The North Korea-connected ScarCruft team has been attributed to a beforehand undocumented backdoor referred to as Dolphin that the danger actor has applied from targets found in its southern counterpart.
“The backdoor […] has a large vary of spying capabilities, together with checking drives and portable devices and exfiltrating data files of interest, keylogging and taking screenshots, and thieving credentials from browsers,” ESET researcher Filip Jurčacko said in a new report printed right now.
Dolphin is reported to be selectively deployed, with the malware using cloud products and services like Google Drive for information exfiltration as properly as command-and-command.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The Slovak cybersecurity corporation claimed it observed the implant deployed as a last-phase payload as portion of a watering gap attack in early 2021 directed versus a South Korean digital newspaper.
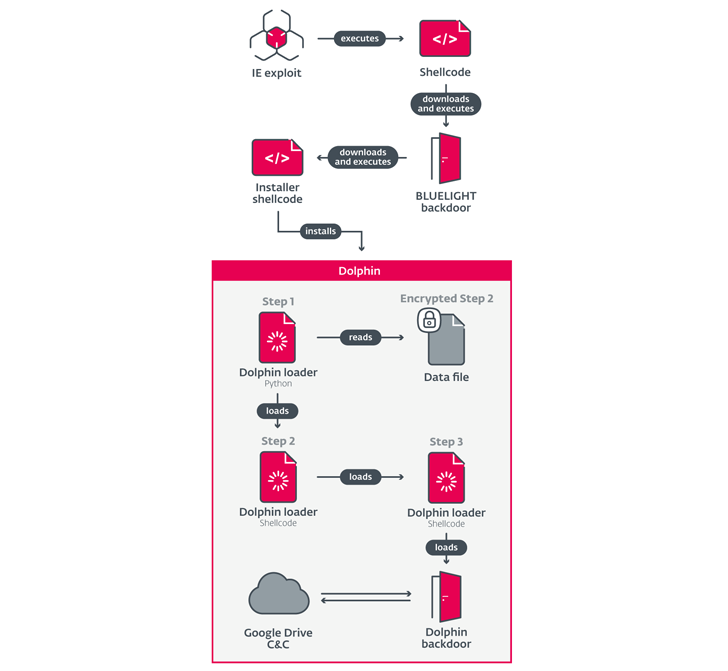
The marketing campaign, very first uncovered by Kaspersky and Volexity past year, entailed the weaponization of two Internet Explorer flaws (CVE-2020-1380 and CVE-2021-26411) to drop a backdoor named BLUELIGHT.
ScarCruft, also referred to as APT37, InkySquid, Reaper, and Ricochet Chollima, is a geo-political enthusiastic APT group that has a monitor document of attacking federal government entities, diplomats, and news organizations affiliated with North Korean affairs. It’s been regarded to be energetic since at minimum 2012.
Previously this April, cybersecurity business Stairwell disclosed specifics of a spear-phishing attack concentrating on journalists masking the region with the top intention of deploying a malware dubbed GOLDBACKDOOR that shares overlaps with yet another ScarCruft backdoor named BLUELIGHT.
The newest conclusions from ESET lose gentle on a second, much more complex backdoor sent to a little pool of victims by way of BLUELIGHT, indicative of a remarkably-targeted espionage procedure.
This, in switch, is realized by executing an installer shellcode that activates a loader comprising a Python and shellcode element, the latter of which operates another shellcode loader to fall the backdoor.
“Whilst the BLUELIGHT backdoor performs primary reconnaissance and analysis of the compromised machine right after exploitation, Dolphin is far more advanced and manually deployed only from selected victims,” Jurčacko described.
What tends to make Dolphin a large amount additional powerful than BLUELIGHT is its skill to look for detachable devices and exfiltrate information of curiosity, these kinds of as media, documents, e-mail, and certificates.
The backdoor, since its unique discovery in April 2021, is claimed to have undergone a few successive iterations that come with its have established of characteristic improvements and grant it much more detection evasion capabilities.
“Dolphin is yet another addition to ScarCruft’s comprehensive arsenal of backdoors abusing cloud storage expert services,” Jurčacko stated. “1 unusual capability uncovered in prior variations of the backdoor is the skill to modify the options of victims’ Google and Gmail accounts to lower their security, presumably in buy to retain account accessibility for the danger actors.”
Uncovered this post attention-grabbing? Follow THN on Fb, Twitter and LinkedIn to go through much more special articles we put up.
Some areas of this short article are sourced from:
thehackernews.com


 How to elevate cyber security needs to be a board-level issue
How to elevate cyber security needs to be a board-level issue