Media companies and high-profile professionals in North Korean affairs have been at the acquiring conclusion of a new campaign orchestrated by a danger actor acknowledged as ScarCruft in December 2023.
“ScarCruft has been experimenting with new an infection chains, such as the use of a complex threat analysis report as a decoy, most likely focusing on consumers of threat intelligence like cybersecurity pros,” SentinelOne scientists Aleksandar Milenkoski and Tom Hegel explained in a report shared with The Hacker News.
The North Korea-joined adversary, also acknowledged by the identify APT37, InkySquid, RedEyes, Ricochet Chollima, and Ruby Sleet, is assessed to be section of the Ministry of Condition Security (MSS), putting it aside from Lazarus Team and Kimsuky, which are things within the Reconnaissance Basic Bureau (RGB).

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The team is regarded for its concentrating on of governments and defectors, leveraging spear-phishing lures to produce RokRAT and other backdoors with the greatest aim of covert intelligence gathering in pursuit of North Korea’s strategic interests.
In August 2023, ScarCruft was linked to an attack on Russian missile engineering company NPO Mashinostroyeniya along with Lazarus Team in what has been deemed as a “very appealing strategic espionage mission” created to advantage its controversial missile software.
Previously this week, North Korean condition media described that the state experienced carried out a test of its “underwater nuclear weapons procedure” in response to drills by the U.S., South Korea, and Japan, describing the workout routines as a risk to its nationwide security.
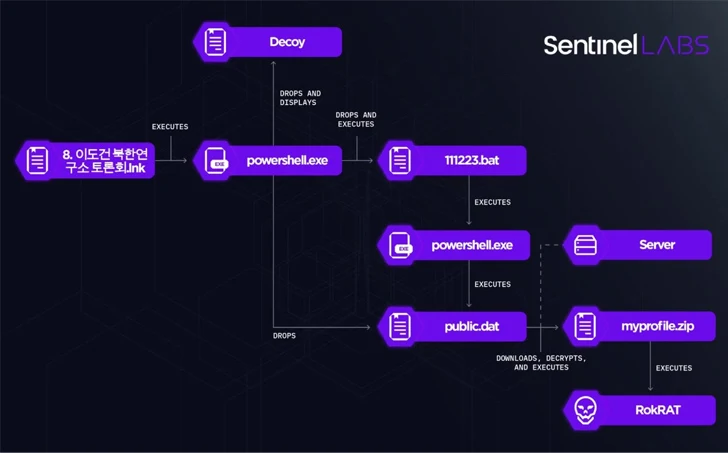
The latest attack chain observed by SentinelOne qualified an skilled in North Korean affairs by posing as a member of the North Korea Study Institute, urging the recipient to open up a ZIP archive file containing presentation elements.
Whilst seven of the nine information in the archive are benign, two of them are malicious Windows shortcut (LNK) files, mirroring a multi-stage infection sequence earlier disclosed by Check Position in May 2023 to distribute the RokRAT backdoor.
There is proof to suggest that some of the people who were focused all-around December 13, 2023, had been also formerly singled out a thirty day period prior on November 16, 2023.
SentinelOne claimed its investigation also uncovered malware – two LNK documents (“inteligence.lnk” and “news.lnk”) as properly as shellcode variants providing RokRAT – which is reported to be portion of the threat actor’s arranging and testing procedures.

While the previous shortcut file just opens the reputable Notepad application, the shellcode executed through information.lnk paves the way for the deployment of RokRAT, while this infection course of action is but to be observed in the wild, indicating its very likely use for long term strategies.
The progress is a indication that the nation-condition hacking crew is actively tweaking its modus operandi possible in an effort to circumvent detection in response to community disclosure about its methods and methods.
“ScarCruft remains dedicated to acquiring strategic intelligence and maybe intends to obtain insights into non-community cyber menace intelligence and protection strategies,” the researchers explained.
“This enables the adversary to attain a much better knowledge of how the global community perceives developments in North Korea, thus contributing to North Korea’s choice-producing processes.”
Uncovered this report interesting? Observe us on Twitter and LinkedIn to study far more exceptional content material we article.
Some parts of this report are sourced from:
thehackernews.com


 MavenGate Attack Could Let Hackers Hijack Java and Android via Abandoned Libraries
MavenGate Attack Could Let Hackers Hijack Java and Android via Abandoned Libraries