A formerly undocumented Windows-based mostly info stealer named ThirdEye has been identified in the wild with capabilities to harvest sensitive details from infected hosts.
Fortinet FortiGuard Labs, which built the discovery, explained it uncovered the malware in an executable that masqueraded as a PDF file with a Russian identify “CMK Правила оформления больничных листов.pdf.exe,” which translates to “CMK Policies for issuing sick leaves.pdf.exe.”
The arrival vector for the malware is presently mysterious, while the nature of the lure factors to it becoming utilised in a phishing campaign. The very initially ThirdEye sample was uploaded to VirusTotal on April 4, 2023, with fairly much less characteristics.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The evolving stealer, like other malware households of its type, is equipped to obtain technique metadata, like BIOS launch day and seller, total/free disk area on the C push, at this time running procedures, sign-up usernames, and volume facts. The amassed particulars are then transmitted to a command-and-control (C2) server.

A notable trait of the malware is that it uses the string “3rd_eye” to beacon its presence to the C2 server.
There are no symptoms to counsel that ThirdEye has been utilized in the wild. That having said, provided that a vast majority of the stealer artifacts ended up uploaded to VirusTotal from Russia, it’s very likely that the destructive action is aimed at Russian-talking corporations.
“While this malware is not regarded subtle, it truly is created to steal numerous facts from compromised machines that can be applied as stepping-stones for potential attacks,” Fortinet scientists explained, including the collected information is “valuable for understanding and narrowing down potential targets.”
The progress will come as trojanized installers for the preferred Tremendous Mario Bros video game franchise hosted on sketchy torrent web pages are remaining used to propagate cryptocurrency miners and an open up-source stealer written in C# referred to as Umbral that exfiltrates knowledge of curiosity applying Discord Webhooks.
“The combination of mining and thieving things to do potential customers to fiscal losses, a significant decline in the victim’s system effectiveness, and the depletion of valuable process resources,” Cyble stated.
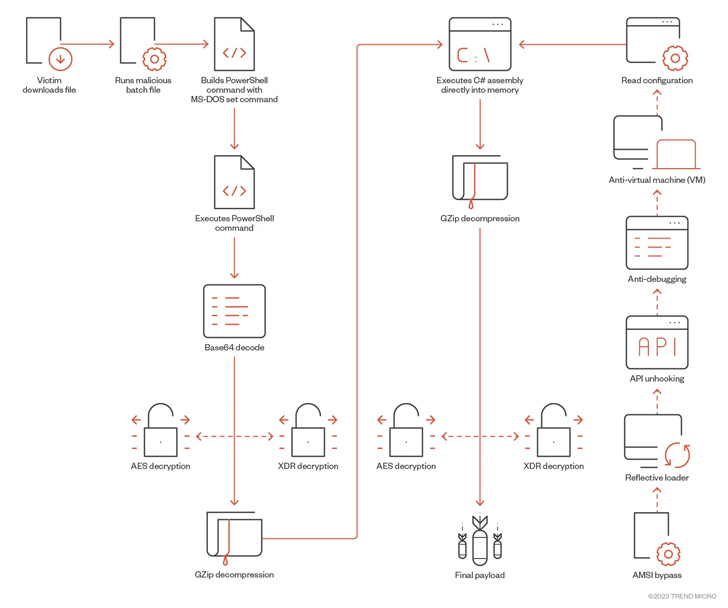
Movie sport end users have also been targeted with Python-primarily based ransomware and a remote entry trojan dubbed SeroXen, which has been observed to consider gain of a professional batch file obfuscation motor recognized as ScrubCrypt (aka BatCloak) to evade detection. Proof displays that actors connected with SeroXen’s growth have also contributed to the generation of ScrubCrypt.

The malware, which was marketed for sale on a clearnet web site that was registered on March 27, 2023 prior to its shutdown in late Could, has additional been promoted on Discord, TikTok, Twitter, and YouTube. A cracked model of SeroXen has due to the fact discovered its way to criminal message boards.
“Persons are strongly encouraged to adopt a skeptical stance when encountering one-way links and software package offers related with terms these as ‘cheats,’ ‘hacks,’ ‘cracks,’ and other pieces of software program related to gaining a competitive edge,” Pattern Micro famous in a new assessment of SeroXen.
“The addition of SeroXen and BatCloak to the malware arsenal of destructive actors highlights the evolution of FUD obfuscators with a small barrier to entry. The virtually-newbie strategy of using social media for intense promotion, thinking of how it can be very easily traced, makes these developers look like novices by state-of-the-art risk actors’ specifications.”
Identified this write-up attention-grabbing? Adhere to us on Twitter and LinkedIn to browse a lot more special written content we submit.
Some pieces of this posting are sourced from:
thehackernews.com

 Alert: New Electromagnetic Attacks on Drones Could Let Attackers Take Control
Alert: New Electromagnetic Attacks on Drones Could Let Attackers Take Control