A set of fake npm deals learned on the Node.js repository has been discovered to share ties with North Korean state-sponsored actors, new findings from Phylum present.
The deals are named execution-time-async, data-time-utils, login-time-utils, mongodb-link-utils, and mongodb-execution-utils.
A person of the offers in concern, execution-time-async, masquerades as its respectable counterpart execution-time, a library with additional than 27,000 weekly downloads. Execution-time is a Node.js utility utilized to measure execution time in code.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
It “basically installs quite a few destructive scripts including a cryptocurrency and credential stealer,” Phylum stated, describing the marketing campaign as a software package provide chain attack concentrating on computer software builders. The deal was downloaded 302 instances since February 4, 2024, in advance of being taken down.

In an attention-grabbing twist, the danger actors created endeavours to conceal the obfuscated malicious code in a exam file, which is built to fetch upcoming-stage payloads from a distant server, steal credentials from web browsers like Courageous, Google Chrome, and Opera, and retrieve a Python script, which, in transform, downloads other scripts –
- ~/.n2/fork out, which can run arbitrary commands, obtain and launch ~/.n2/bow and ~/.n2/adc, terminate Brave and Google Chrome, and even delete alone
- ~/.n2/bow, which is a Python-centered browser password stealer
- ~/.n2/adc, which installs AnyDesk on Windows
Phylum reported it identified feedback in the supply code (“/People/ninoacuna/”) that built it possible to monitor down a now-deleted GitHub profile with the exact identify (“Nino Acuna” or binaryExDev) containing a repository termed File-Uploader.
Present inside the repository ended up Python scripts referencing the same IP addresses (162.218.114[.]83 – subsequently modified to 45.61.169[.]99) applied to fetch the aforementioned Python scripts.

It’s suspected that the attack is a do the job in development, as at least 4 extra packages with similar attributes have made their way to the npm bundle repository, attracting a complete of 325 downloads –
- info-time-utils – 52 downloads starting off from February 15
- login-time-utils – 171 downloads starting from February 15
- mongodb-connection-utils – 51 downloads starting up from February 19
- mongodb-execution-utils – 51 downloads starting from February 19
Connections to North Korean Actors Arise
Phylum, which also analyzed the two GitHub accounts that binaryExDev follows, uncovered an additional repository recognised as mave-finance-org/auth-playground, which has been forked no fewer than a dozen situations by other accounts.
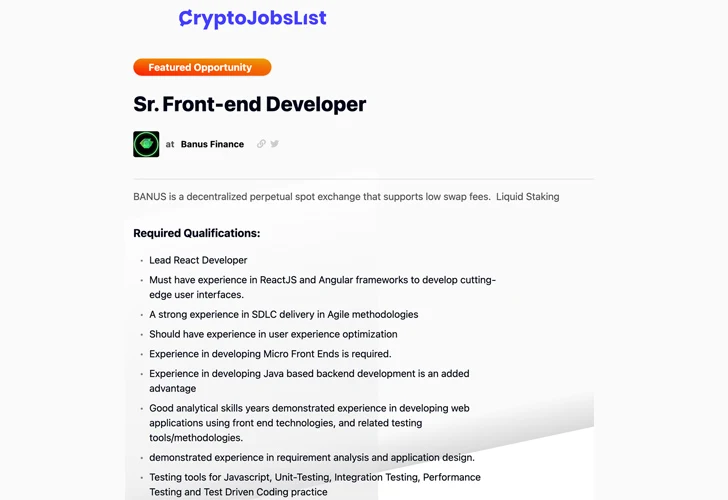
Though forking a repository in itself isn’t really abnormal, an abnormal factor of some of these forked repositories were being that they were renamed as “auth-demo” or “auth-obstacle,” raising the risk that the first repository may well have been shared as aspect of a coding test for a job job interview.
The repository was later moved to banus-finance-org/auth-sandbox, Dexbanus-org/are living-coding-sandbox, and mave-finance/subsequent-evaluation, indicating tries to actively get about GitHub’s takedown tries. All these accounts have been taken off.

What is actually much more, the following-assessment deal was observed to comprise a dependency “json-mock-config-server” that’s not stated on the npm registry, but rather served right from the area npm.mave[.]finance.
It really is value noting that Banus promises to be a decentralized perpetual location exchange based in Hong Kong, with the firm even posting a career option for a senior frontend developer on February 21, 2024. It’s presently not very clear if this is a authentic occupation opening or if it is really an elaborate social engineering scheme.
The connections to North Korean risk actors appear from the point that the obfuscated JavaScript embedded in the npm bundle overlaps with a further JavaScript-based malware dubbed BeaverTail that is propagated by way of npm offers. The campaign was codenamed Contagious Job interview by Palo Alto Networks Unit 42 in November 2023.
Contagious Job interview is a very little various from Operation Dream Task – which is linked to the Lazarus Team – in that it is largely focused on targeting developers by way of faux identities in freelance job portals to trick them into installing rogue npm packages, Michael Sikorski, vice president and CTO of Palo Alto Networks Device 42, instructed The Hacker News at the time.
One particular of the builders who fell victim to the campaign has since confirmed to Phylum that the repository is shared below the guise of a are living coding job interview, although they claimed they by no means installed it on their method.
“A lot more than ever, it is critical for both of those particular person builders as very well as software package development corporations to stay vigilant against these attacks in open-resource code,” the corporation stated.
Found this short article attention-grabbing? This post is a contributed piece from one particular of our valued partners. Stick to us on Twitter and LinkedIn to browse far more unique information we write-up.
Some parts of this post are sourced from:
thehackernews.com


 Three Tips to Protect Your Secrets from AI Accidents
Three Tips to Protect Your Secrets from AI Accidents