Lazarus Team, the notorious hacking group with ties to the North Korean routine, has unleashed a new multi-platform malware framework with an goal to infiltrate corporate entities all over the globe, steal consumer databases, and distribute ransomware.
Able of targeting Windows, Linux, and macOS functioning techniques, the MATA malware framework — so-called simply because of the authors’ reference to the infrastructure as “MataNet” — arrives with a large assortment of attributes built to carry out a range of destructive functions on infected equipment.
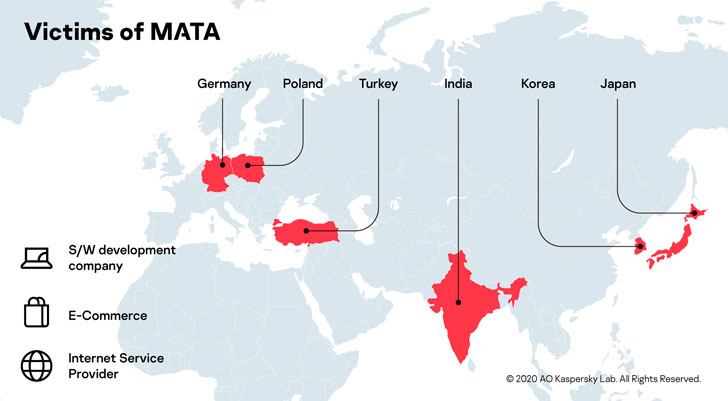
The MATA marketing campaign is said to have begun as early as April of 2018, with the victimology traced to unnamed corporations in software package progress, e-commerce and internet support company sectors positioned in Poland, Germany, Turkey, Korea, Japan, and India, cybersecurity business Kaspersky reported in its Wednesday investigation.
The report features a complete seem at the MATA framework, though also building on previous evidence gathered by scientists from Netlab 360, Jamf, and Malwarebytes more than the earlier eight months.
Last December, Netlab 360 disclosed a completely purposeful remote administration Trojan (RAT) termed Dacls focusing on both Windows and Linux platforms that shared essential infrastructure with that operated by the Lazarus Group.
Then in May well, Jamf and Malwarebytes uncovered a macOS variant of Dacls RAT that was dispersed via a trojanized two-factor authentication (2FA) app.
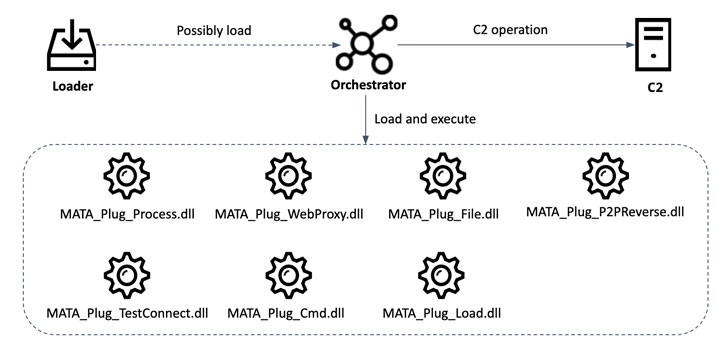
In the newest development, the Windows version of MATA consists of a loader utilised to load an encrypted subsequent-stage payload — an orchestrator module (“lsass.exe”) capable of loading 15 supplemental plugins at the exact time and executing them in memory.
The plugins on their own are attribute-abundant, boasting options that allow for the malware to manipulate files and process processes, inject DLLs, and make an HTTP proxy server.
MATA plugins also permit hackers to target Linux-based diskless network products these kinds of as routers, firewalls or IoT products, and macOS methods by masquerading as a 2FA application known as TinkaOTP, which is based on an open up-resource two-element authentication application named MinaOTP.
At the time the plugins have been deployed, the hackers then experimented with to find the compromised company’s databases and execute several databases queries to acquire customer facts. It really is not right away clear if they were successful in their attempts. Additionally, Kaspersky researchers stated MATA was used to distribute VHD ransomware to a person anonymous sufferer.
Kaspersky reported it linked MATA to the Lazarus Team based on the special file name structure identified in the orchestrator (“c_2910.cls” and “k_3872.cls”), which has been previously seen in many variants of the Manuscrypt malware.
The point out-sponsored Lazarus Team (also termed Hidden Cobra or APT38) has been linked to a lot of big cyber offensives, including the Sony Pics hack in 2014, the SWIFT banking hack in 2016, and the WannaCry ransomware infection in 2017.
Most recently, the APT additional web skimming to their repertoire, focusing on the U.S. and European e-commerce web sites to plant JavaScript-based payment skimmers.
The hacking crew’s penchant for carrying out financially inspired assaults led the U.S. Treasury to sanction the team and its two off-shoots, Bluenoroff and Andariel, final September.
Uncovered this report intriguing? Stick to THN on Fb, Twitter and LinkedIn to read through a lot more unique written content we write-up.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount


 Hackers Steal Transfer Fees, Cripple Soccer Stadiums
Hackers Steal Transfer Fees, Cripple Soccer Stadiums