The Lazarus Group threat actor has been observed leveraging pretend cryptocurrency apps as a entice to provide a formerly undocumented model of the AppleJeus malware, in accordance to new results from Volexity.
“This action notably involves a marketing campaign probable concentrating on cryptocurrency people and businesses with a variant of the AppleJeus malware by way of destructive Microsoft Office environment paperwork,” researchers Callum Roxan, Paul Rascagneres, and Robert Jan Mora mentioned.
The North Korean authorities is identified to adopt a 3-pronged technique by utilizing destructive cyber activity developed to gather intelligence, conduct attacks, and create illicit income for the sanctions strike nation. The threats are collectively tracked beneath the identify Lazarus Group (aka Concealed Cobra or Zinc).

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

“North Korea has done cyber theft from money establishments and cryptocurrency exchanges worldwide, potentially stealing hundreds of tens of millions of pounds, almost certainly to fund government priorities, such as its nuclear and missile plans,” per the 2021 Yearly Danger Evaluation introduced by U.S. intelligence organizations.
Earlier this April, the Cybersecurity and Infrastructure Security Company (CISA) warned of an exercise cluster dubbed TraderTraitor that targets cryptocurrency exchanges and trading companies as a result of trojanized crypto apps for Windows and macOS.
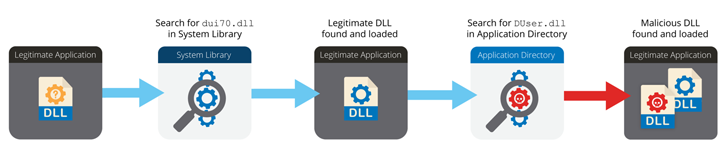
Whilst the TraderTraitor attacks culminate in the deployment of the Manuscrypt distant access trojan, the new action helps make use of a meant crypto investing site named BloxHolder, a copycat of the respectable HaasOnline system, to provide AppleJeus through an installer file.
AppleJeus, 1st documented by Kaspersky in 2018, is intended to harvest information about the contaminated system (i.e., MAC tackle, laptop or computer title, and working method version) and obtain shellcode from a command-and-control (C2) server.
The attack chain is claimed to have undergone a slight deviation in Oct 2022, with the adversary shifting from MSI installer documents to a booby-trapped Microsoft Excel doc that takes advantage of macros to down load a remotely hosted payload, a PNG graphic, from OpenDrive.
The plan behind the change is probably to lessen static detection by security items, Volexy stated, introducing it could not attain the impression file (“Qualifications.png”) from the OpenDrive website link but pointed out it embeds a few information, which includes an encoded payload that’s subsequently extracted and introduced on the compromised host.
“The Lazarus Team proceeds its energy to concentrate on cryptocurrency users, even with ongoing interest to their strategies and strategies,” the scientists concluded.
Identified this article intriguing? Comply with us on Twitter and LinkedIn to study a lot more exceptional material we write-up.
Some sections of this report are sourced from:
thehackernews.com


 Microsoft: Beware Russian Winter Cyber-Offensive
Microsoft: Beware Russian Winter Cyber-Offensive