An rising Android banking trojan dubbed Nexus has by now been adopted by numerous risk actors to goal 450 monetary apps and carry out fraud.
“Nexus seems to be in its early phases of enhancement,” Italian cybersecurity organization Cleafy reported in a report printed this week.
“Nexus offers all the principal options to conduct ATO attacks (Account Takeover) towards banking portals and cryptocurrency providers, these as credentials thieving and SMS interception.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The trojan, which appeared in a variety of hacking discussion boards at the commence of the year, is marketed as a membership service to its clientele for a regular monthly charge of $3,000. Aspects of the malware were 1st documented by Cyble previously this month.
Even so, there are indications that the malware could have been applied in genuine-earth attacks as early as June 2022, at minimum 6 months before its formal announcement on darknet portals.
It really is also mentioned to overlap with a further banking trojan dubbed SOVA, reusing sections of its supply code and incorporating a ransomware module that appears to be under lively development.
A level really worth mentioning in this article is that Nexus is the identical malware that Cleafy initially categorized as a new variant of SOVA (dubbed v5) in August 2022.
Curiously, the Nexus authors have laid out express policies that prohibit the use of its malware in Azerbaijan, Armenia, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Uzbekistan, Ukraine, and Indonesia.
The malware, like other banking trojans, consists of characteristics to consider more than accounts relevant to banking and cryptocurrency providers by carrying out overlay attacks and keylogging to steal users’ credentials.
WEBINARDiscover the Hidden Dangers of 3rd-Party SaaS Apps
Are you mindful of the hazards connected with 3rd-party app obtain to your firm’s SaaS applications? Sign up for our webinar to discover about the styles of permissions remaining granted and how to lessen risk.
RESERVE YOUR SEAT
Also, it is capable of studying two-factor authentication (2FA) codes from SMS messages and the Google Authenticator application through the abuse of Android’s accessibility products and services.
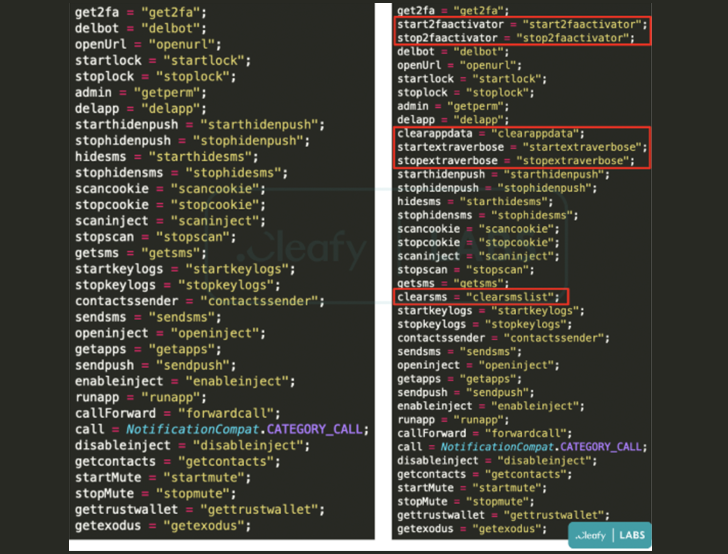
Some new additions to the record of functionalities is its capacity to remove received SMS messages, activate or end the 2FA stealer module, and update by itself by periodically pinging a command-and-command (C2) server.
“The [Malware-as-a-Service] design makes it possible for criminals to monetize their malware a lot more successfully by furnishing a all set-created infrastructure to their prospects, who can then use the malware to attack their targets,” the scientists reported.
Located this article intriguing? Comply with us on Twitter and LinkedIn to browse much more distinctive written content we publish.
Some components of this posting are sourced from:
thehackernews.com

 Windows, macOS, and Tesla exploits debuted at Pwn2Own hacking contest
Windows, macOS, and Tesla exploits debuted at Pwn2Own hacking contest