A new report from XM Cyber has found – among other insights – a dramatic gap between where most organizations focus their security efforts, and where the most serious threats actually reside.
The new report, Navigating the Paths of Risk: The State of Exposure Management in 2024, is based on hundreds of thousands of attack path assessments conducted by the XM Cyber platform during 2023. These assessments uncovered over 40 million exposures that affected millions of business-critical assets. Anonymized data regarding these exposures was then provided to the Cyentia Institute for independent analysis. To read the full report, check it out here.
.ebook-details { padding: 20px 0 0; }.ebook-image img { border-radius: 5px; } .xm_container {display: flex; align-items: center; margin: 20px 10px 30px 0; background: #f9fbff; color: #160755; padding: 0 20px; border: 2px solid #d9deff; border-radius: 10px; text-align: left; box-shadow: 5px 5px 0 #e2ebff; -webkit-border-top-left-radius: 15px; -moz-border-radius-topleft: 15px; -webkit-border-bottom-right-radius: 15px; -moz-border-radius-bottomright: 15px;} .ebook-image {flex: 0 0 250px;margin-right: 20px;} .ebook-details { flex: 1; }.ebook-details ul { margin: 15px; } .ebook-details ul li { margin-bottom: 5px; } @media (max-width: 600px) { .xm_container { flex-direction: column; } .ebook-image { margin-right: 0; margin-bottom: 20px; } }


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Download the report to discover:
- Key findings on the types of exposures putting organizations at greatest risk of breach.
- The state of attack paths between on-prem and cloud networks.
- Top attack techniques seen in 2023.
- How to focus on what matters most, and remediate high-impact exposure risks to your critical assets.
The findings shine a critical light on the continuing over-emphasis on remediating CVEs in cybersecurity programs. In fact, XM Cyber found that CVE-based vulnerabilities account for less than 1% of the average organizations’ On-prem exposure landscape. Even when factoring in high-impact exposures that present a risk of compromise to business-critical assets, these CVEs still represent only a small percentage (11%) of the exposure risk profile.
Where does the lion’s share of risk actually lie? Let’s dig deeper into the results:
CVEs: Not Necessarily Exposures
When analyzing the On-premises infrastructure, of the vast majority of organizations (86%) the XM Cyber report found, not surprisingly, that remote code executable vulnerabilities accounted (as mentioned above) for less than 1% of all exposures and only 11% of critical exposures.
The research found that identity and credential misconfigurations represent a staggering 80% of security exposures across organizations, with a third of these exposures putting critical assets at direct risk of breach – a gaping attack vector actively being exploited by adversaries.
Thus, the report makes it clear that while patching vulnerabilities is important, it’s not enough. More prevalent threats like attackers poisoning shared folders with malicious code (taint shared content) and using common local credentials on multiple devices expose a much larger share of critical assets (24%) compared to CVEs.
Thus, security programs need to extend far beyond patching CVEs. Good cyber hygiene practices and a focus on mitigating choke points and exposures like weak credential management are crucial.

Don’t Sweat Dead Ends, Hunt High-Impact Choke Points
Traditional security tries to fix every vulnerability, but XM Cyber’s report shows that 74% of exposures are actually dead ends for attackers – offering them minimal onward or lateral movement. This makes these vulnerabilities, exposures, and misconfiguration less critical to your remediation efforts, allowing more time to focus on the real issues that present a validated threat to critical assets.
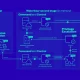
The remaining 26% of exposure discovered in the report would allow adversaries to propagate their attacks onward toward critical assets. The XM Cyber Attack Graph Analysis(™) identifies the key intersections where multiple attack paths toward critical assets converge as “choke points”. The report highlights that only 2% of exposures reside on “choke points”. Giving security teams a far smaller subset of high-impact exposures to focus their remediation efforts on. These “choke points” – are highlighted in yellow & red on the graph below. They are especially dangerous because compromising just one can expose a significant portion of critical assets. In fact, the report found that 20% of choke points expose 10% or more of critical assets. Thus, identifying attack paths and homing in on high-risk choke points can give defenders a bigger bang for their buck – reducing risk much more efficiently. To learn more about choke points, check out this article.

