assurance in the state’s potential to protect its citizens, and destabilize its unity.
“Ukraine is struggling with makes an attempt to systematically sow panic, spread pretend info and distort the authentic condition of affairs,” the Security Services of Ukraine (SSU) mentioned on February 14. “All this merged is practically nothing far more than another significant wave of hybrid warfare.”
Observed this write-up attention-grabbing? Comply with THN on Facebook, Twitter and LinkedIn to read more special information we publish.
Some components of this write-up are sourced from:
thehackernews.com




 Samsung Shattered Encryption on 100M Phones
Samsung Shattered Encryption on 100M Phones