The North Korea-joined menace actor tracked as APT37 has been joined to a piece of new malware dubbed M2RAT in attacks targeting its southern counterpart, suggesting ongoing evolution of the group’s functions and ways.
APT37, also tracked below the monikers Reaper, RedEyes, Ricochet Chollima, and ScarCruft, is linked to North Korea’s Ministry of Point out Security (MSS) contrary to the Lazarus and Kimsuky threat clusters that are portion of the Reconnaissance Common Bureau (RGB).
In accordance to Google-owned Mandiant, MSS is tasked with “domestic counterespionage and overseas counterintelligence things to do,” with APT37’s attack strategies reflective of the agency’s priorities. The operations have traditionally singled out people today this sort of as defectors and human rights activists.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“APT37’s assessed major mission is covert intelligence collecting in support of DPRK’s strategic armed service, political, and economic pursuits,” the risk intelligence organization reported.
The threat actor is identified to rely on personalized equipment these kinds of as Chinotto, RokRat, BLUELIGHT, GOLDBACKDOOR, and Dolphin to harvest delicate info from compromised hosts.
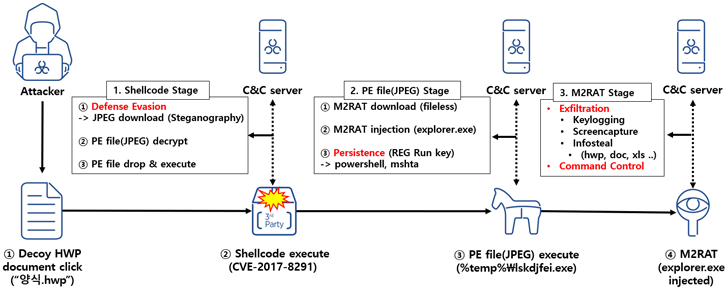
“The principal element of this RedEyes Team attack circumstance is that it employed a Hangul EPS vulnerability and employed steganography approaches to distribute destructive codes,” AhnLab Security Emergency reaction Heart (ASEC) mentioned in a report posted Tuesday.
The infection chain noticed in January 2023 commences with a decoy Hangul document, which exploits a now-patched flaw in the term processing software program (CVE-2017-8291) to set off shellcode that downloads an graphic from a remote server.
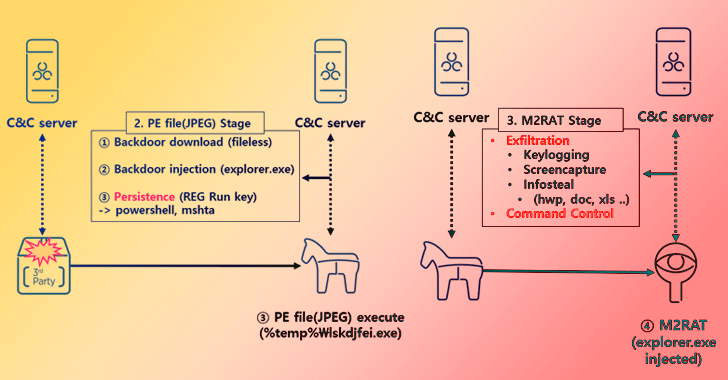
The JPEG file makes use of steganographic methods to conceal a moveable executable that, when launched, downloads the M2RAT implant and injects it into the reputable explorer.exe procedure.
When persistence is realized by usually means of a Windows Registry modification, M2RAT functions as a backdoor able of keylogging, screen seize, method execution, and info theft. Like Dolphin, it really is also designed to siphon facts from removable disks and related smartphones.
“These APT attacks are pretty complicated to defend against, and the RedEyes team in particular is recognized to generally goal people today, so it can be complicated for non-company people today to even figure out the hurt,” ASEC mentioned.
This is not the initial time CVE-2017-8291 has been weaponized by North Korean menace actors. In late 2017, the Lazarus Team was observed concentrating on South Korean cryptocurrency exchanges and customers to deploy Destover malware, according to Recorded Foreseeable future.
Found this post exciting? Follow us on Twitter and LinkedIn to read through extra exclusive material we write-up.
Some pieces of this posting are sourced from:
thehackernews.com

 Webinar — A MythBusting Special: 9 Myths about File-based Threats
Webinar — A MythBusting Special: 9 Myths about File-based Threats