A newly found Magecart skimming campaign has its roots in a earlier attack exercise going all the way back to November 2021.
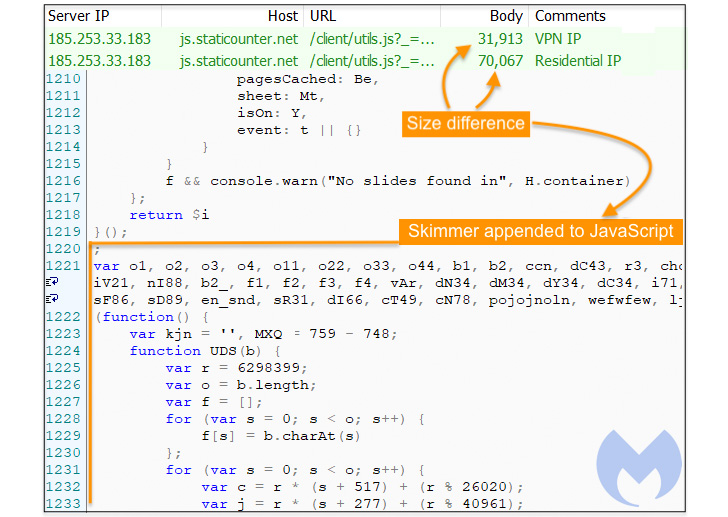
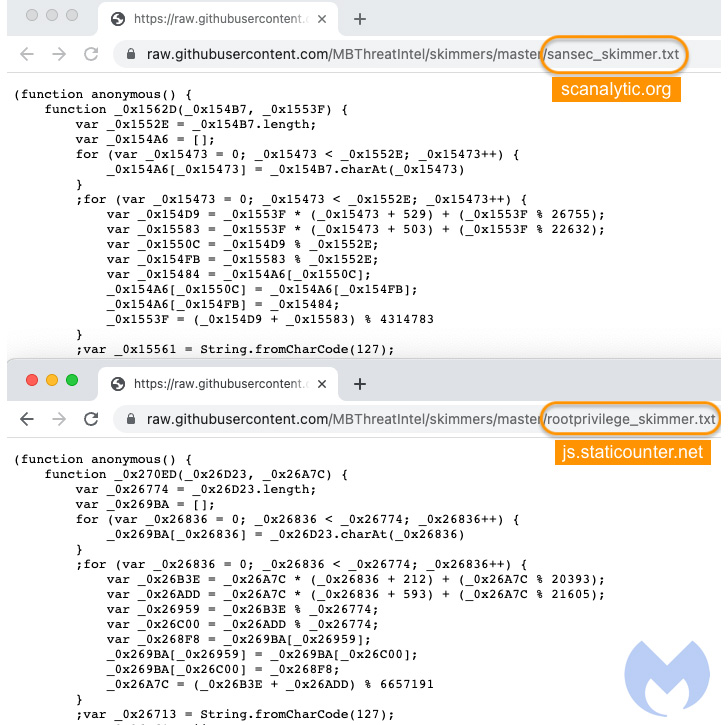
To that finish, it has come to mild that two malware domains determined as hosting credit card skimmer code — “scanalytic[.]org” and “js.staticounter[.]net” — are section of a broader infrastructure utilized to carry out the intrusions, Malwarebytes reported in a Tuesday examination.
“We were being equipped to connect these two domains with a former marketing campaign from November 2021 which was the initial instance to our awareness of a skimmer examining for the use of virtual devices,” Jérôme Segura stated. “Even so, both of those of them are now devoid of VM detection code. It truly is unclear why the danger actors taken off it, except probably it prompted a lot more issues than positive aspects.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The earliest evidence of the campaign’s action, primarily based on the added domains uncovered, suggests it dates back again to at least May perhaps 2020.
Magecart refers to a cybercrime syndicate comprised of dozens of subgroups that focus in cyberattacks involving electronic credit score card theft by injecting JavaScript code on e-commerce storefronts, typically on checkout internet pages.
This performs by operatives attaining accessibility to internet websites possibly immediately or by using 3rd-party companies that supply software to the specific web sites.
When the attacks gained prominence in 2015 for singling out the Magento e-commerce system (the title Magecart is a portmanteau of “Magento” and “purchasing cart”), they have due to the fact expanded to other choices, like a WordPress plugin named WooCommerce.

According to a report published by Sucuri in April 2022, WordPress has emerged as the leading CMS platform for credit rating card skimming malware, outpacing Magento as of July 2021, with skimmers concealed in the websites in the variety of fake pictures and seemingly innocuous JavaScript concept documents.
What is extra, WordPress internet sites accounted for 61% of recognised credit history card skimming malware detections in the course of the 1st five months of 2022, adopted by Magento (15.6%), OpenCart (5.5%), and other individuals (17.7%).
“Attackers adhere to the revenue, so it was only a make a difference of time just before they shifted their focus toward the most well known e-commerce platform on the web,” Sucuri’s Ben Martin observed at the time.
Identified this post fascinating? Adhere to THN on Fb, Twitter and LinkedIn to read much more exceptional written content we submit.
Some areas of this posting are sourced from:
thehackernews.com


 Euro Cops Dismantle Multimillion-Dollar Phishing Gang
Euro Cops Dismantle Multimillion-Dollar Phishing Gang