A new North Korean country-state cyber operator has been attributed to a series of strategies orchestrated to assemble strategic intelligence that aligns with Pyongyang’s geopolitical passions given that 2018.
Google-owned Mandiant, which is tracking the activity cluster below the moniker APT43, stated the group’s motives are both espionage- and economically-motivated, leveraging tactics like credential harvesting and social engineering.
The financial angle to its attack strategies is an try on the aspect of the menace actor to crank out funds to fulfill its “most important mission of accumulating strategic intelligence.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Victimology patterns suggest that concentrating on is targeted on South Korea, the U.S., Japan, and Europe, spanning authorities, training, investigate, plan institutes, small business solutions, and manufacturing sectors.
The menace actor was also noticed straying off study course by hanging wellbeing-relevant verticals and pharma companies from Oct 2020 as a result of October 2021, underscoring its capacity to quickly modify priorities.
“APT43 is a prolific cyber operator that supports the interests of the North Korean routine,” Mandiant scientists claimed in a specific technological report revealed Tuesday.
“The group combines reasonably-innovative technological capabilities with aggressive social engineering ways, particularly from South Korean and U.S.-based mostly governing administration organizations, teachers, and feel tanks concentrated on Korean peninsula geopolitical issues.”
APT43’s activities are claimed to align with the Reconnaissance Typical Bureau (RGB), North Korea’s international intelligence company, indicating tactical overlaps with an additional hacking team dubbed Kimsuky (aka Black Banshee, Thallium, or Velvet Chollima).
What is a lot more, it has been observed utilizing instruments beforehand related with other subordinate adversarial syndicates within RGB, this kind of as the Lazarus Team (aka TEMP.Hermit).
Attack chains mounted by APT43 require spear-phishing e-mails made up of personalized lures to entice victims. These messages are despatched working with spoofed and fraudulent personas that masquerade as crucial people within the target’s space of expertise to attain their have faith in.
It is really also known to just take edge of call lists stolen from compromised people today to recognize a lot more targets and steal cryptocurrency to fund its attack infrastructure. The stolen digital belongings are then laundered employing hash rental and cloud mining products and services to obscure the forensic trail and transform them into clean cryptocurrency.
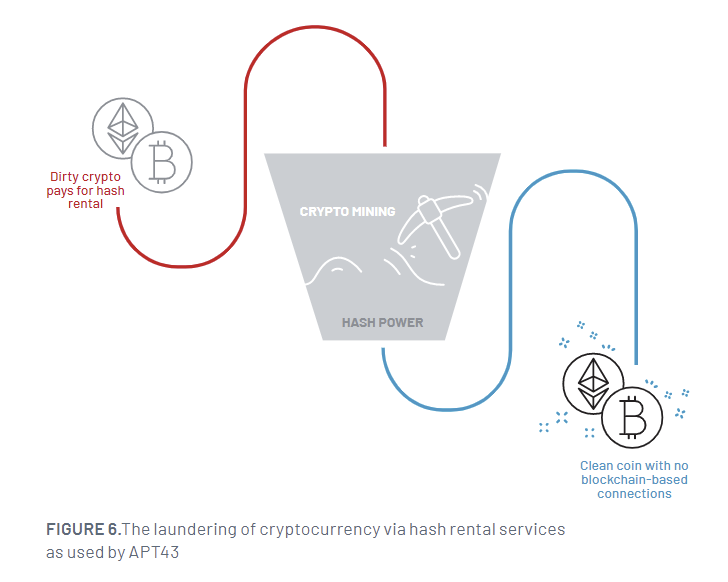
The final aim of the attacks is to facilitate credential selection strategies by way of domains that mimic a wide range of reputable solutions and use the collected info to generate on line personas.
“The prevalence of monetarily-inspired action amongst North Korean teams, even amid these which have traditionally targeted on cyber espionage, suggests a popular mandate to self-fund and an expectation to maintain themselves without having added resourcing,” Mandiant reported.
APT43’s operations are actualized by a significant arsenal of custom made and publicly accessible malware these kinds of as LATEOP (aka BabyShark), FastFire, gh0st RAT, Quasar RAT, Amadey, and an Android variation of a Windows-based mostly downloader named PENCILDOWN.
WEBINARDiscover the Hidden Risks of Third-Party SaaS Applications
Are you knowledgeable of the threats connected with third-party application accessibility to your company’s SaaS apps? Join our webinar to master about the styles of permissions staying granted and how to lessen risk.
RESERVE YOUR SEAT
The findings arrive much less than a 7 days right after German and South Korean authorities organizations warned about cyber attacks mounted by Kimsuky employing rogue browser extensions to steal users’ Gmail inboxes.
“APT43 is very responsive to the needs of Pyongyang’s management,” the menace intelligence business explained, noting the group “maintains a superior tempo of action.”
“Whilst spear-phishing and credential assortment in opposition to federal government, military services, and diplomatic corporations have been main taskings for the group, APT43 finally modifies its targeting and ways, techniques and treatments to go well with its sponsors, such as carrying out financially-enthusiastic cybercrime as wanted to guidance the regime.”
Uncovered this post fascinating? Observe us on Twitter and LinkedIn to read far more unique articles we post.
Some elements of this article are sourced from:
thehackernews.com


 Microsoft Introduces GPT-4 AI-Powered Security Copilot Tool to Empower Defenders
Microsoft Introduces GPT-4 AI-Powered Security Copilot Tool to Empower Defenders