The npm registry for the Node.js JavaScript runtime environment is inclined to what’s known as a manifest confusion attack that could most likely make it possible for risk actors to conceal malware in task dependencies or perform arbitrary script execution for the duration of set up.
“A npm package’s manifest is posted independently from its tarball,” Darcy Clarke, a former GitHub and npm engineering manager, explained in a technological produce-up printed final 7 days. “Manifests are hardly ever thoroughly validated versus the tarball’s contents.”
“The ecosystem has broadly assumed the contents of the manifest and tarball are dependable,” Clarke included.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The trouble, at its main, stems from the reality that the manifest and bundle metadata are decoupled and that they are hardly ever cross-referenced from a single another, thereby foremost to unpredicted habits and misuse when there is a mismatch.
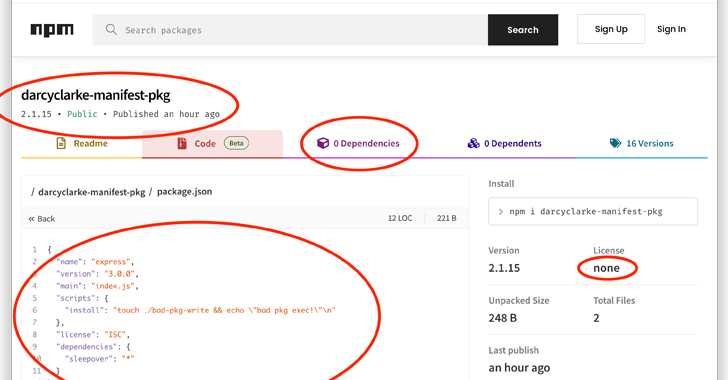
As a final result, a danger actor could exploit this loophole to publish a module with a manifest file (deal.json) that incorporates concealed dependencies as properly as operate set up scripts, which could then pave the way for a provide chain attack and the poisoning of a developer’s setting.
“Manifest confusion gets problematic in advancement environments without productive DevSecOps workflows and tooling in put, in particular when programs blindly believe in application manifests rather than the precise (susceptible or destructive) data files contained within open source offers,” Sonatype researcher and journalist Ax Sharma mentioned.
The locating underscores the fact that metadata contained within just deal manifest files alone are not able to be relied upon when downloading a offer from the open up-supply repository, necessitating that customers get techniques to scan offers for any anomalous options and exploits.
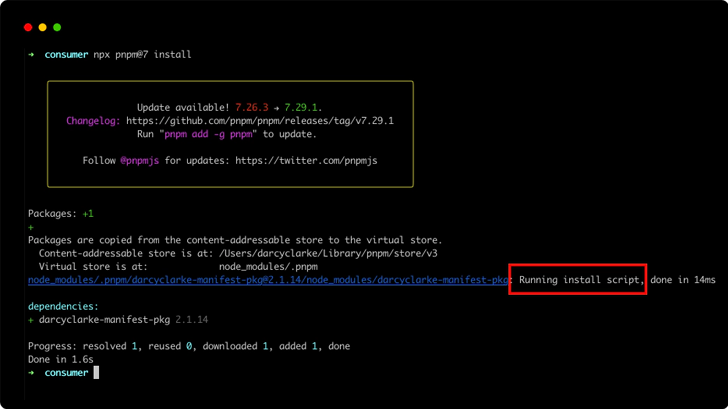
GitHub, per Clarke, is said to be informed of the issue since at minimum early November 2022, with the Microsoft subsidiary stating it plans to address it internally as of March 2023. The issue, nevertheless, continues to be unresolved to day.
In the absence of an official resolve, security researcher Felix Pankratz has designed out there a Python script that can be utilised to examination for mismatches involving the manifests in npm modules.
The enhancement also arrives as developer security organization Snyk, in partnership with Redhunt Labs, examined 11,900 repositories from the major 1,000 GitHub businesses for insecure dependencies, uncovering 1,229,601 flaws in 15,584 vulnerable dependency data files.
Forthcoming WEBINAR🔐 Privileged Access Administration: Understand How to Conquer Key Challenges
Explore different ways to conquer Privileged Account Management (PAM) problems and amount up your privileged entry security approach.
Reserve Your Place
“Deserialization of untrusted facts was the most common vulnerability style with a whopping 130,831 occurrences in Java repositories, building it 40 % of the complete vulnerabilities recognized,” the examine mentioned.
In JavaScript-centered assignments, prototype air pollution emerged as the major shortcoming with 343,332 occurrences. Denial-of-services (DoS) flaws contributed to the most in Python and Ruby initiatives with 19,652 and 56,331 occurrences, respectively.
“The threat of vulnerable dependencies disrupting the state of security of software package provide chains is right here to remain,” security researchers Umair Nehri and Vandana Verma Sehgal mentioned. “So, developers should be thorough with the dependencies they use in their tasks and maintain them up-to-day to retain them patched from any acknowledged vulnerabilities.”
Identified this posting exciting? Adhere to us on Twitter and LinkedIn to study more distinctive content material we article.
Some parts of this short article are sourced from:
thehackernews.com

 Instagram’s Twitter Alternative ‘Threads’ Launch Halted in Europe Over Privacy Concerns
Instagram’s Twitter Alternative ‘Threads’ Launch Halted in Europe Over Privacy Concerns