Finding and Categorizing Exposures: Focus on Critical Assets
Where are exposures and how do attackers exploit them? Traditionally, the attack surface is seen as everything in the IT environment. However, the report shows that effective security requires understanding where valuable assets reside and how they are exposed.
For example, the report analyzes the distribution of potential attack points across environments – finding that not all entities are vulnerable (see the graph below). A more critical metric is exposure to critical assets. Cloud environments hold the most critical asset exposures, followed by Active Directory (AD) and IT/Network devices.
It’s worth drilling down into the extreme vulnerability of organizational AD. Active Directory remains the cornerstone of organizational identity management – yet the report found that 80% of all security exposures identified stem from Active Directory misconfigurations or weaknesses. Even more concerning, one-third of all critical asset vulnerabilities can be traced back to identity and credential problems within Active Directory.
What’s the takeaway here? Security teams are often organized by critical asset categories. While this might be sufficient for managing the overall number of entities, it can miss the bigger picture. Critical exposures, though fewer, pose a much higher risk and require dedicated focus. (To help keep you on track with addressing AD security issues, we recommend this handy AD best practices security checklist.)

Different Needs for Different Industries
The report also analyzes differing cybersecurity risks across industries. Industries with a greater number of entities (potential attack points) tend to have more vulnerabilities. Healthcare, for example, has 5 times the exposure of Energy and Utilities.
However, the key risk metric is the proportion of exposures that threaten critical assets. Here, the picture flips. Transportation and Energy have a much higher percentage of critical exposures, despite having fewer overall vulnerabilities. This means they hold a higher concentration of critical assets that attackers might target.
The takeaway is that different industries require different security approaches. Financial firms have more digital assets but a lower critical exposure rate compared to Energy. Understanding the industry-specific attack surface and the threats it faces is crucial for an effective cybersecurity strategy.

The Bottom Line
A final key finding demonstrates that exposure management can’t be a one-time or annual project. It’s an ever-changing, continuous process to drive improvements. Yet today’s over-focus on patching vulnerabilities (CVEs) leads to neglect of more prevalent threats.
Today’s security ecosystem and threat landscape are not yesterday’s. It’s time for a cybersecurity paradigm shift. Instead of patching every vulnerability, organizations need to prioritize the high-impact exposures that offer attackers significant onward and lateral movement within a breached network – with a special focus on the 2% of exposures that reside on “choke points” where remediating key weakness in your environment will have the most positive reduction in your overall risk posture.
The time has come to move beyond a check-the-box mentality and focus on real-world attack vectors.
Note: This article was expertly written by Dale Fairbrother, Senior Product Marketing Manager at XM Cyber.
.ebook-details { padding: 20px 0 0; }.ebook-image img { border-radius: 5px; } .xm_container {display: flex; align-items: center; margin: 20px 10px 30px 0; background: #f9fbff; color: #160755; padding: 0 20px; border: 2px solid #d9deff; border-radius: 10px; text-align: left; box-shadow: 5px 5px 0 #e2ebff; -webkit-border-top-left-radius: 15px; -moz-border-radius-topleft: 15px; -webkit-border-bottom-right-radius: 15px; -moz-border-radius-bottomright: 15px;} .ebook-image {flex: 0 0 250px;margin-right: 20px;} .ebook-details { flex: 1; }.ebook-details ul { margin: 15px; } .ebook-details ul li { margin-bottom: 5px; } @media (max-width: 600px) { .xm_container { flex-direction: column; } .ebook-image { margin-right: 0; margin-bottom: 20px; } }

The State of Exposure Management report’s findings are based on data from the XM Cyber Continuous Exposure Management Platform that was analyzed independently by the Cyentia Institute. Grab your free report here.
Found this article interesting? This article is a contributed piece from one of our valued partners. Follow us on Twitter and LinkedIn to read more exclusive content we post.
Some parts of this article are sourced from:
thehackernews.com


 China-Linked Hackers Adopt Two-Stage Infection Tactic to Deploy Deuterbear RAT
China-Linked Hackers Adopt Two-Stage Infection Tactic to Deploy Deuterbear RAT